Trojan horse detection method based on computer memory analysis technology
A technology of memory analysis and detection method, which is applied in the field of Trojan horse detection based on computer memory analysis technology, detection of information security incidents and various computer attack incidents, and can solve problems such as difficulty in finding malicious code, high false alarm rate, and difficulty in detection , to achieve the effect of preventing the influence of Trojan horse detection results and reliable detection results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
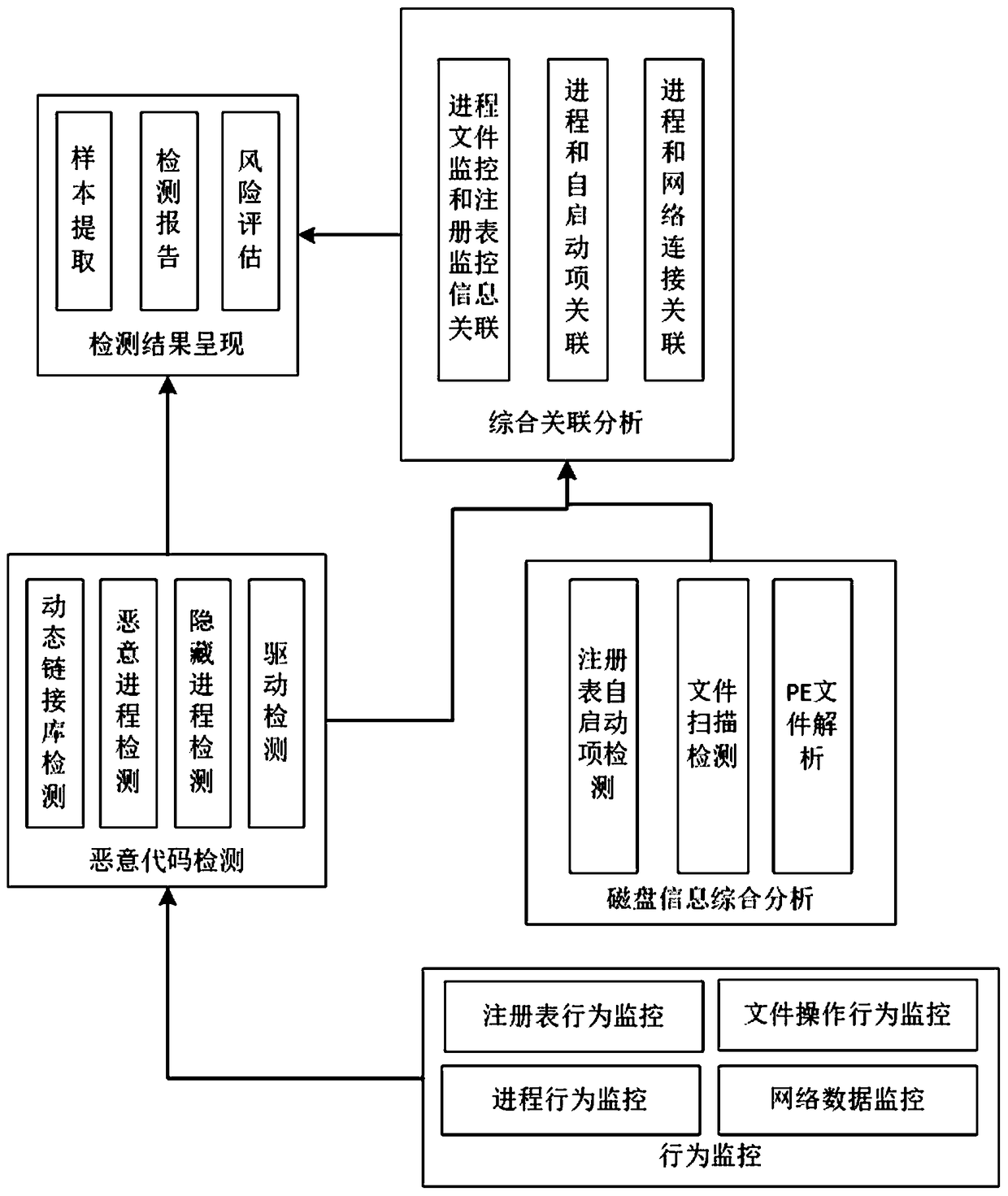
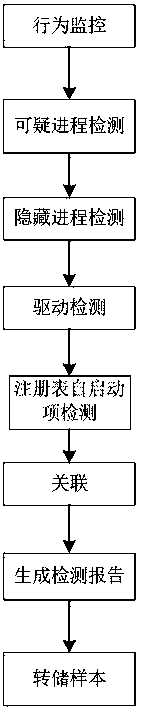
[0051] Such as figure 1 As shown, a schematic diagram of the composition of the Trojan horse detection method based on the computer memory analysis technology of the present invention is provided. The Trojan horse detection method based on the memory analysis technology of the present invention includes behavior monitoring, malicious code detection, comprehensive analysis of disk information, and comprehensive correlation analysis. , The test result presents five parts.
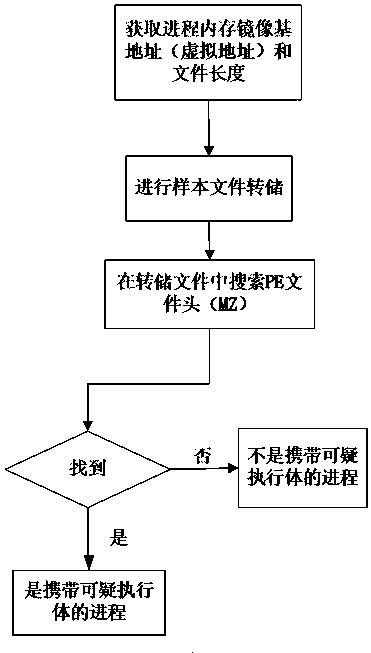
[0052] The behavior monitoring part of the present invention includes four sub-parts: process operation behavior monitoring, registry behavior monitoring, file operation behavior monitoring, and network data monitoring; the malicious code detection part is based on memory analysis technology detection, including dynamic link library detection, malicious process Detection, hidden proce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com