A Trusted Boot Method Based on Joint Full Disk Encryption of Firmware and USBKey
A full-disk encryption and firmware technology, applied in computer security devices, internal/peripheral computer component protection, instruments, etc., can solve problems that do not involve the joint full-disk encryption method, reduce the cost of the whole machine, protect user data, and prevent being hacked The effect of stealing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0088] The implementation of the present application will be described in detail below in conjunction with the accompanying drawings and embodiments, so as to fully understand and implement the implementation process of how the application uses technical means to solve technical problems and achieve technical effects.
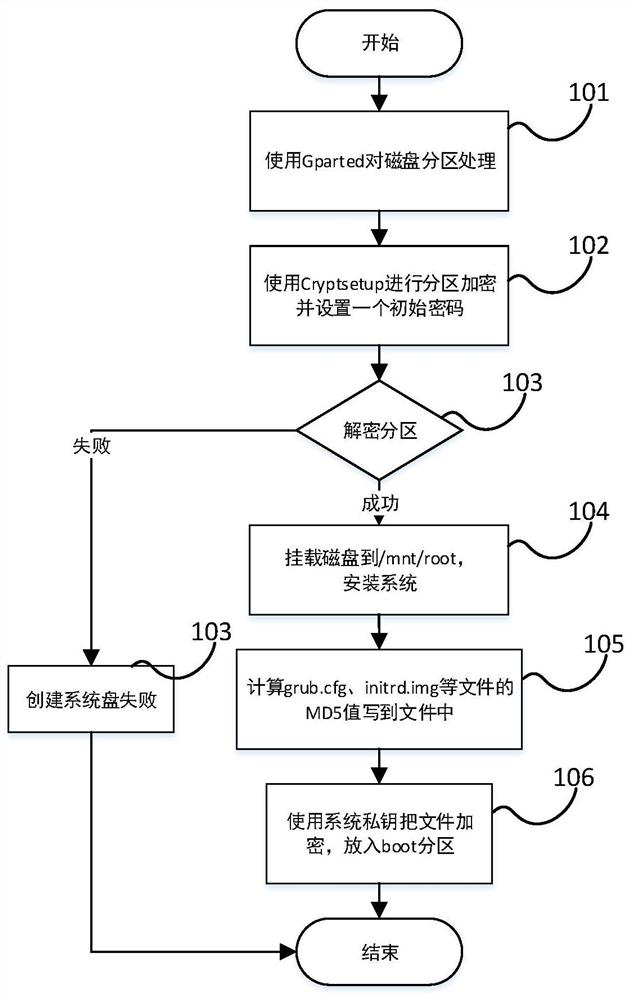
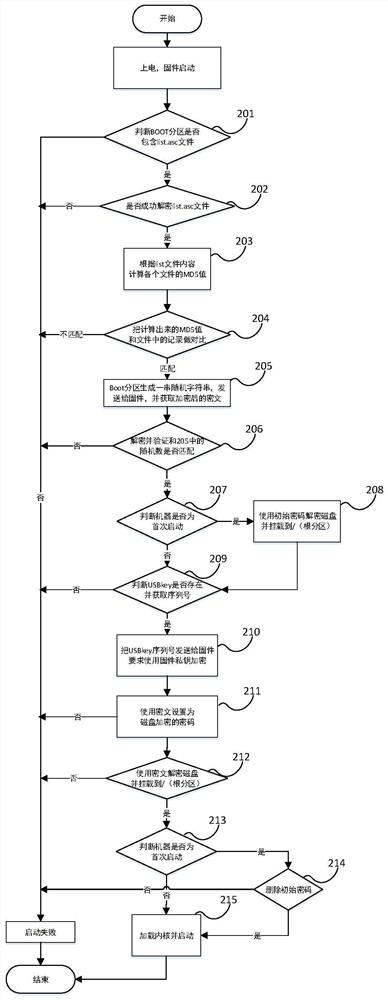
[0089] A trusted boot method based on the joint full disk encryption of firmware and USBkey includes the following steps: firmware preparation, boot partition preparation, installation preparation, and boot trusted boot. Among them, the power-on credible startup includes two processes: the first-time credible startup and the non-first-time startup credible startup.
[0090] (1) Firmware preparation: Save a public key provided in advance in the firmware to decrypt the files in the boot partition; the firmware also needs to save its own private key to respond to the private key encryption request of the system; in addition, the firmware has an MD5 value Calculation fu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com