Graph data publishing privacy protection cluster anonymity method and system
A technology of privacy protection and graph data, which is applied in the direction of digital transmission system, transmission system, data exchange network, etc., can solve the problems of general limitation and achieve the effect of ensuring privacy and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
[0039] like figure 1 As shown, the embodiment of the present invention provides a clustering anonymity method for graph data publishing privacy protection, including:
[0040] Obtaining step S101, taking each user in the graph data group as a node, and obtaining the user attributes of each node and the relationship between users;
[0041] Calculation step S102, calculating the attribute similarity and structural similarity between each node and its adjacent nodes; the attribute similarity is determined by the user attributes of two adjacent nodes, and the structural similarity is determined by the two adjacent nodes The mutual relationship between users is determined;
[0042] Clustering step S103, according to the attribute similarity and structural similarity between each node and its adjacent nodes, the nodes in the group are sequentially divided into attribute clustering and structural clustering to obtain several clusters;
[0043] In the anonymizing step S104, the node...
specific Embodiment 2
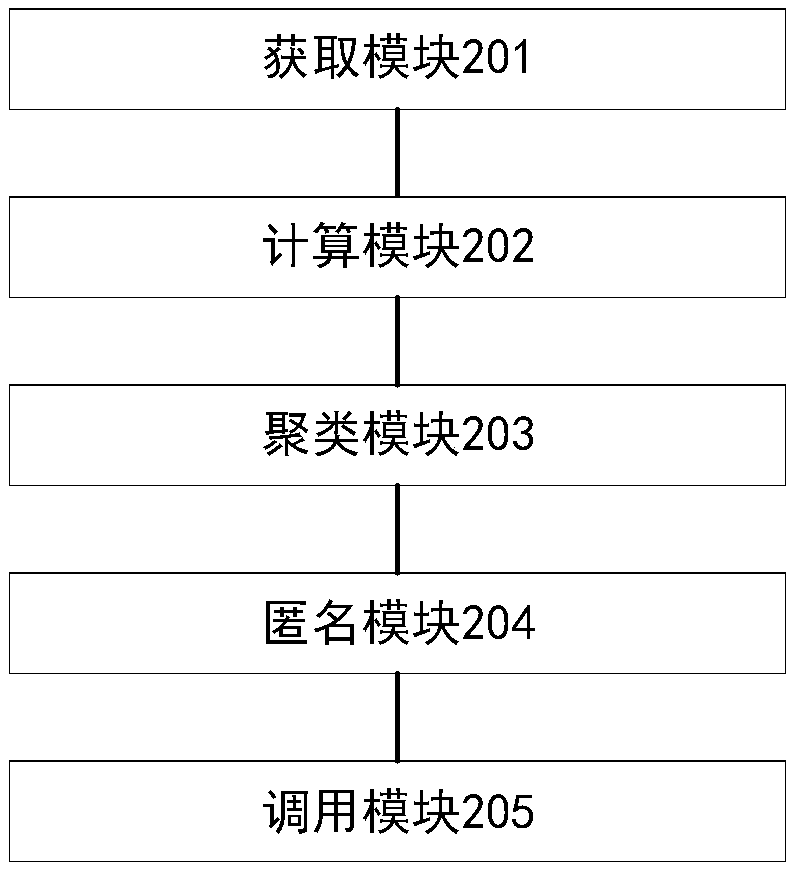
[0050] like figure 2 As shown, the embodiment of the present invention provides a clustering anonymity system for graph data publishing privacy protection, including:
[0051] The obtaining module 201 is used to use each user in the graph data group as a node to obtain the user attributes of each node and the relationship between users;
[0052] The calculation module 202 is used to calculate the attribute similarity and structural similarity between each node and its adjacent nodes; the attribute similarity is determined by the user attributes of two adjacent nodes, and the structural similarity is determined by two related nodes The mutual relationship between users of adjacent nodes is determined;
[0053] The clustering module 203 is used to perform attribute clustering and structural clustering division on the nodes in the group in turn according to the attribute similarity and structural similarity between each node and its adjacent nodes, so as to obtain several clust...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com