Method and system for monitoring operating system data integrity
A data integrity and operating system technology, applied in digital data protection, electrical digital data processing, special data processing applications, etc., can solve problems such as insufficient content, insufficient fine-grainedness, and inability to actively generate easy-to-read reports.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to more clearly illustrate the technical solutions in the embodiments of the present invention, the following will briefly introduce the accompanying drawings that need to be used in the embodiments. Obviously, the accompanying drawings in the following description are only some embodiments of the present invention. For Those of ordinary skill in the art can also obtain other drawings based on these drawings without making creative efforts.
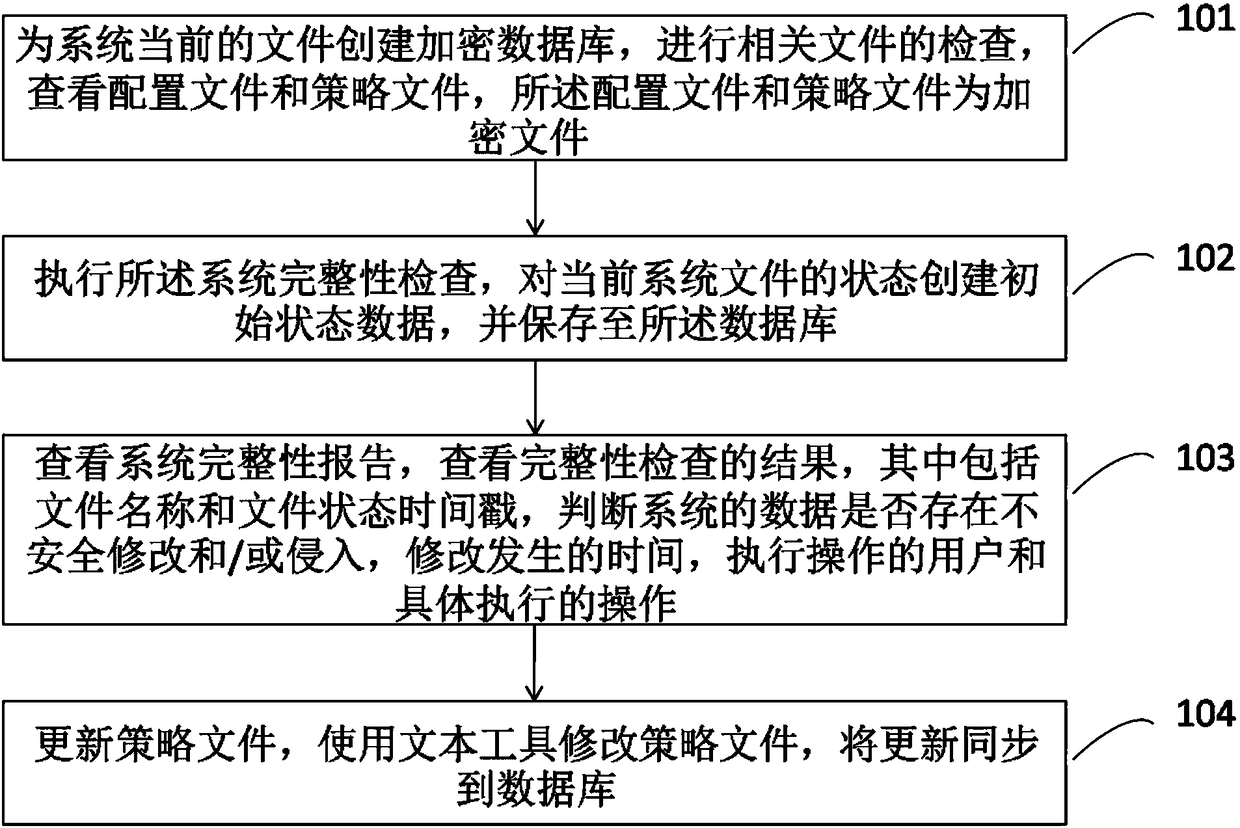
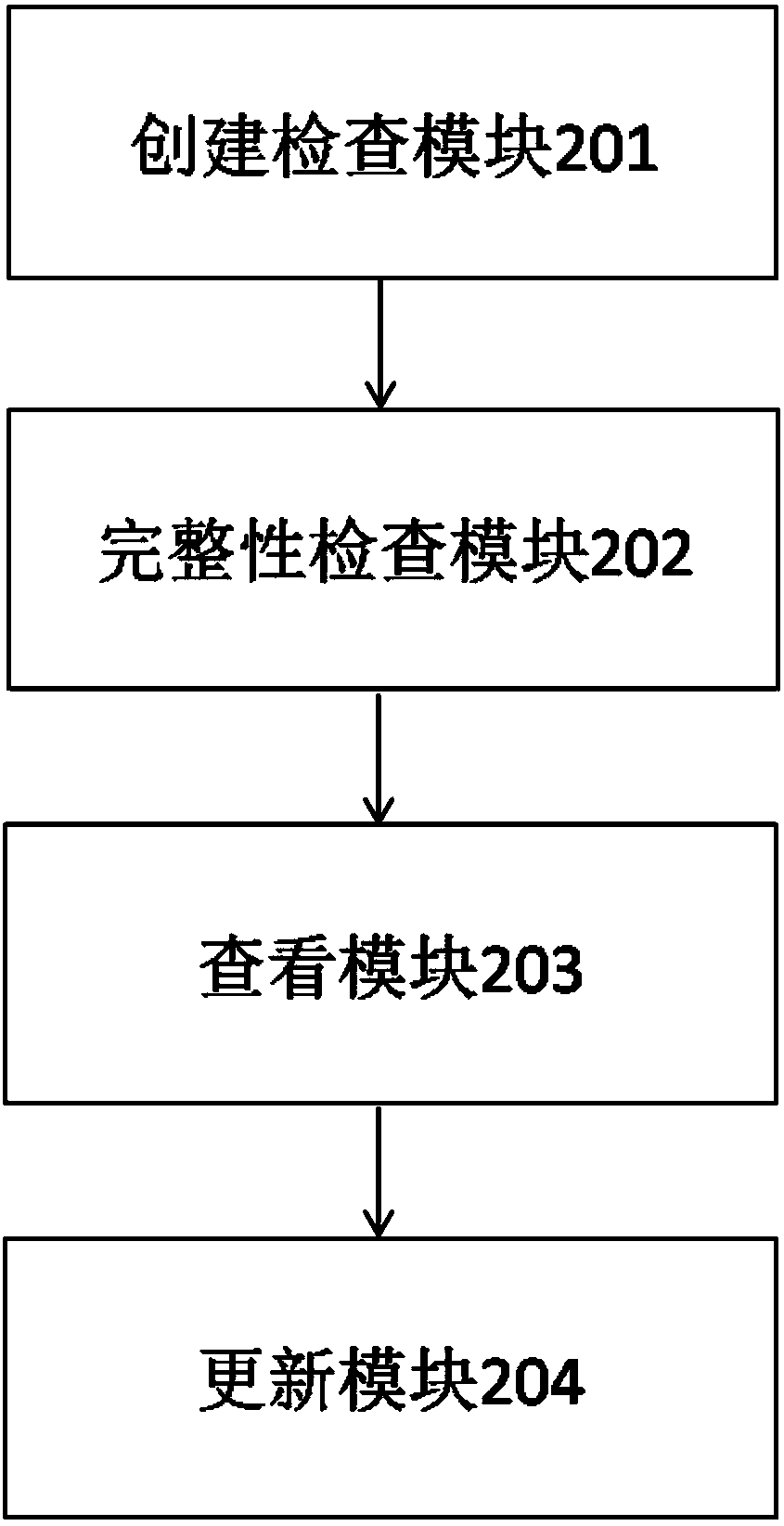
[0026] The present invention can be applied to Linux operating system, Unix operating system and K-UX operating system (K-UX operating system is a key application host operating system independently developed by Inspur). In the present invention, K1 is a key application host independently developed by Inspur, and MD5 is a hash function widely used in the field of computer security to provide data integrity protection.
[0027] Based on the above, on the one hand, the embodiment of the present invention provides a method fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com