SeLinux-based resource access method and device under multiple users
A technology of resource access and resource access request, applied in computer security devices, instruments, computing and other directions, can solve problems such as security loopholes, loss of host users, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
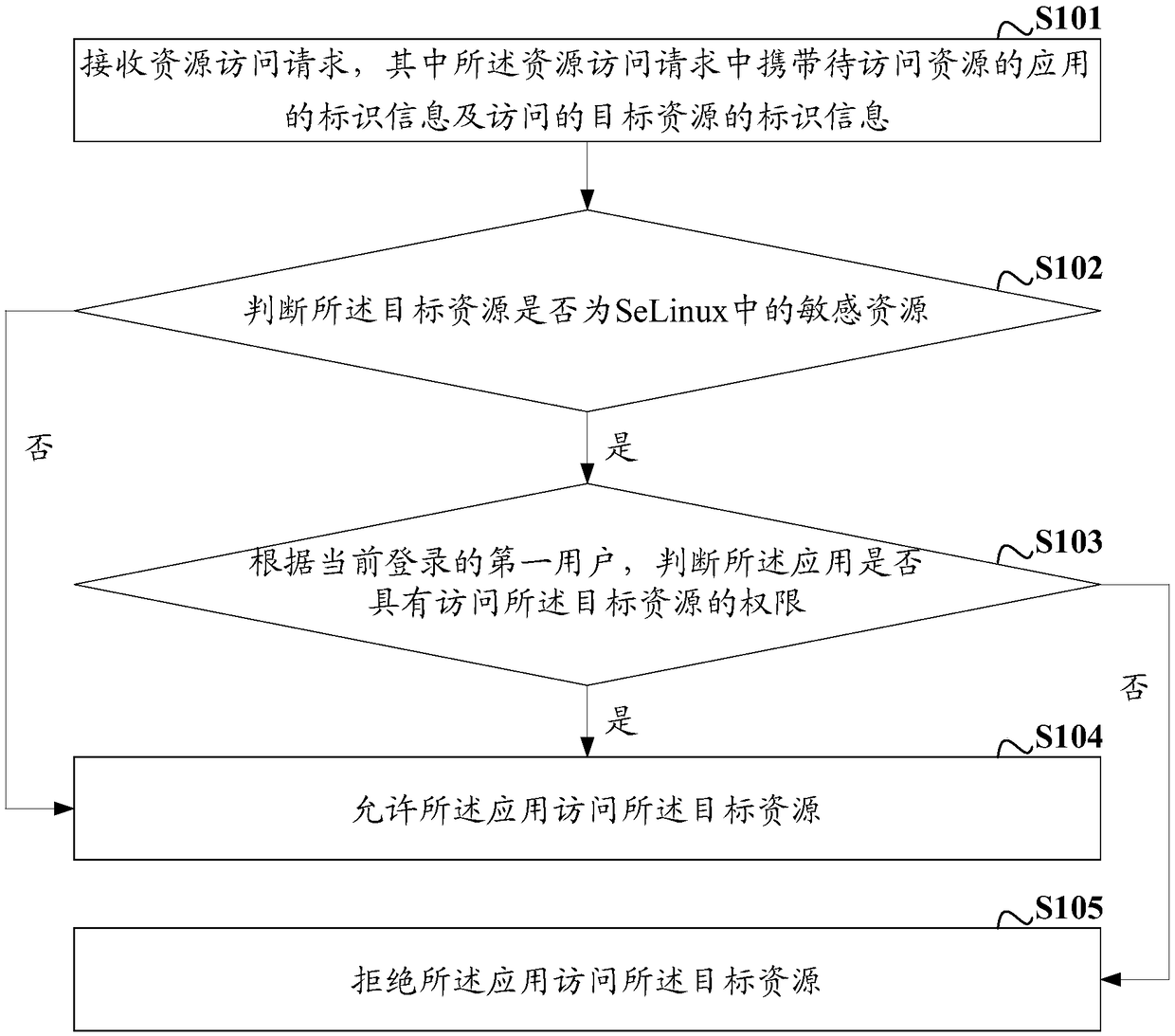
[0047] figure 1 A schematic diagram of a resource access process based on SeLinux under a multi-user provided by the embodiment of the present invention, the process includes:
[0048] S101: Receive a resource access request, wherein the resource access request carries identification information of an application to access a resource and identification information of a target resource to be accessed.
[0049] The multi-user-based Android SeLinux resource access method provided by the embodiment of the present invention is applied to a mobile terminal, and the mobile terminal may be a mobile phone, a tablet computer, and the like.
[0050] With the start of Android5.1, Google has added the function of supporting multiple users in Android. Multiple user accounts can be established in the same android mobile terminal. Each user account corresponds to a user, and each user can have their own Applications, application data, and system settings. The first user in the embodiment of...
Embodiment 2
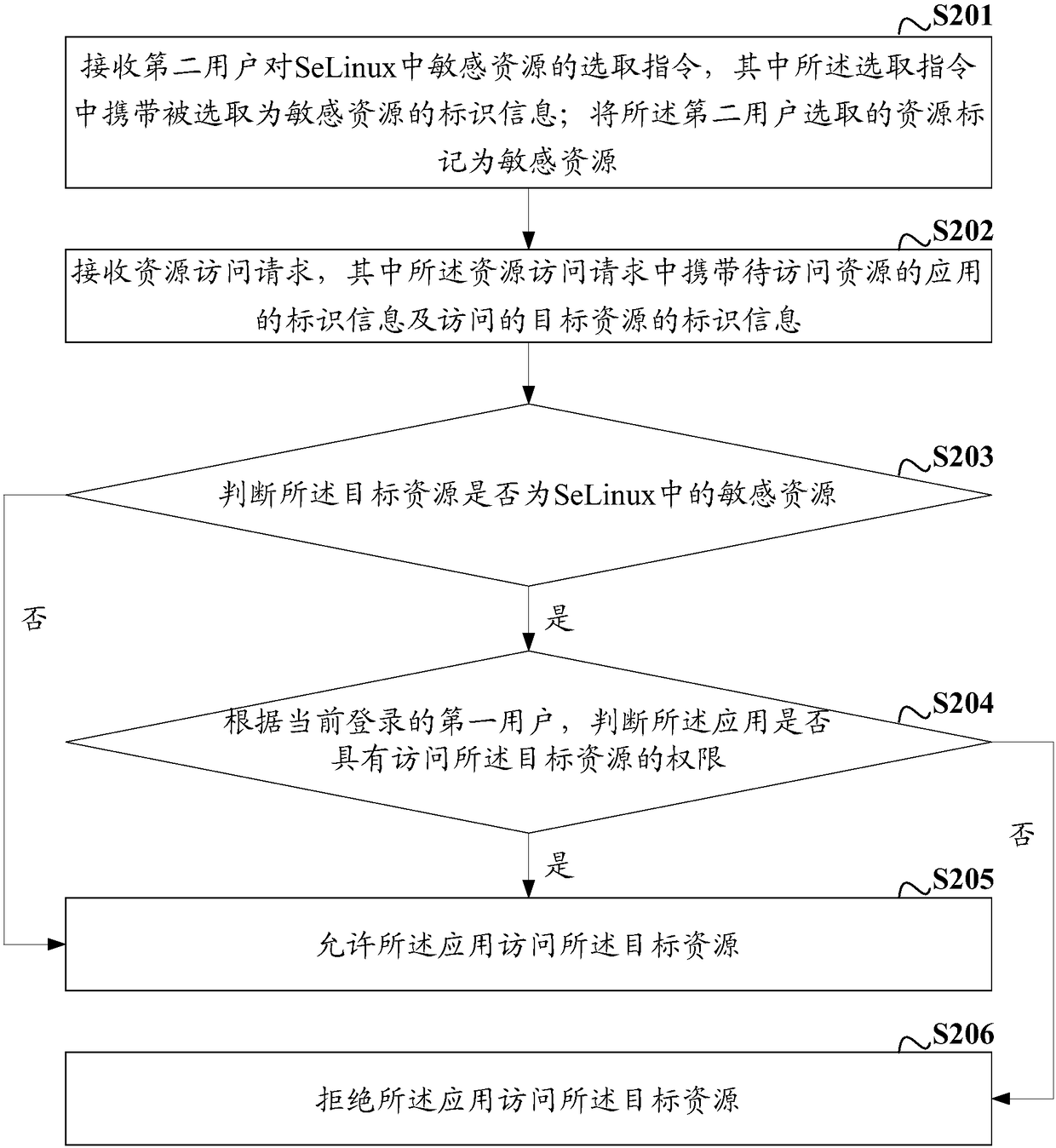
[0064] In the embodiment of the present invention, the host user can divide the resources in SeLinux according to their own needs, thereby improving the experience of the host user. On the basis of the above-mentioned embodiment, before the resource access request is received, the method Also includes:
[0065] receiving a second user's selection instruction for sensitive resources in SeLinux, wherein the selection instruction carries identification information selected as a sensitive resource;
[0066] Marking the resource selected by the second user as a sensitive resource.
[0067] The second user can be the owner user of the mobile terminal, or a non-owner user who is given sensitive resource selection authority by the owner user. In the existing Android multi-user mechanism, the first one to start the mobile terminal The user is called the master user, similar to the administrator user in a personal computer (PC).
[0068] Specifically, receiving an instruction from a s...
Embodiment 3
[0079] In order to reduce security vulnerabilities and provide information security, on the basis of the above implementations, in the embodiment of the present invention, the method further includes:
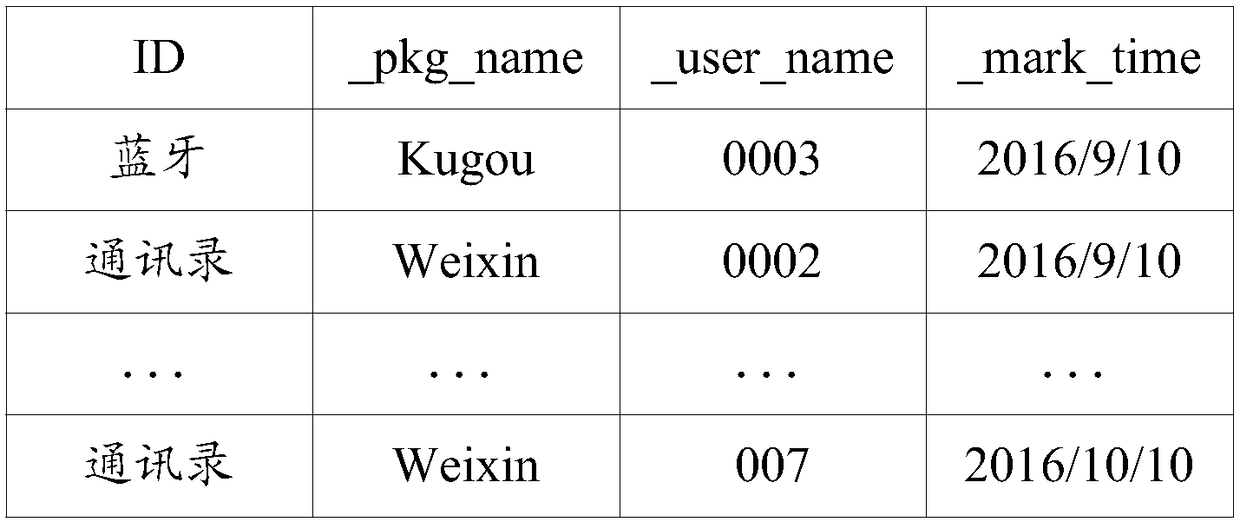
[0080] receiving a configuration instruction from the second user to the first user, wherein the configuration instruction includes identification information of the first user and identification information of an application capable of accessing the sensitive resource for each sensitive resource in SeLinux;
[0081] According to the configuration instruction, for the first user and each sensitive resource, the identification information of the application that can access the sensitive resource is stored in the configuration table.
[0082] The current basic principle of SELinux is that a resource access request has a security label, and a resource in SELinux also has a security label. When a resource access request accesses a resource in SELinux, the labels of the two need to b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com