Data access control method, device, proxy server and medium based on web API
A data access control and data access technology, applied in the computer field, can solve the problems of data security reduction, data desensitization, etc., and achieve the effect of improving data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
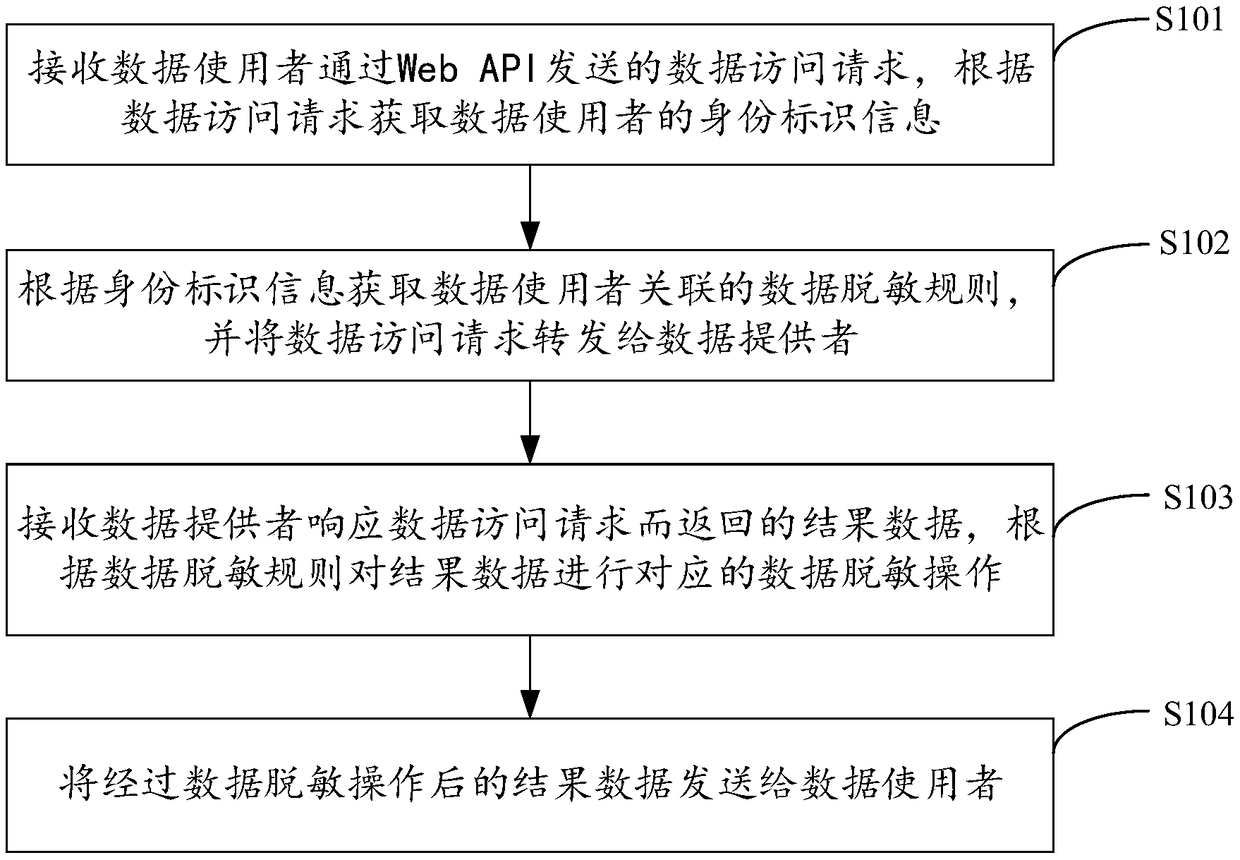
[0025] figure 1 The implementation flow of the Web API-based data access control method provided by Embodiment 1 of the present invention is shown. For the convenience of description, only the parts related to the embodiment of the present invention are shown, and the details are as follows:
[0026] In step S101, the data access request sent by the data user through the Web API is received, and the identity information of the data user is obtained according to the data access request.
[0027] The embodiment of the present invention is applicable to a data provider providing network service through Web API, especially to a proxy server of the data provider, so as to guarantee the response efficiency of network service while ensuring data privacy and security. The data access request is a Web API request, and the data user can be a program, application, service or user client that uses the Web API data access method, and the identification information can be the user name / pass...
Embodiment 2
[0038] image 3 The structure of the Web API-based data access control device provided by the second embodiment of the present invention is shown. For the convenience of description, only the parts related to the embodiment of the present invention are shown, including:
[0039] The identity information obtaining unit 31 is used to receive the data access request sent by the data user through the Web API, and obtain the identity information of the data user according to the data access request;
[0040] The request forwarding unit 32 is configured to obtain the data desensitization rules associated with the data user according to the identity information, and forward the data access request to the data provider;
[0041] The data desensitization unit 33 is configured to receive the result data returned by the data provider in response to the data access request, and perform a corresponding data desensitization operation on the result data according to the data desensitization ...
Embodiment 3
[0052] Figure 4 The structure of the proxy server provided by the third embodiment of the present invention is shown, and for the convenience of description, only the parts related to the embodiment of the present invention are shown.
[0053] The proxy server 4 in the embodiment of the present invention includes a processor 40 , a memory 41 and a computer program 42 stored in the memory 41 and operable on the processor 40 . When the processor 40 executes the computer program 42, the steps in the above-mentioned method embodiments are realized, for example figure 1 Steps S101 to S104 are shown. Alternatively, when the processor 40 executes the computer program 42, the functions of the units in the above-mentioned device embodiments are realized, for example image 3 Function of units 31 to 34 shown.
[0054] When the processor 40 of the proxy server 4 in the embodiment of the present invention executes the computer program 42, it receives the data access request sent by th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com