AES (Advanced Encryption Standard)-based encryption method and device
An encryption method and technology to be encrypted, applied in the field of information security, can solve the problem of weak anti-side channel attack ability, achieve the effect of improving anti-side channel attack ability and increasing data complexity and difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
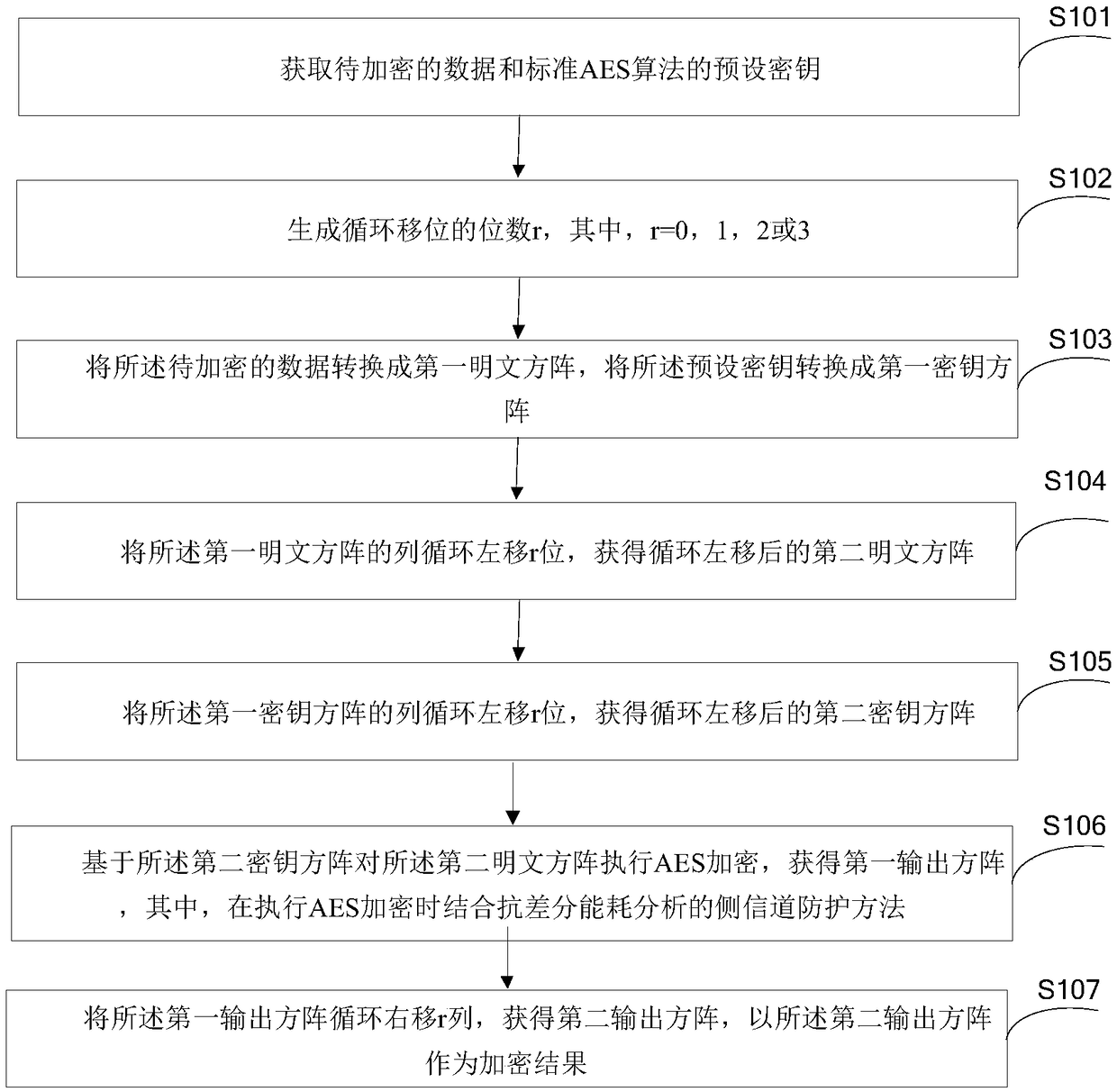
[0055] This embodiment provides an encryption method based on AES, please refer to figure 1 , the method includes:
[0056] Step S101: Obtain the data to be encrypted and the preset key of the standard AES algorithm.
[0057] Specifically, the standard AES algorithm (Advanced Encryption Standard), the packet length of the AES algorithm is 128bit, and the preset key is the key used for the encryption operation of the AES algorithm, which includes the key word (also known as the seed key). In a specific implementation process, the preset key can be converted into a matrix form, and a certain column of the matrix is a key word, for example, a 4*4 matrix includes 4 key words.
[0058] Step S102: Generate the number of bits r for cyclic shift, where r=0, 1, 2 or 3.
[0059] Specifically, a random number generator can be used to generate the number r of the cyclic shift, or a random number can be obtained from a preset random source to generate the number r of the cyclic shift, ...
Embodiment 2
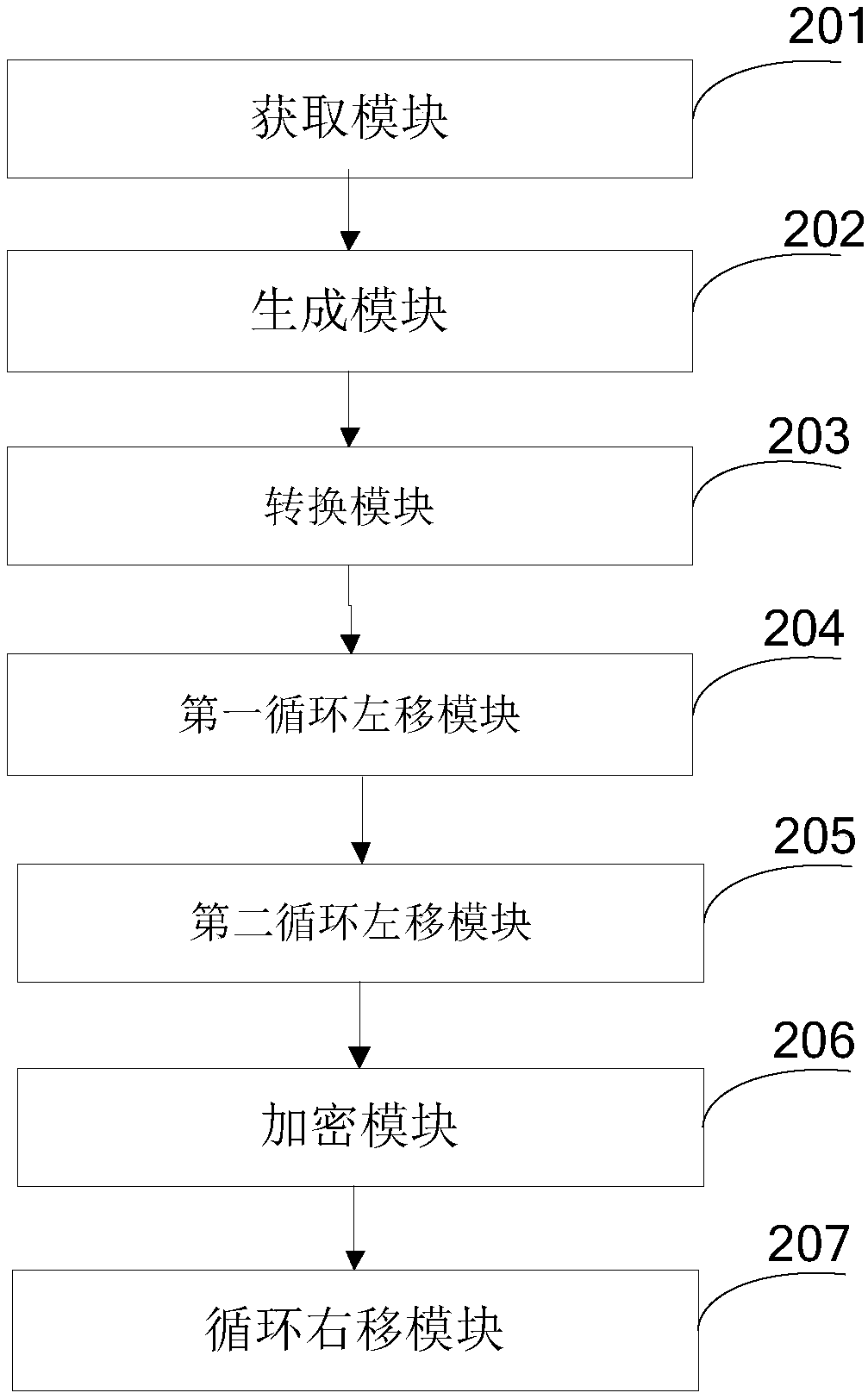
[0115] This embodiment provides an AES-based encryption device, please refer to figure 2 , the device consists of:
[0116] Obtaining module 201, for obtaining the data to be encrypted and the preset key of standard AES algorithm;
[0117] A generating module 202, configured to generate the number of bits r of the cyclic shift, where r=0, 1, 2 or 3;
[0118] A conversion module 203, configured to convert the data to be encrypted into a first plaintext square matrix, and convert the preset key into a first key square matrix;
[0119] The first cyclic left shift module 204 is used to cyclically shift the columns of the first plaintext square matrix to the left by r bits to obtain the second plaintext square matrix after the circular left shift;
[0120] The second cyclic left shift module 205 is used to cyclically shift the column of the first key square matrix to the left by r bits to obtain the second key square matrix after the circular left shift;
[0121] An encryption ...
Embodiment 3
[0137] Based on the same inventive concept, the present application also provides a computer-readable storage medium 300, please refer to image 3 , on which a computer program 311 is stored, and the method in Embodiment 1 is implemented when the program is executed.
[0138] Since the computer-readable storage medium introduced in Embodiment 3 of the present invention is a computer-readable storage medium used to implement the AES-based encryption method in Embodiment 1 of the present invention, based on the method described in Embodiment 1 of the present invention, this Those skilled in the art can understand the specific structure and deformation of the computer-readable storage medium, so details will not be repeated here. All computer-readable storage media used in the method of Embodiment 1 of the present invention belong to the scope of protection of the present invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com