A Role and Trust Based Access Control Approach for Hadoop
An access control and role technology, applied in the field of role and trust-based access control, can solve problems such as inability to ensure, and achieve the effect of a reliable access control mechanism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, so that the advantages and features of the present invention can be more easily understood by those skilled in the art, so as to define the protection scope of the present invention more clearly.
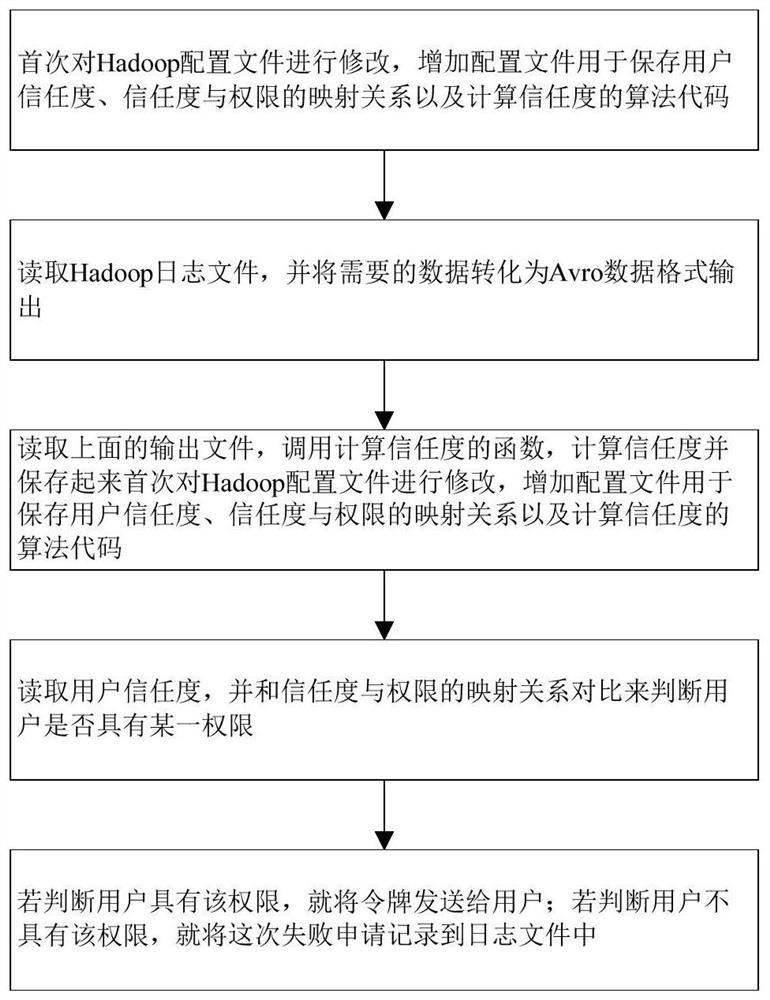
[0021] Such as figure 1 As shown, a role-based and trust-based access control method for Hadoop includes the following steps:
[0022] S1, the Hadoop configuration file was modified for the first time, and the configuration file was added to save user trust, the mapping relationship between trust and authority, and the algorithm code for calculating trust. The configuration files were all stored in the hard disk (using 5 i3-2130CPUs , build a cluster with a computer with 4GB of memory);
[0023] S2, read the Hadoop log file stored in the hard disk, and convert the required data into Avro data format output and save it in HDFS (Hadoop file system...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com