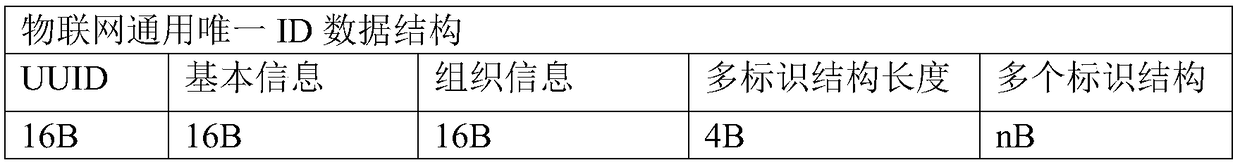
Object authentication method and system based on universal unique token chain of multiple identifier partition sections
An authentication method and segmented technology, which is applied in the field of the generation system of the multi-identification segmented universal unique token chain, to achieve the effect of avoiding the leakage of biological characteristics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] Practical example 1: In the Bluetooth positioning application, after the Bluetooth sniffer obtains the signal strength RSSI values of different Bluetooth beacons, the obtained Bluetooth signal strength event sending process: First, according to the OwnerID of the owner of the sniffer (the fixed line is in the The sniffer or the front-end processing unit) requests the URL address of the cloud server corresponding to the OwnerID from the ANS server. After obtaining the address, the Bluetooth sniffer sends the obtained Bluetooth signal strength event and RSSI value directly to the URL address.
Embodiment 2
[0036] Practical example 2: In the face recognition shopping application, after the face data obtained by the recognition terminal is compared and found, the event data transmission process obtained: first send the OwnerID of the terminal to the ANS server, and the ANS server is in its OwnerID list Find the URL address of the cloud server corresponding to the OwnerID, and return the URL address to the terminal. The terminal sends the acquired event data directly to the URL address.
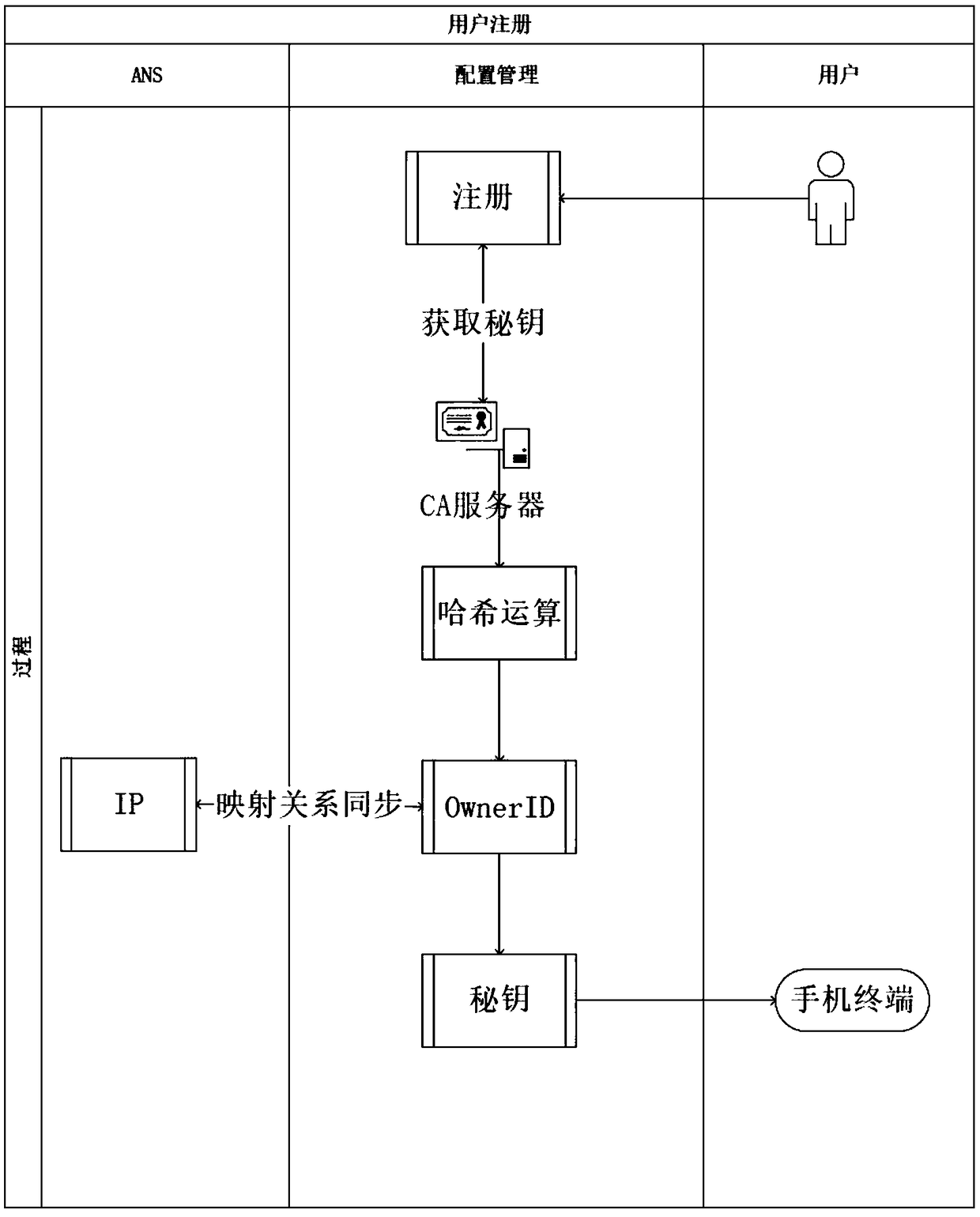
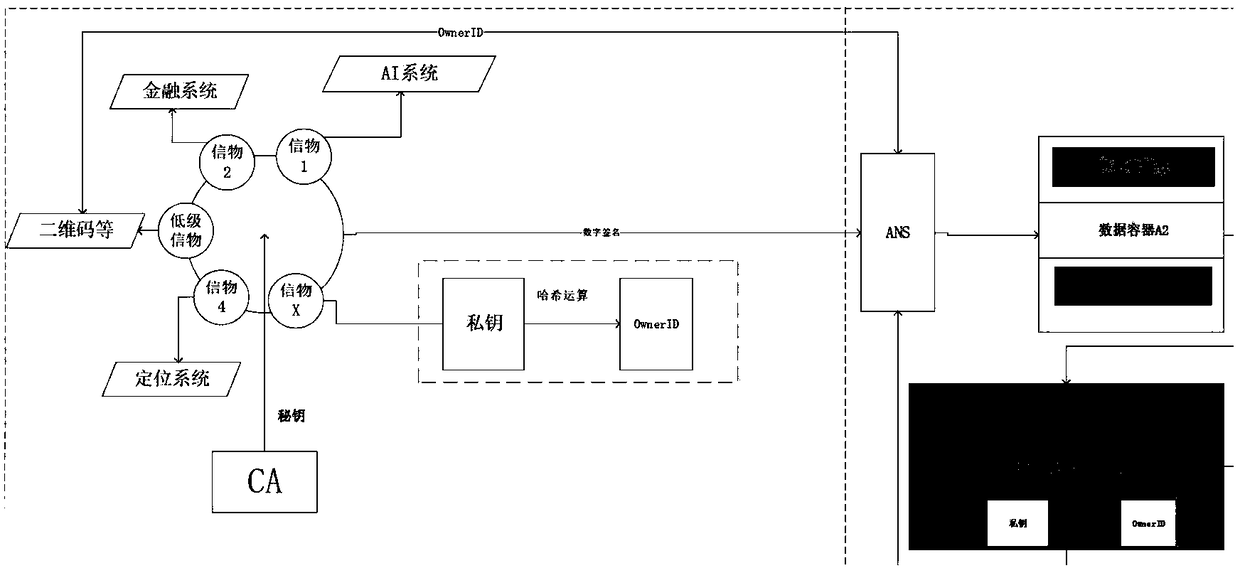
[0037] Such as figure 2 Shown is the data flow during the user's use. A user's various tokens and terminals share the same CA certificate, use its private key and private key to perform hash operations to obtain the OwnerID, and query the ANS server to obtain the URL address of the user's data container in the cloud for data forwarding. The data is sent directly to the data container owned by the user in the cloud.
[0038] Compared with the traditional identity verification, the present inven...
Embodiment 3
[0040] Security level 1: Company sign-in, only need to provide verification of one of the authentication results. Such as work permits, fingerprints, or personal mobile phones. You only need to pass one of them to be certified.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com