Cluster audit control method based on blockchain technology
A block chain and cluster technology, applied in the field of information technology and computer software, can solve the problems of no cluster audit control and achieve the effect of improving audit efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] Below in conjunction with accompanying drawing, the present invention will be further described through embodiment.
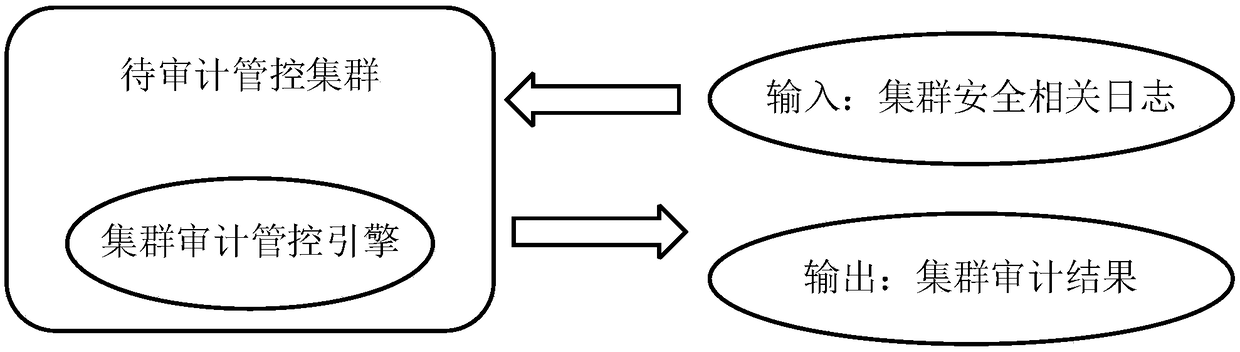
[0024] Such as figure 1 As shown, the cluster audit management and control method based on blockchain technology in this embodiment, the main body is a hardware device, which carries a cluster audit management and control engine, the input of which is the cluster log related to security, and the output is the cluster audit result and the cluster Control information.
[0025] The functions of this embodiment are fully automated, from the audit of the cluster log to the control of the cluster, the whole process is automatically executed by each unit inside the engine, without manual intervention.
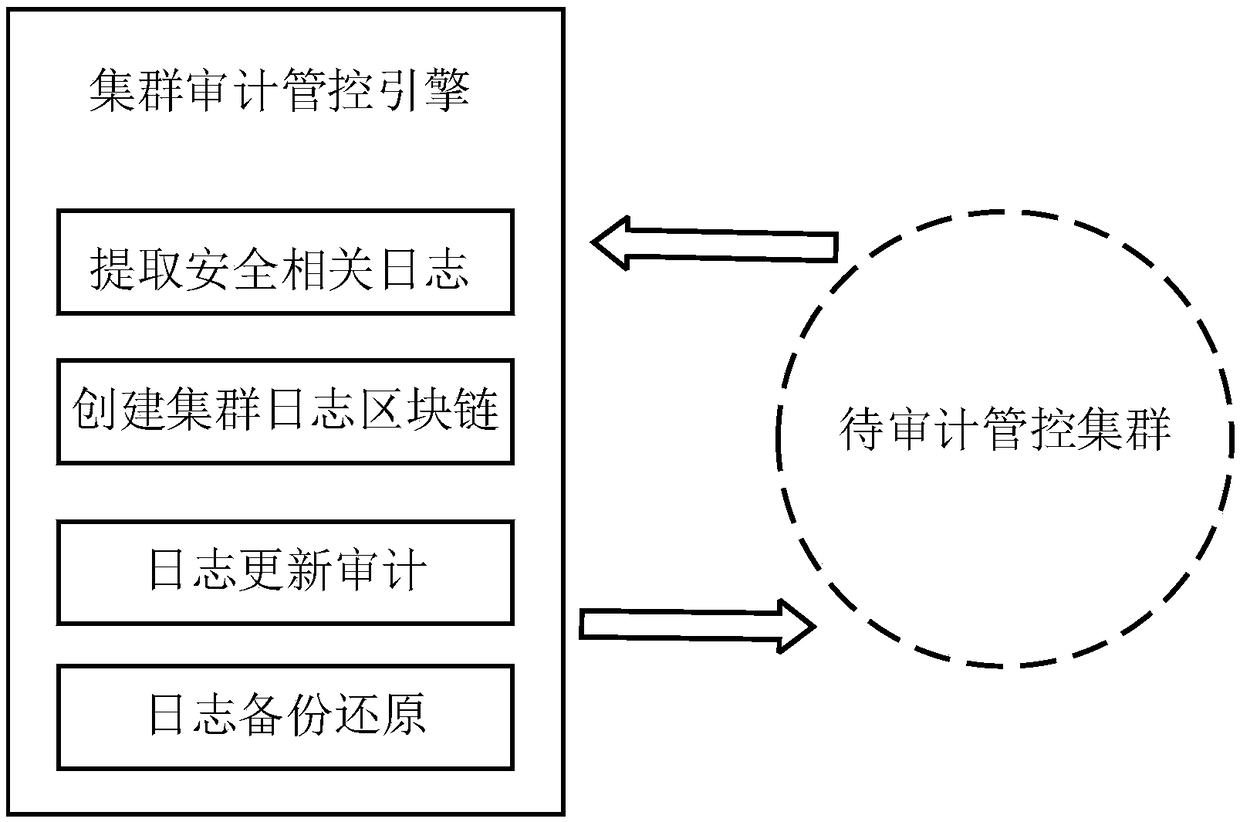
[0026] The schematic diagram of cluster audit management and control in this embodiment is as follows figure 2 As shown, the cluster audit control flow chart is as follows image 3 As shown, it mainly includes the following steps:
[0027] 1) Collect the lo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com