Method for redirecting access request, medium and device
An access request and redirection technology, applied in the computer field, can solve the problems of counterfeit replies, inability to redirect HTTPS requests, inability to parse content, etc., achieving the effect of simple deployment, no network bottlenecks, and no network failure risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
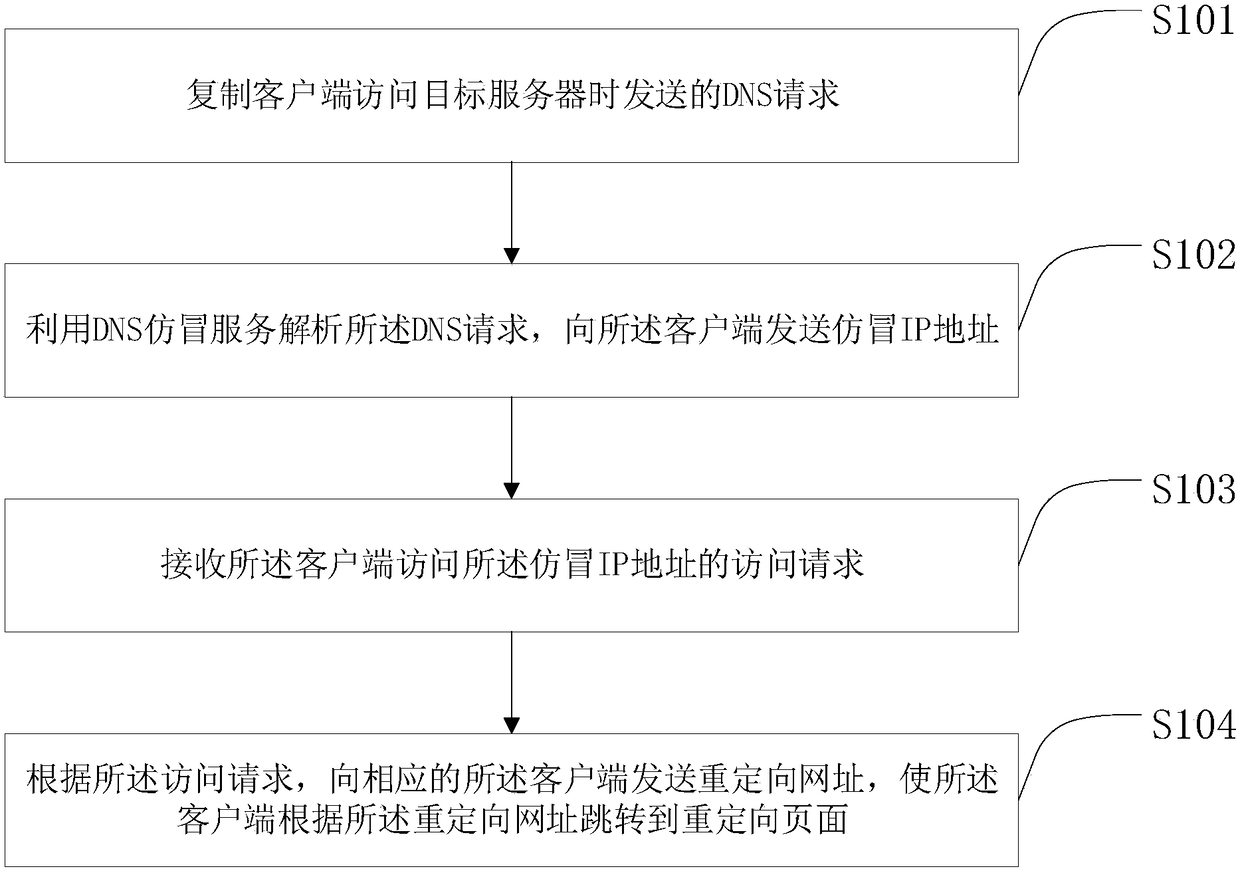
[0042] Please refer to figure 1 , figure 1 It is a flowchart of a method for redirecting an access request provided in the first embodiment of the present invention. The method for redirecting an access request provided in this embodiment includes:
[0043] Step S101: copying the DNS request sent by the client when accessing the target server.
[0044] Step S102: Utilize a DNS spoofing service to resolve the DNS request, and send a spoofed IP address to the client.
[0045] Step S103: Receive an access request from the client to access the counterfeit IP address.
[0046] Step S104: According to the access request, send a redirect URL to the corresponding client, so that the client jumps to a redirect page according to the redirect URL.
[0047] When the user accesses the target server, the client will first send a DNS request to the DNS server, obtain the target IP address of the target server sent by the DNS server, and then access the corresponding target server accordin...
no. 2 example
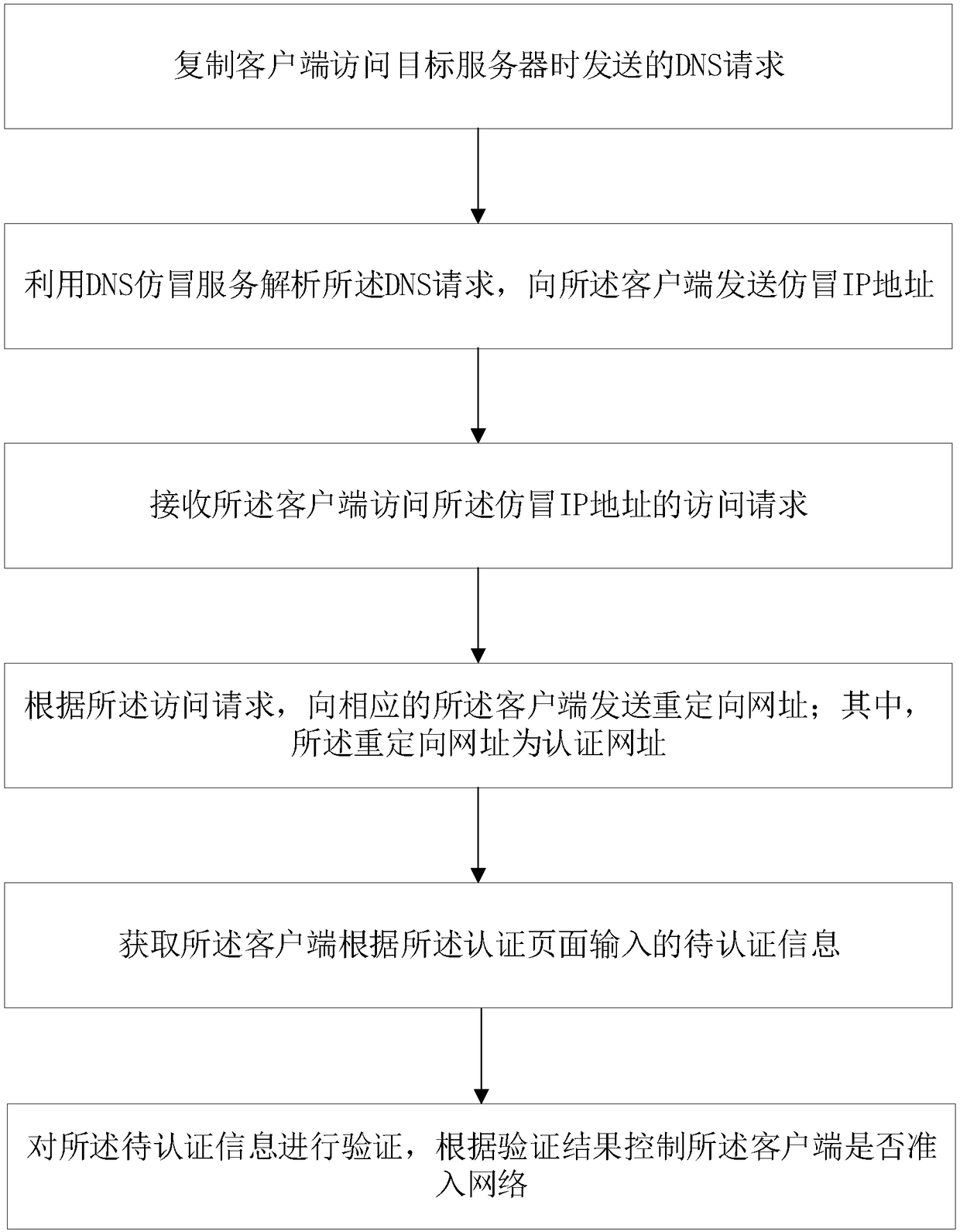
[0061] In the above-mentioned first embodiment, a method for redirecting an access request is provided. In combination with the above-mentioned first embodiment, the second embodiment of the present invention provides a computer-readable storage medium on which a computer program is stored. When the program is executed by the processor, the method for redirecting the access request provided by the above-mentioned first embodiment is implemented.
no. 3 example
[0063] In combination with the method for redirecting an access request provided in the first embodiment, the present invention also provides a computer device, including: a memory, a processor, and a computer program stored on the memory and operable on the processor, the processing When the server executes the program, the method for redirecting the access request provided by the above-mentioned first embodiment is implemented. figure 2 A schematic diagram of a hardware structure of a computer device provided by an embodiment of the present invention is shown.
[0064] Specifically, the above-mentioned processor 201 may include a central processing unit (CPU), or an Application Specific Integrated Circuit (ASIC), or may be configured to implement one or more integrated circuits in the embodiments of the present invention.
[0065] Memory 202 may include mass storage for data or instructions. By way of example and not limitation, the memory 202 may include a hard disk drive...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com