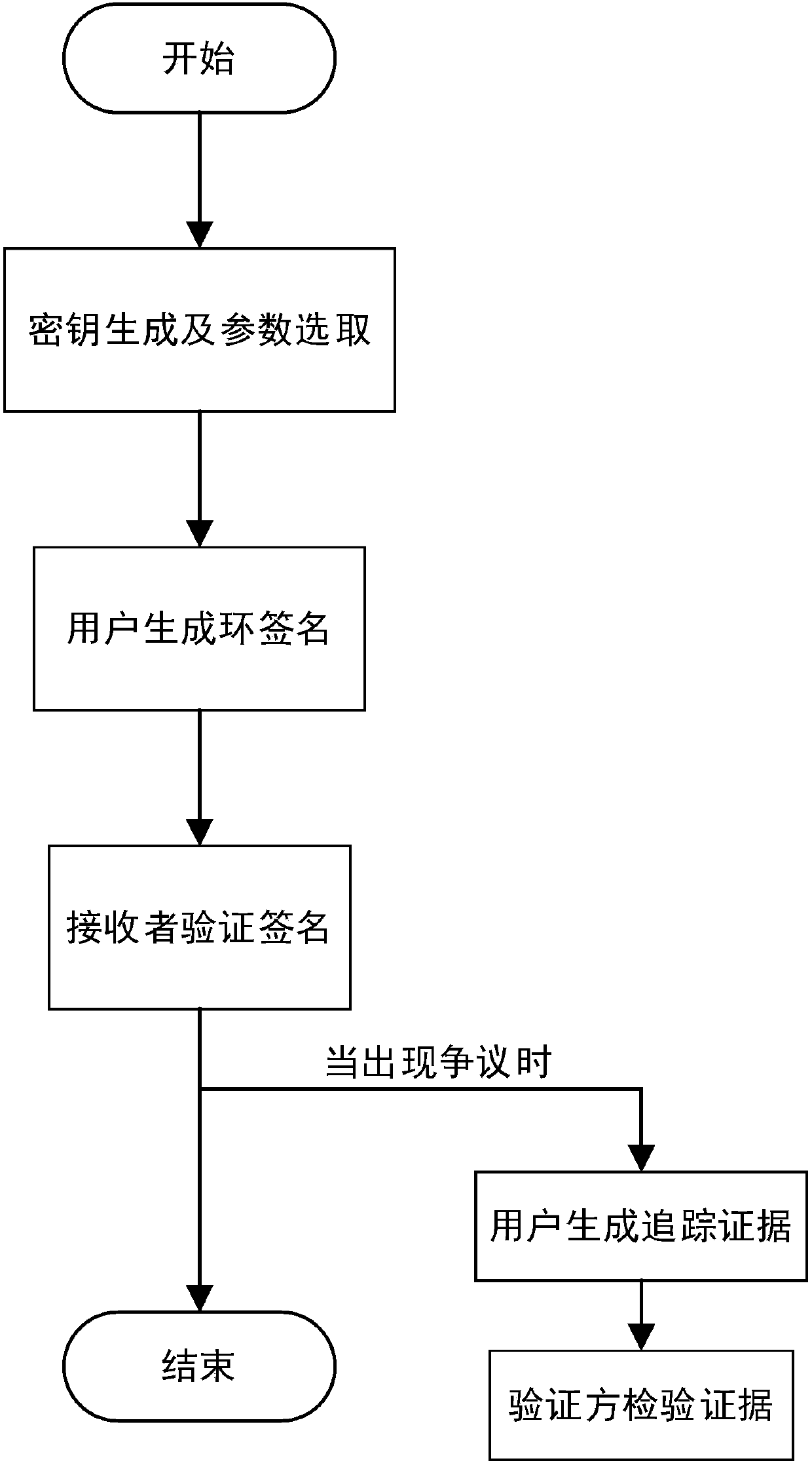
Identity-based traceable ring signature authentication protocol
An authentication protocol and ring signature technology, which is applied in the field of identity-based traceable ring signature authentication protocol, can solve the problem of being unable to resist collusion attacks between dishonest signers and non-signers, and achieve simple generation and verification, resistance to collusion attacks, The effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention will be specifically introduced below in conjunction with the accompanying drawings and specific embodiments.
[0018] Explain and explain the relevant concepts involved in the above technical solutions:
[0019] 1. Anti-collision accumulator
[0020] The anti-collision accumulator is a tuple ({X 1} 1∈N ,{F 1} 1∈N ), where {X 1} 1∈N is called the value field of the accumulator, {F 1} 1∈N It is a collection of system functions. choose(f,g)∈{F 1},in while g:U f → U g is a bijective function. In the present invention, an ID-based accumulator can be implemented as follows: Select a security parameter 1 k , get a tuple t=(p,G 1 ,G M ,e,P), where p is a large prime number, and P is the additive cyclic group G 1 A generator of G M is a and g 1 For multiplicative groups of the same order, e is a bilinear pairing. then choose a Calculate t'=(P,sP,...,s q P), and t' is public. Then the accumulator function (f,g) is defined as:
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com