Method for detecting local rejection service vulnerabilities of dynamic Receiver components of android applications
A denial of service and vulnerability detection technology, applied in software testing/debugging, error detection/correction, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
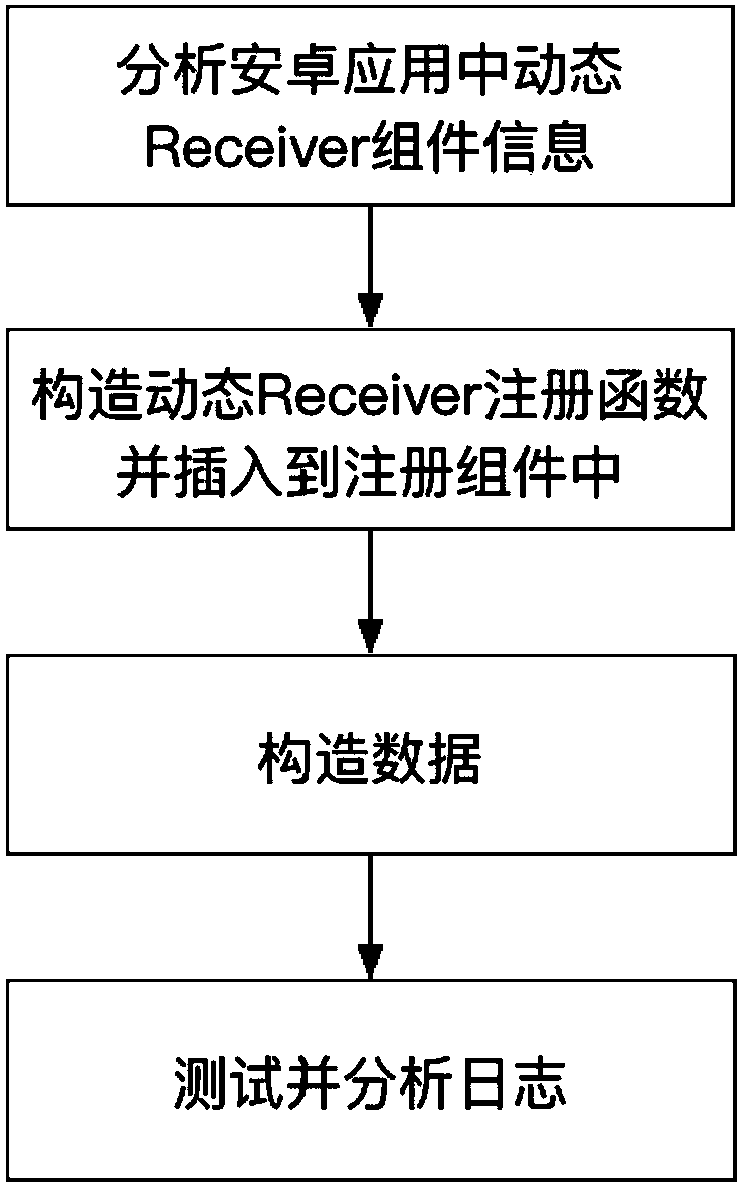
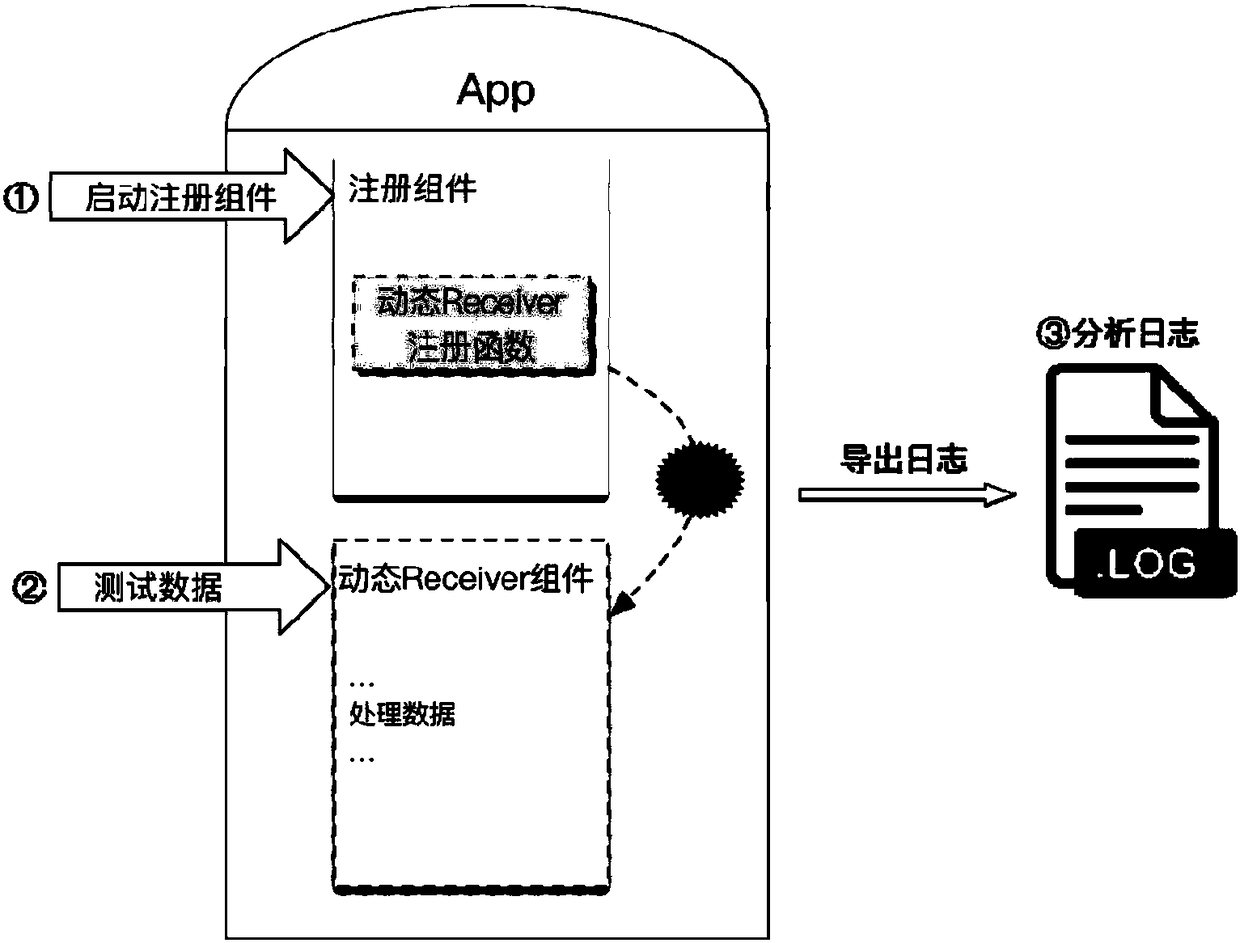
[0068] Step 1: Analyze dynamic Receiver component information
[0069] a) Get dynamic Receiver component name and intent-filter object
[0070]Ic3 is a tool for attribute value analysis of complex objects. The present invention uses the control flow graph between application processes constructed by the Ic3 tool to analyze the dynamic Receiver component information registered by the registerReceiver method in the application, including component name, intent-filter information (by action , category and data).
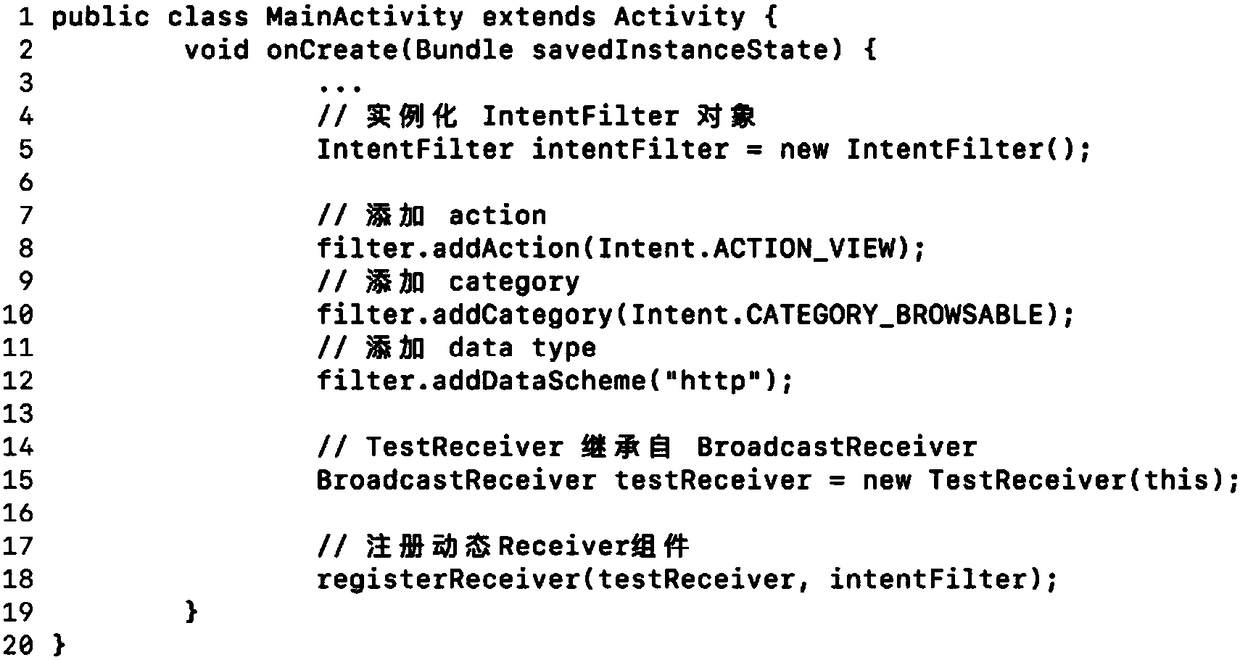
[0071] image 3 Shows an example of registering a dynamic Receiver component in code. Line 19 of the code registers a dynamic Receiver component named TestReceiver, which is defined as Figure 4 . The action attribute value of the dynamic Receiver component intent-filter is ACTION_VIEW; the category attribute value is CATEGORY_BROWSABLE; the Scheme attribute value in Data is http.
[0072] b) Analyze the data format that the dynamic Receiver component can receive ...
Embodiment 2
[0110] 300 applications were randomly downloaded from the application market and tested using the method of the present invention, and it was found that 61 applications contained a total of 139 dynamic Receiver components, of which 79 components did not obtain data from the intent, and were directly determined not to contain local denial of service vulnerabilities . Among the other 60 dynamic Receiver components, there are 45 parameters that are empty or component names, which belong to the detection scope of the present invention. The present invention that the remaining 15 parameters are not component names cannot be detected.
[0111] Utilize the inventive method to test these 45 dynamic Receiver components after rewriting, and the start-up situation test result is as shown in table 8, in 45 dynamic Receiver components, there are 42 just can start when application starts, can finish test, start test The success rate is about 93%. The reason for the failure of the thre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com