Library hit attack detection method, device and equipment and computer readable memory medium
A technology of attack detection and preset thresholds, which is applied in the field of network security, can solve problems such as NAT environment false positives, hard-to-crash attacks, and large traffic on portal websites, so as to improve recognition accuracy and reduce rule complexity and calculation load. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 2 example
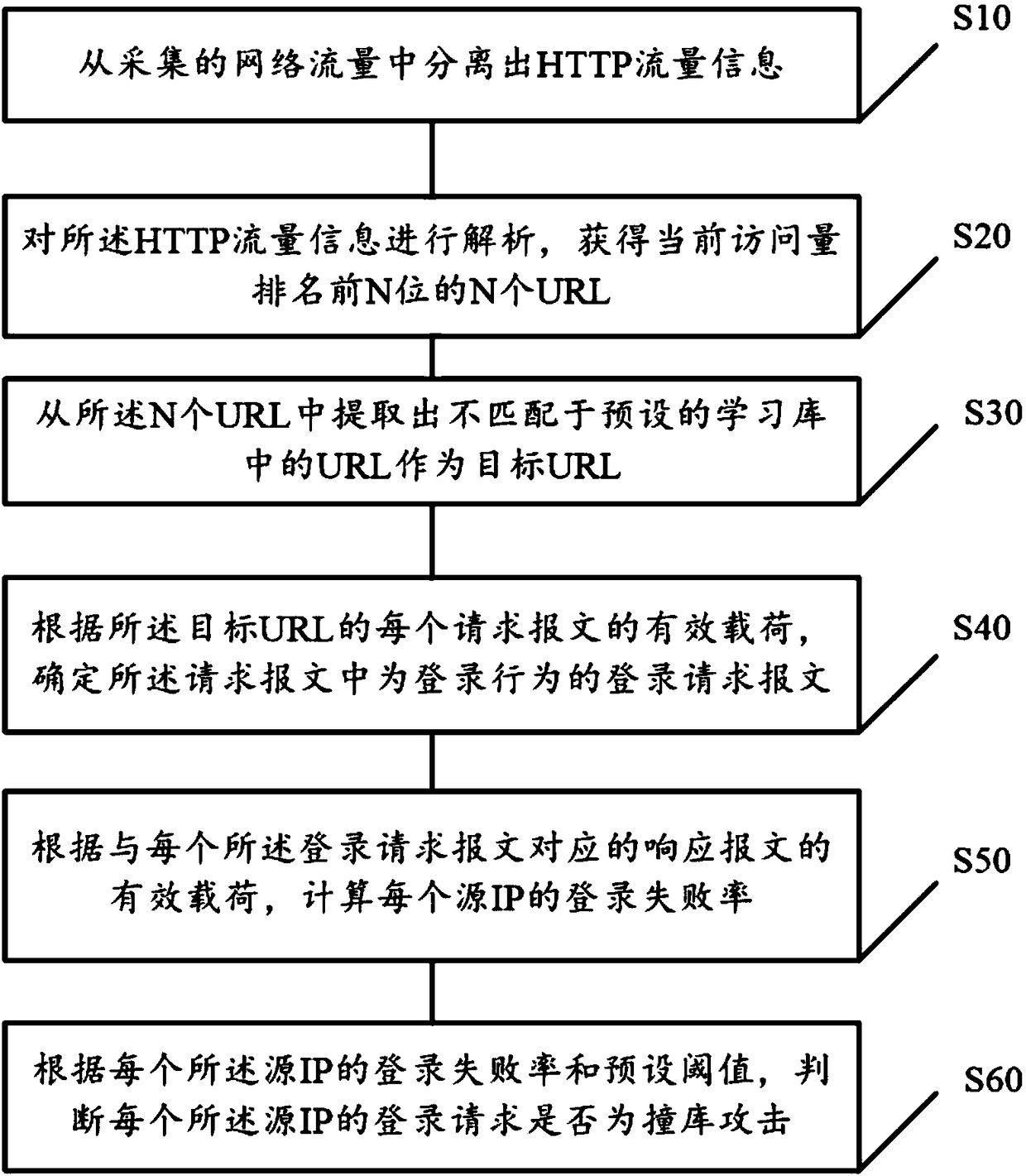
[0068] The learning library includes at least two groups of URL groups corresponding to time periods; each URL group includes N first URLs; each URL group contains N first URLs extracted according to the same time period within a predetermined historical date Obtain the statistics of the top N URLs in terms of visits.
[0069] Then, the URL that does not match the preset learning library is extracted from the N URLs as the target URL, specifically:
[0070] Obtain the URL group corresponding to the current moment in the learning library;
[0071] A URL that does not exist in the URL group is extracted from the N URLs as a target URL.
[0072] Specifically, the activity of different URLs in different time periods is different. For example, the websites corresponding to some URLs are more active during the day, that is, they have a relatively large number of visits during the day (top N), while the websites corresponding to some URLs are more active during the daytime. The num...
no. 3 example
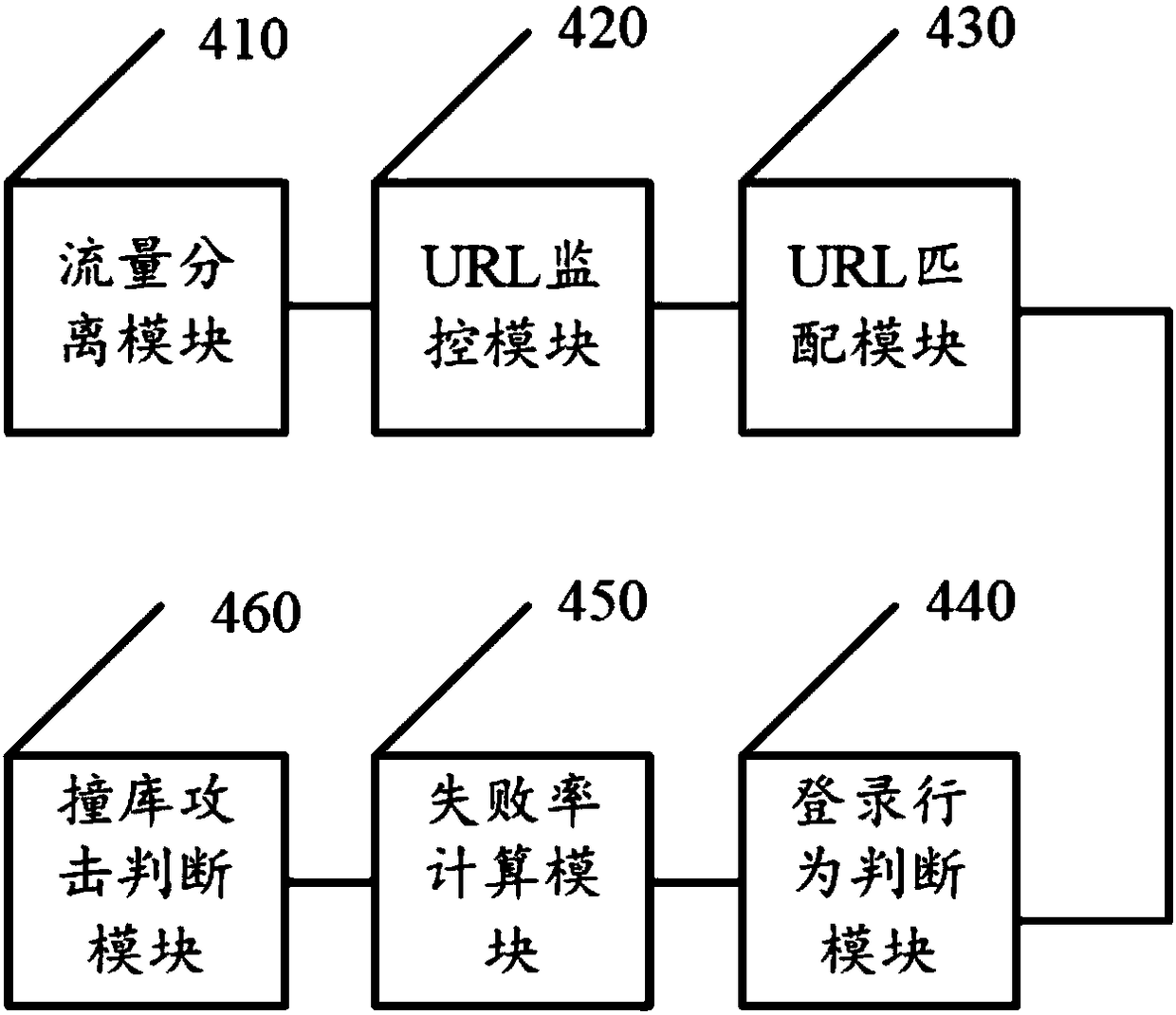
[0075] On the basis of the first embodiment:
[0076] According to the payload of each request message of the target URL, it is determined that the login request message in the request message is a login behavior, specifically:
[0077] Using stream processing mode for the payload of each request message of the target URL, matching through ordered vectorization technology to obtain a matching result;
[0078] According to the matching result, judging whether the request message is a login behavior;
[0079] If not, discarding the request message;
[0080] If yes, mark the request packet as a login request packet.
[0081] In this embodiment, as an example, the stream processing mode is used for the payload of each request message of the target URL, and high-speed matching is performed in multiple dimensions through the ordered vectorization technology, wherein the matched dimension and keyword It can be set by the user, for example, only filter the request message whose req...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com