CPK-based video monitoring method, system, camera, server and client
A video surveillance and camera technology, applied in the field of video surveillance based on CPK, can solve problems such as exposure of video data in unsafe environments
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
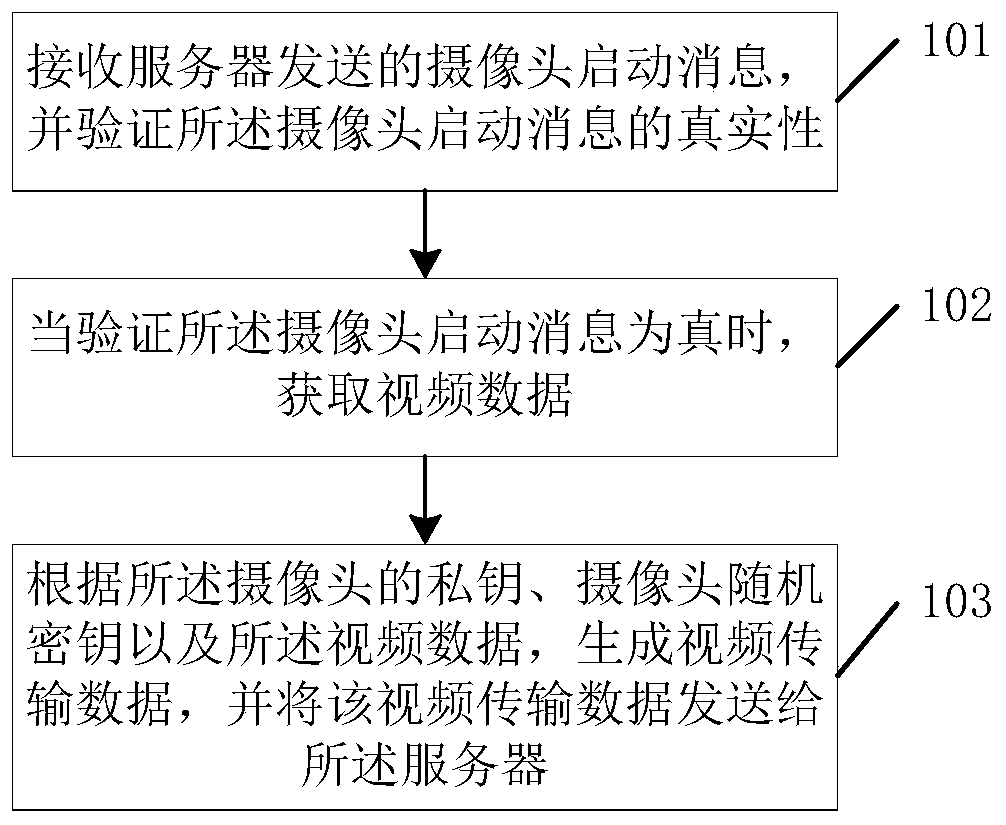
[0042] figure 1 It is a schematic flowchart of a CPK-based video surveillance method provided by an embodiment of the present invention. like figure 1 As shown, the method is applied to a camera, and the method includes:
[0043] Step 101, receiving the camera startup message sent by the server, and verifying the authenticity of the camera startup message, the camera startup message including the authenticity certificate of the server, the authenticity certificate of the camera and the authenticity certificate of the startup instruction ;
[0044] Step 102, when verifying that the camera start message is true, obtain video data; and
[0045] Step 103, generate video transmission data according to the private key of the camera, the random key of the camera and the video data, and send the video transmission data to the server, the video transmission data includes the authenticity of the camera certificate, the authenticity certificate of each positive second key frame in th...
Embodiment 2
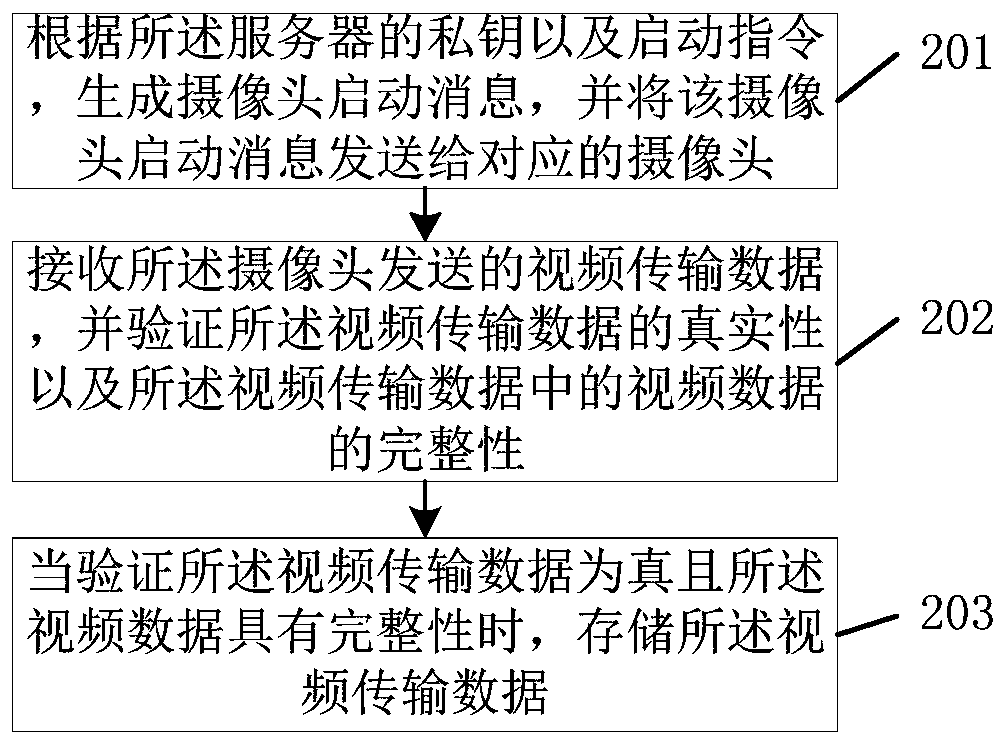
[0056] figure 2 It is a schematic flowchart of another CPK-based video monitoring method provided by an embodiment of the present invention. like figure 2 As shown, the method is applied to the server, and the method includes the following steps:
[0057] Step 201: Generate a camera startup message according to the server's private key and startup instructions, and send the camera startup message to the corresponding camera, where the camera startup message includes the authenticity certificate of the server, the authenticity of the camera Proof of authenticity and proof of authenticity of the activation instruction;
[0058] Step 202, receiving the video transmission data sent by the camera, and verifying the authenticity of the video transmission data and the integrity of the video data in the video transmission data, the video transmission data including the authenticity certificate of the camera , the authenticity certificate of each positive second key frame in the v...
Embodiment 3
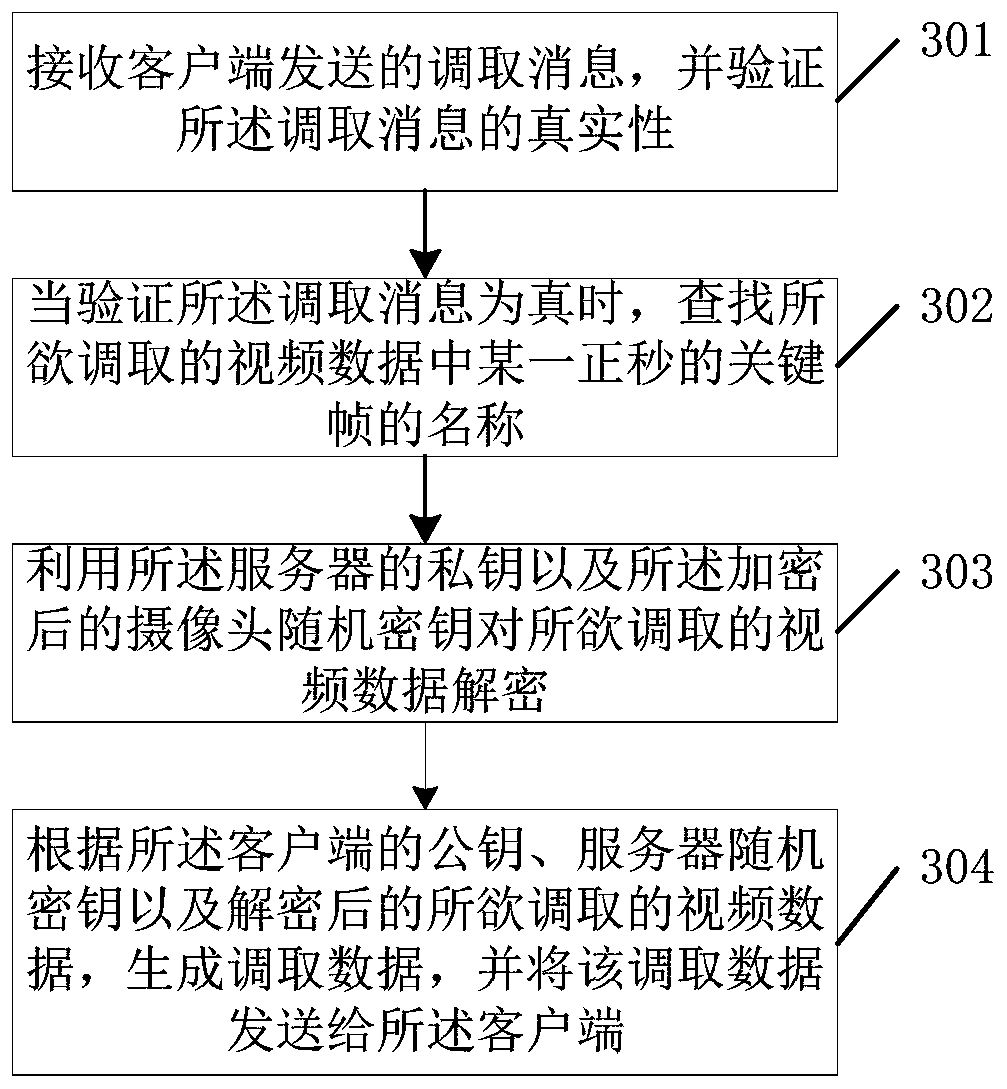
[0085] Figure 4 It is a schematic flowchart of another CPK-based video monitoring method provided by an embodiment of the present invention. like Figure 4 As shown, the method is applied to the client, and the method includes the following steps:
[0086] Step 401, obtaining the name of a key frame of a positive second in the video data to be retrieved and the camera corresponding to the video data to be retrieved;
[0087] Step 402, generate a call message according to the private key of the client, the identification of the camera, and the name of a key frame of a certain positive second in the video data to be called, and send the call message to the server, The calling message includes the authenticity certificate of the client, the authenticity certificate of the camera, and the name of a certain positive-second key frame in the video data to be called;
[0088] Step 403: Receive the call data sent by the server in response to the call message, and verify the authent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com