WEB application security protection method based on automatic learning
An application security and automatic learning technology, applied in the computer field, can solve problems such as false positives and inability to defend against unknown vulnerabilities, and achieve the effect of low false positives and false positives.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
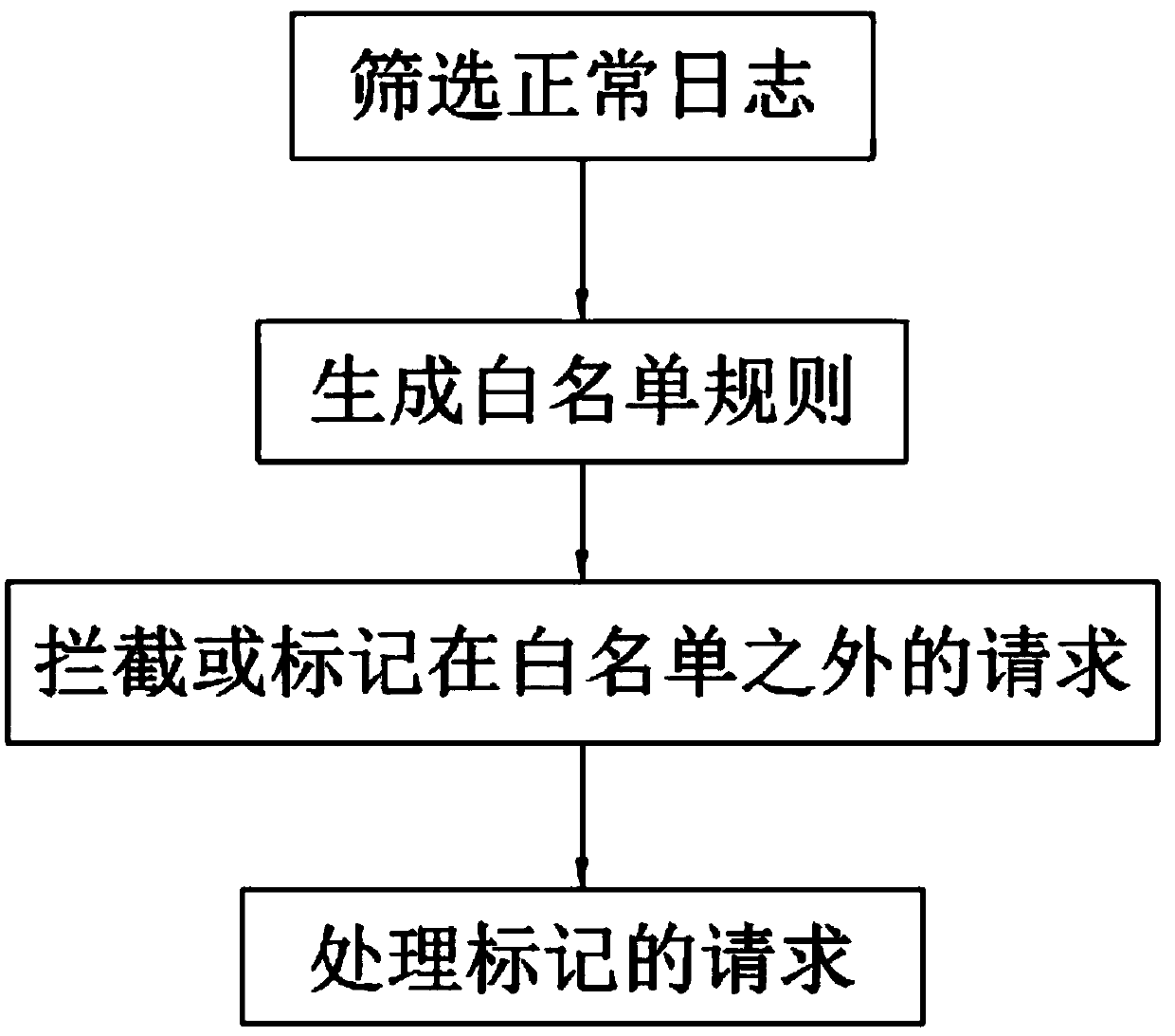
[0023] Such as figure 1 As shown, a WEB application security protection method based on automatic learning includes the following steps:
[0024] Step 1: Extract the access log of the WEB application from the WEB server or the traditional WAF device, and filter the log of non-attack requests;
[0025] The screening method is to use scripts to match keywords, filter attack requests, and filter out attack logs in WAF logs, or manually identify them one by one to determine whether they are attacks.
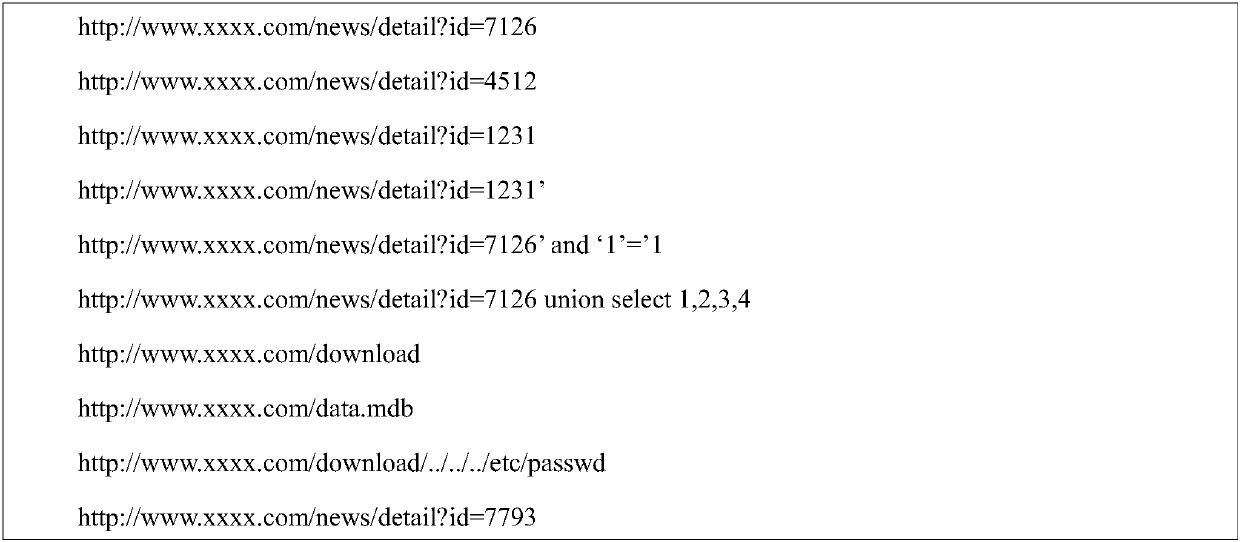
[0026] For example: URL collection:
[0027]
[0028] The set of attack request URLs can be filtered out through the above screening methods:
[0029]
[0030]
[0031] Step 2: According to the fields of URL, Cookie, Referer and other custom records in the logs filtered out in Step 1, a set of regular expressions with specific rules is gen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com