A self-certified digital identity management system and method based on smart contracts
A digital identity and smart contract technology, applied in the field of information security, can solve problems such as being easy to be tampered with, users cannot have control over information data, and information data cannot be modified and deleted at will.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
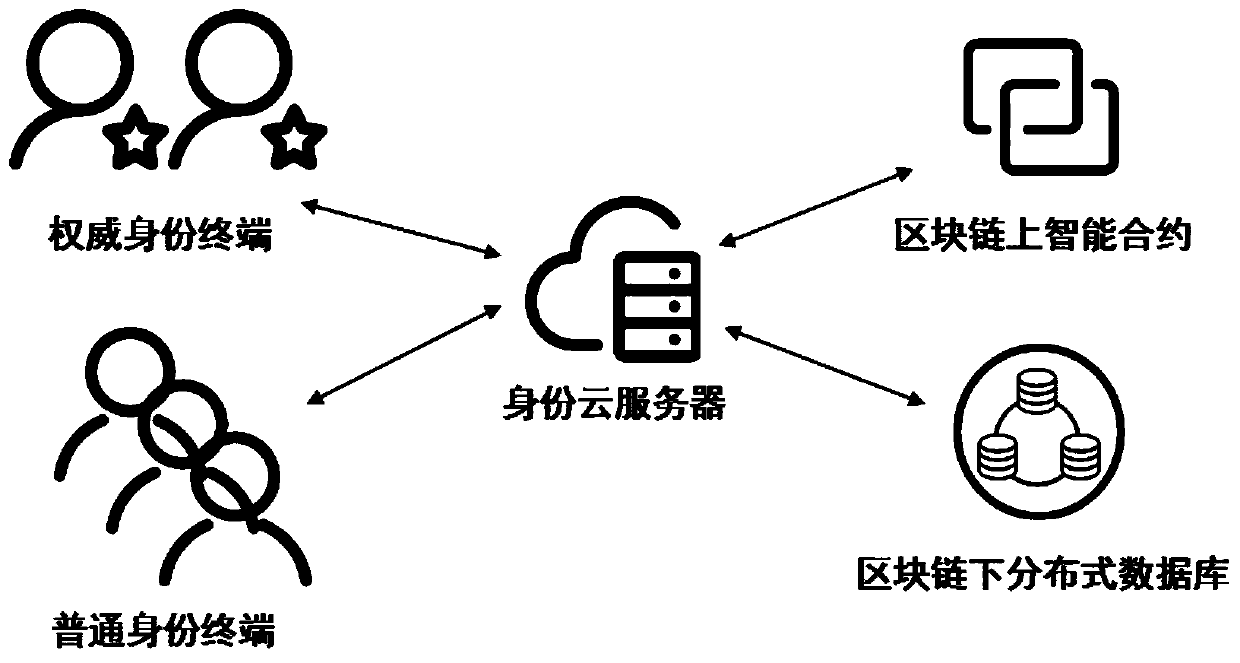
[0065] In this embodiment, a smart contract-based self-certified digital identity management system, such as figure 1 As shown, including: ordinary identity terminal, authoritative identity terminal, identity cloud server, smart contract on blockchain and distributed database under blockchain;
[0066] Identity terminals are terminal applications installed on device terminals such as smartphones, tablet computers, desktop computers, and notebooks, and are divided into ordinary identity terminals and authoritative identity terminals. Ordinary identity terminals mainly enter the user's digital information, complete the registration of digital identity and encrypt and upload digital information through the identity cloud server interaction interface, and authorize the digital information to other identity terminals through the identity cloud server interaction interface. Ordinary identity terminals include: key generation module, two-dimensional code module, digital identity regi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com