User account login method and apparatus, electronic device and storage medium
A technology for user accounts and login methods, applied in the Internet field, can solve problems such as poor browser compatibility, inability to ensure device security, and poor maintainability, and achieve the effects of convenient and flexible management, protection of fundamental interests, and reduction of the risk of theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0019] figure 1 It is a schematic flow chart of the user account login method in the embodiment of the present invention, and the specific steps are:
[0020] Step 11. After the server side receives the access request sent by the client to access the page, it obtains one or more combinations of the user agent UA field, HTTP header information field, hardware information field, and cookie field in the access request, and calculates The unique identifier of the client device;
[0021] Wherein, since each of the above fields is related to the user's personal usage habits and application environment, when combined together, the user equipment can be effectively distinguished, and can be used as a basis for distinguishing equipment information. Therefore, the purpose of collecting the above fields is to obtain the unique identifier (EID) of the client device. Specifically, the MurmurHash operation (hash function ) and perform hash encryption processing to calculate the unique dev...
Embodiment 2
[0049] The server side receives a reminder message including a malicious account, and the reminder message carries the name of the malicious account and the unique identifier of the client device under the name of the malicious account; according to the reminder message, the unique identifier of the client device under the name of the malicious account will be The login status is deleted. In this way, according to the way of EID kicking people, once a certain device in the common device list is identified to be at risk, the login status information on this device can be directly removed, and the user is forced to log in again to minimize the risk of account theft.
[0050] It should be noted that one account name can correspond to multiple unique identifiers of client devices, and the deleted malicious user refers to one of the unique identifiers of client devices under the account name.
[0051] In the present invention, the malicious account is obtained through the analysis ...
Embodiment 3
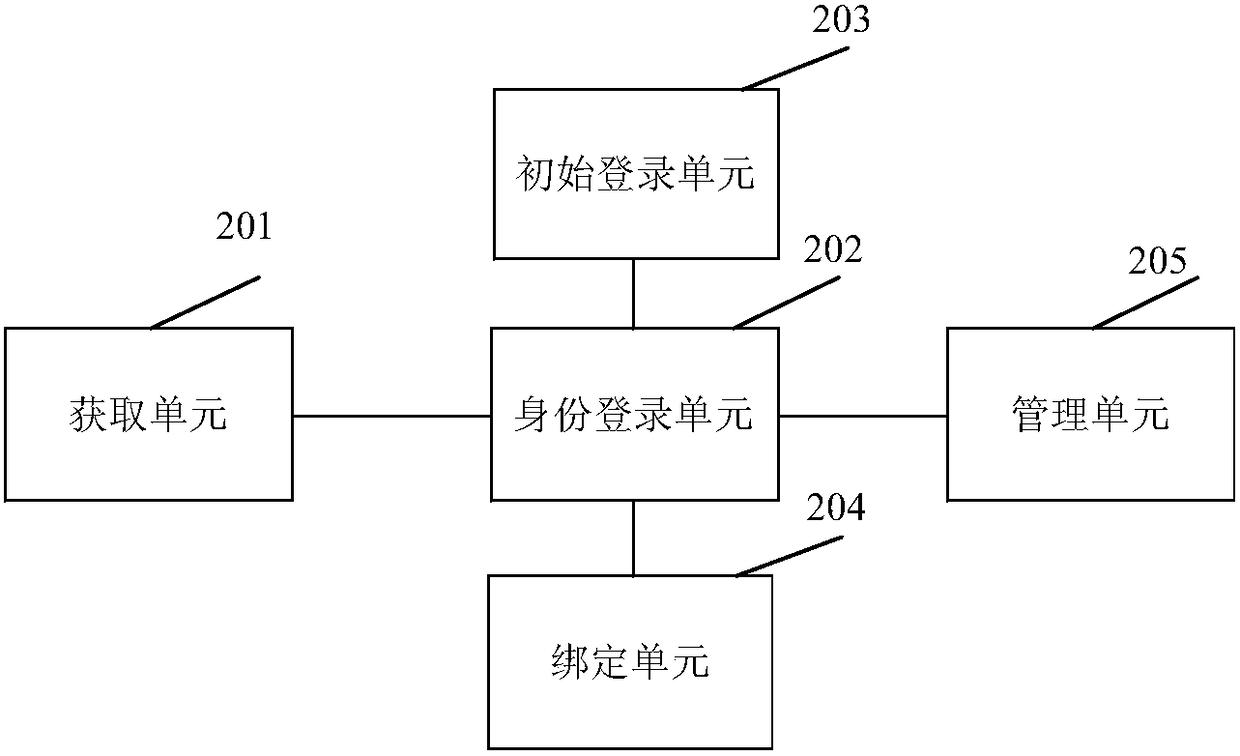
[0060] Based on the same inventive concept, an embodiment of the present application also proposes a user account login device. see figure 2 , figure 2 It is a schematic structural diagram of a device applied to the above technology in the embodiment of the present application. The device includes: an acquisition unit 201, an identity registration unit 202;
[0061] Obtaining unit 201, after receiving the access request of the access page sent by the client, obtains the user agent UA field in the access request, the HTTP header information field, the hardware information field, the combination of one or more of the cookie fields, and calculates the client The unique identifier of the terminal device;
[0062] The identity login unit 202 performs identity login, detects whether the unique identifier of the client device is stored in the common equipment list, if yes, then confirms that the identity login is successful; if not, then performs identity verification according ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com