Method for displaying authority after employee in system logs in account thereof
A display method and employee technology, applied in the direction of instruments, electrical digital data processing, digital data protection, etc., can solve the loss of system users, understand their own positions/station numbers that cannot be clearly distinguished, and trace the source of work complicated And other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
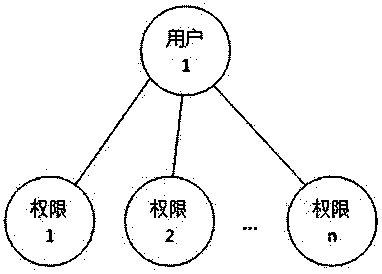
[0036] Example 1: In the system, the account (user) corresponding to employee A is associated with three roles: sales manager 1, production supervisor 1 and financial supervisor 1, and the role of sales manager 1 is the main role of the account. Then, after employee A logs in to the system, the system will display sales manager 1, production supervisor 1, and financial supervisor 1 to employee A, and the corresponding permissions of these three roles, or the system will display sales manager 1 and its corresponding permissions to employee A.
[0037] The authority display method further includes: the employee chooses to display the first information or the second information. For example, in Example 1, after employee A logs in to the system, the system allows the employee to choose roles by himself; employee A can choose to display all roles, then the system will show employee A sales manager 1, production supervisor 1 and financial supervisor 1, and the three The permissions ...
Embodiment 2
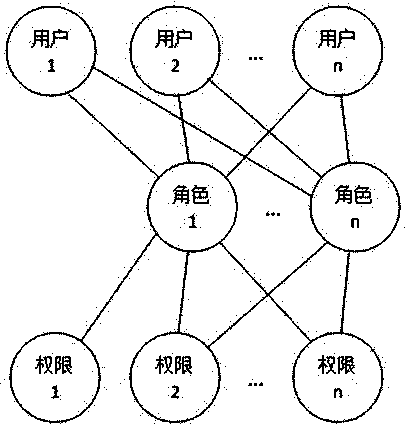
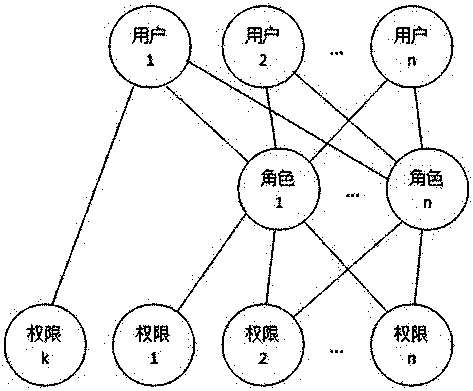
[0049] [Example 2] such as Figure 5 As shown in the system, the permission display method after an employee logs in to their account includes: selecting a created, unassociated employee, and unfrozen account for the employee as the employee's account, or creating a separate account for the employee; The corresponding account login system; the system displays the first information or second information to the employee, the first information includes all roles associated with the account and the permissions corresponding to each role, the second information includes the account associated The main role of all roles and the permissions corresponding to the main role.
example 2
[0050] Example 2: Account A, Account B, and Account C exist in the system, and Account A, Account B, and Account C have no associated employees, Account A and Account B are not frozen, and Account C is frozen. Then you can choose one from account A and account B as employee A's account; or, create a new account in the system as employee A's account.
[0051] In the system, the account corresponding to employee A is associated with three roles: sales manager 1, production supervisor 1, and financial supervisor 1. The role of sales manager 1 is the main role of the account. Then, after employee A logs in to the system, the system will display sales manager 1, production supervisor 1, and financial supervisor 1 to employee A, and the corresponding permissions of these three roles, or the system will display sales manager 1 and its corresponding permissions to employee A.
[0052] The method of creating a separate account for an employee is: select a unique field in the system of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com