Traffic attack protection method and system, traffic attack protection control device and traffic attack protection processing device
一种流量攻击、处理系统的技术,应用在网络安全领域,能够解决降低DDoS防护系统可靠性和稳定性、CPU冲击、降低封堵流量时效性等问题,达到提升稳定性和可维护性、减少需求、提升时效性和可靠性的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0053] This embodiment describes the perspective of the traffic attack protection device. The protection device can protect and control the traffic attack, so it can also be called the traffic attack protection control device. The protection control device may be integrated in a controller, such as an SDN controller.
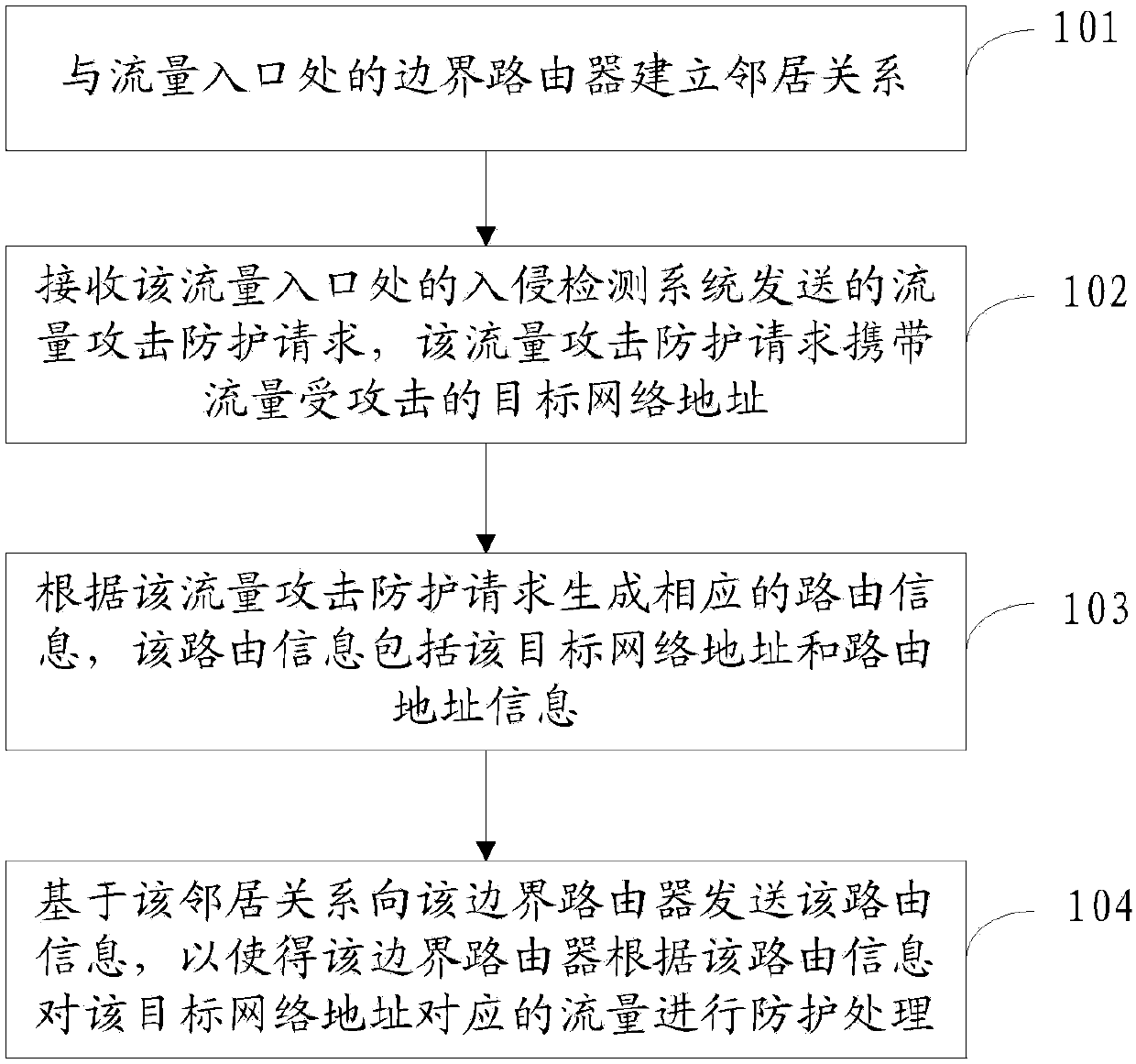
[0054] A traffic attack protection method, comprising: establishing a neighbor relationship with a border router at a traffic entrance, and then receiving a traffic attack protection request sent by an intrusion detection system at the traffic entrance, the traffic attack protection request carrying a traffic attacked target Network address, generate corresponding routing information according to the traffic attack protection request, the routing information includes the target network address and routing address information, send the routing information to the border router based on the neighbor relationship, so that the border router The traffic corresponding ...
Embodiment 2
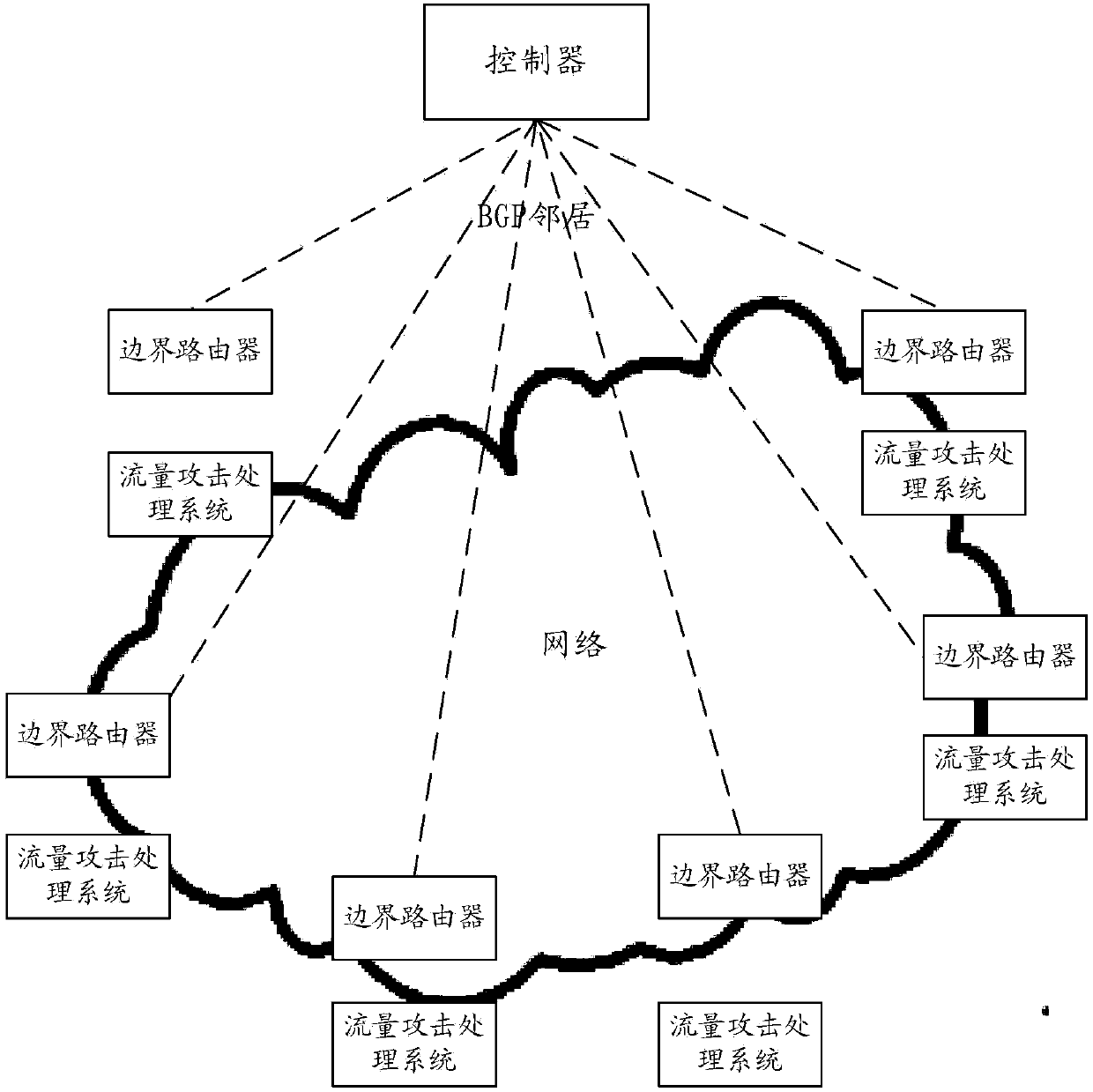
[0094] This embodiment will describe another traffic attack protection method from the perspective of another traffic attack protection device. The protection device can protect traffic attacks, so it can also be called a traffic attack protection processing device. The protective processing device may be integrated in a border router, or other border routing devices located at the traffic ingress.
[0095] A method for defending against traffic attacks, comprising: establishing a neighbor relationship with a controller, and then receiving routing information sent by the controller based on the neighbor relationship, the routing information including routing address information and a target network address where traffic is attacked, according to the The routing information performs protective processing on the traffic corresponding to the target network address.
[0096] Such as image 3 As shown, a traffic attack protection method, the specific process is as follows:
[009...
Embodiment 3
[0127] According to the methods described in Embodiments 1 and 2, examples will be given below for further detailed description.
[0128] In this embodiment, description will be made by taking the traffic attack protection control device integrated in the controller and the traffic attack protection processing device integrated in the border router as an example.
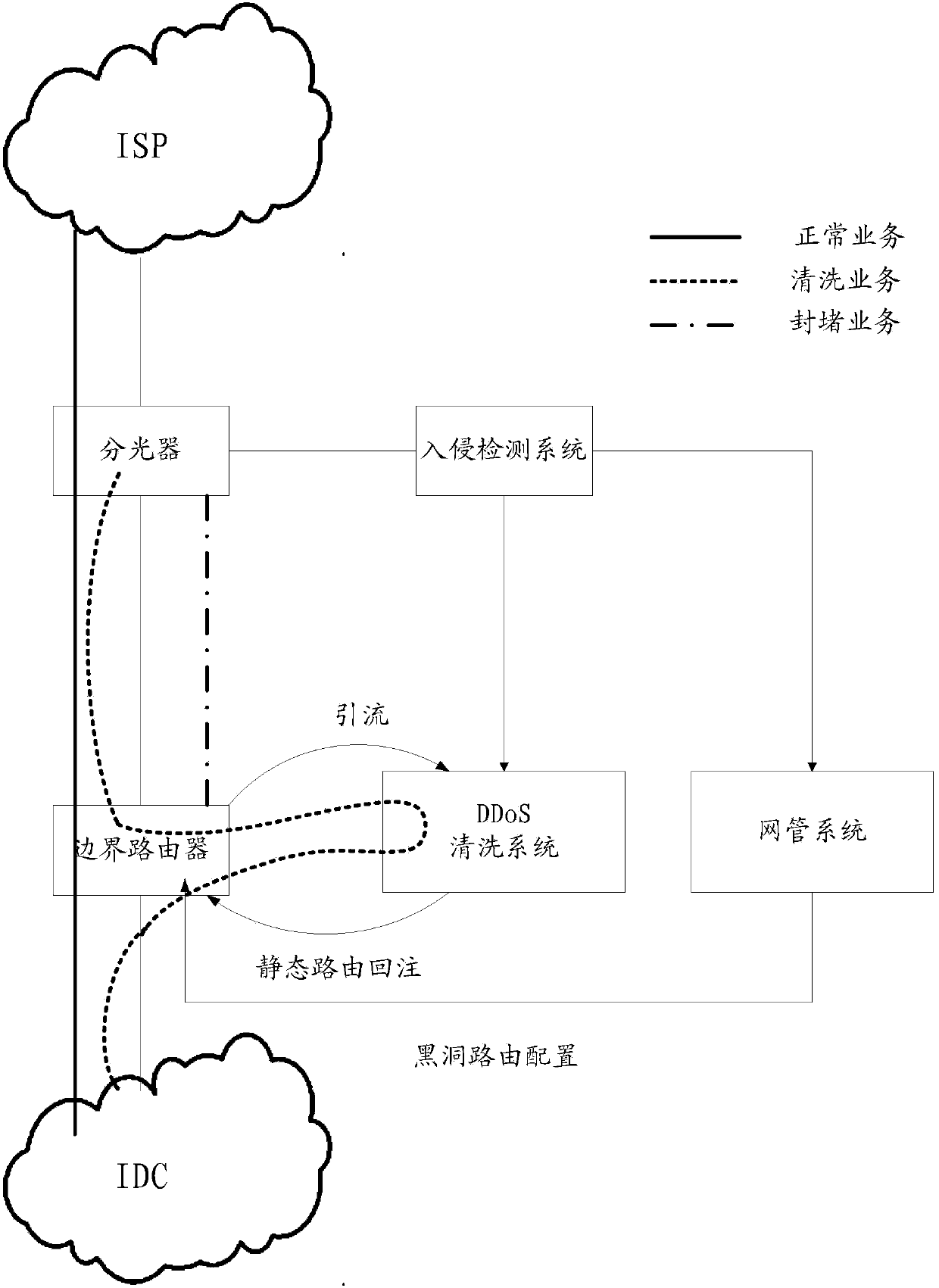
[0129] Such as Figure 4a As shown, the protection system of a kind of traffic attack comprises: optical splitter, intrusion detection system IDS, controller, DDoS cleaning system and border router at the entrance of network flow; Wherein, optical splitter and ISP (Internet ServiceProvider, Internet Service Provider) Connection, the border router is connected with IDC (Internet Data Center, Internet Data Center).
[0130] The following will be based on Figure 4a The system shown is used to introduce the protection method provided by the embodiment of the present invention, such as Figure 4b As shown, a traffic ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com