Diameter flooding attack detection device and method
A flood attack and detection device technology, applied in the field of communication security, can solve problems such as denial of service, occupation of service and network resources, and decline in service capabilities of related network elements, so as to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
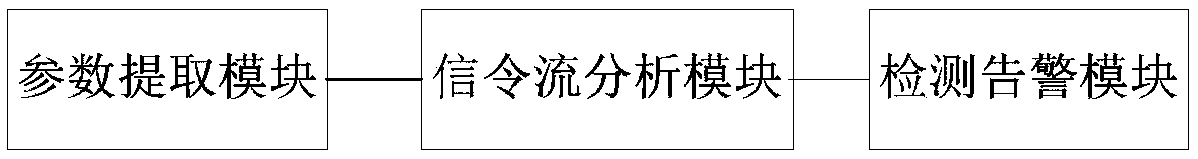
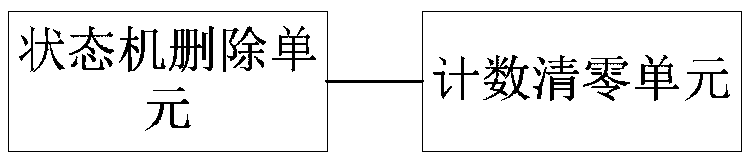
[0040] A Diameter message consists of two parts: a header and a message body. The message header is located at the front end of the message, including the protocol version, message length, command code, application ID, hop-by-hop identifier and end-to-end identifier, see the attached Figure 8 As shown; the message body consists of multiple AVPs, and each AVP is composed of AVP Code, AVP Flag, AVP Length, Vendor-ID and Data, see the attached Figure 8 shown. Since the IMS network is based on an all-IP core network, it has the inherent vulnerability of an IP network. Therefore, it is more vulnerable to various forms of network attacks, especially flooding attacks using the Diameter protocol. Diameter flooding attack...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com