A javascript data transmission encryption method
A technology of data transmission and encryption method, which is applied in the field of information security to achieve the effect of ensuring reliability, preventing interception and application, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
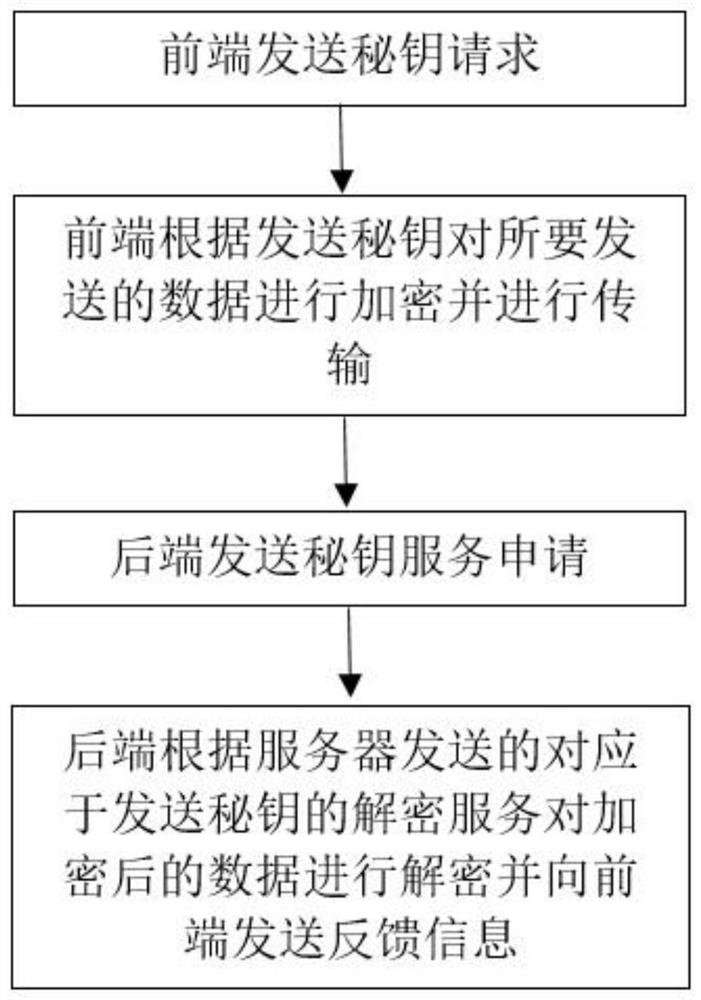
[0024] This embodiment provides a JavaScript data transmission encryption method, see figure 1 , the method includes:
[0025] Step 1: The front-end sends a secret key request, which is used to apply for sending a secret key to the server. The secret key request includes front-end attributes, so that after receiving the secret key request sent by the front-end, the server generates a sending secret in a predetermined way according to the front-end attributes. key and send it to the front end;
[0026] Step 2: The front end receives the sending key sent by the server, encrypts the data to be sent according to the sending key, and sends a data transmission request to the back end. The data transmission request includes the encrypted data and its corresponding sending key;
[0027] Step 3: The backend receives the data transmission request sent by the frontend, and sends a secret key service request to the server according to the data transmission request, and the secret key ser...
Embodiment 2
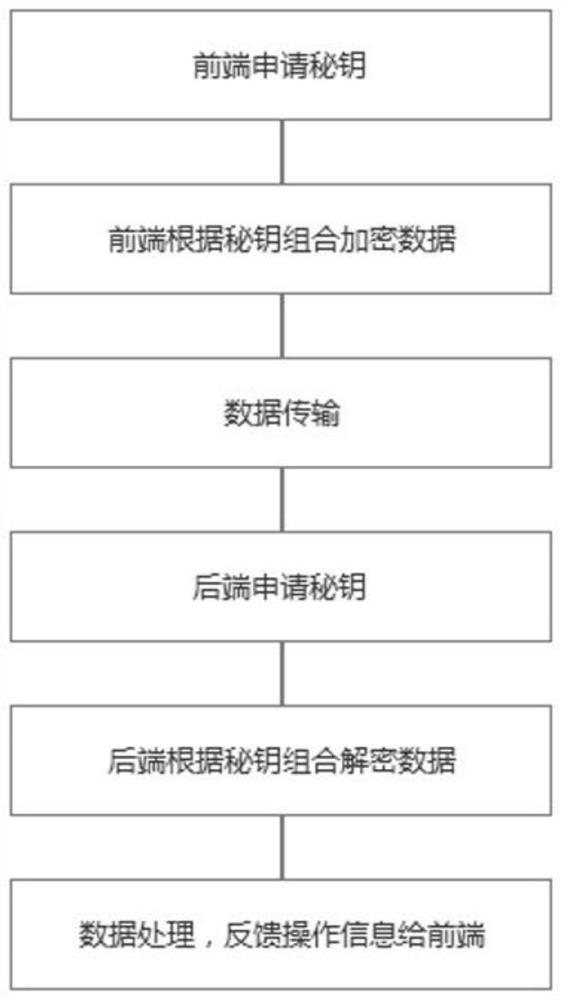
[0031] This embodiment provides a JavaScript data transmission encryption method, see figure 2 , the method includes:
[0032] Step 1: Apply for a secret key at the front end;
[0033] Before the front-end prepares to transmit data, it first sends a secret key request to the server to apply for sending a secret key. The secret key request includes front-end attributes so that the server can generate it in a predetermined way according to the front-end attributes after receiving the secret key request sent by the front-end. Send the secret key, where the front-end attributes include the front-end IP address, the request interface id, and the random number of the established rules;
[0034] Before the server generates the sending key in a predetermined way according to the front-end properties, it will first verify the front-end properties, including: verifying whether the front-end IP is legal, whether the request interface exists, whether the request interface has the author...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com