Intrusion monitoring method, intrusion monitoring device and equipment
A technology of terminal equipment and gateway equipment, applied in the computer field, can solve the problems of monitoring blind spots and inability to monitor blind spots in monitoring methods, and achieve the effect of quick intrusion alarm and optimized applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
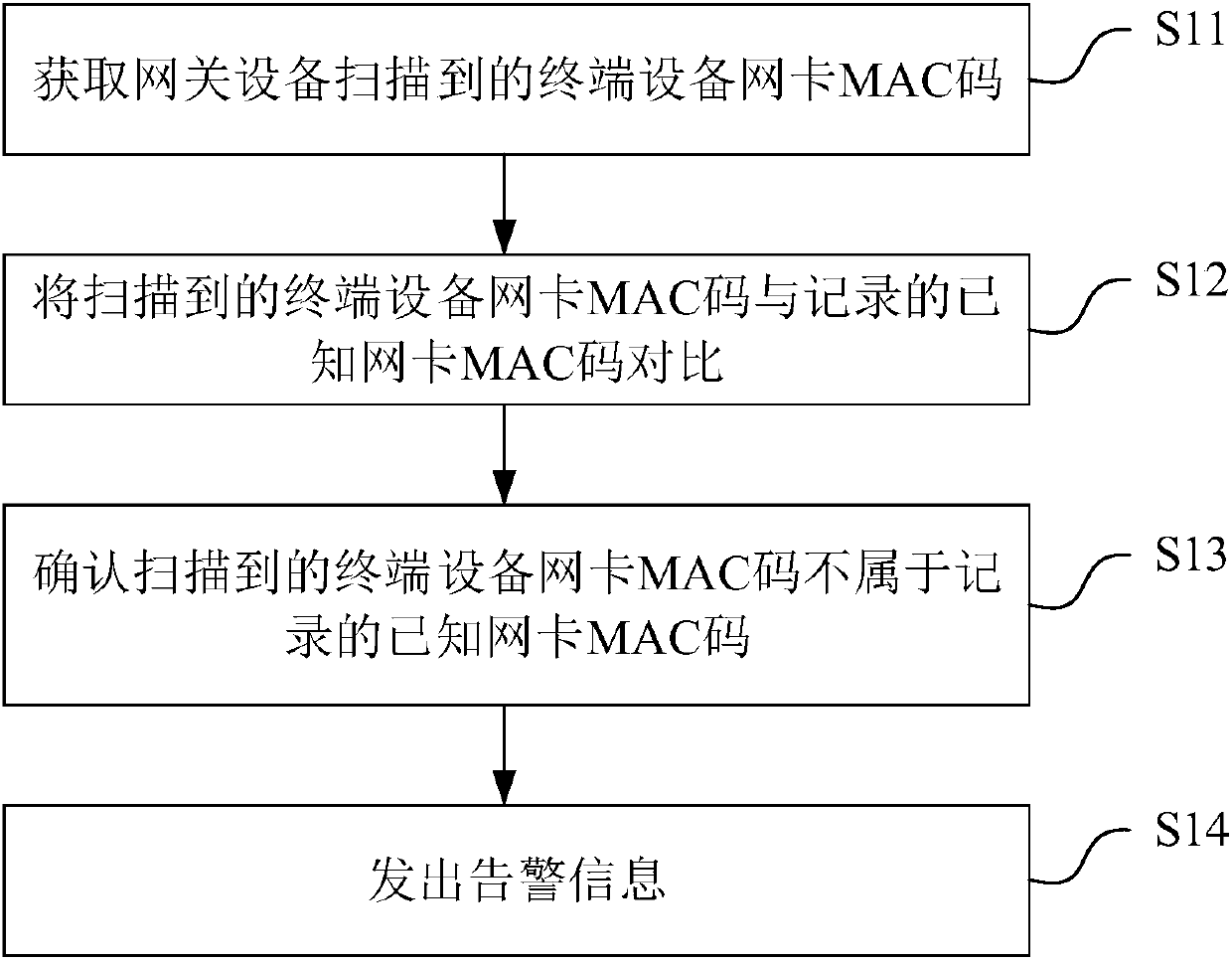
[0056] For further explanation to the intrusion monitoring method of the present invention, please refer to figure 1 :
[0057] Wherein, this embodiment may be implemented on one device, or may be implemented on a system composed of several devices. Specifically, in this embodiment, the device implemented is named after a master controller.
[0058] S11 acquires the MAC code of the network card of the terminal device scanned by the gateway device;
[0059] Specifically, a gateway (Gateway) device, also known as a network connector or a protocol transfer device, is a computer system or device that provides data conversion services between multiple networks. It can be said that a gateway device is a connector between different networks, and a device that needs to be "negotiated" when data is transferred from one network to another. Gateway devices enable them to be processed by another system by repackaging information. In this regard, gateway devices also have the ability to ...
Embodiment 2
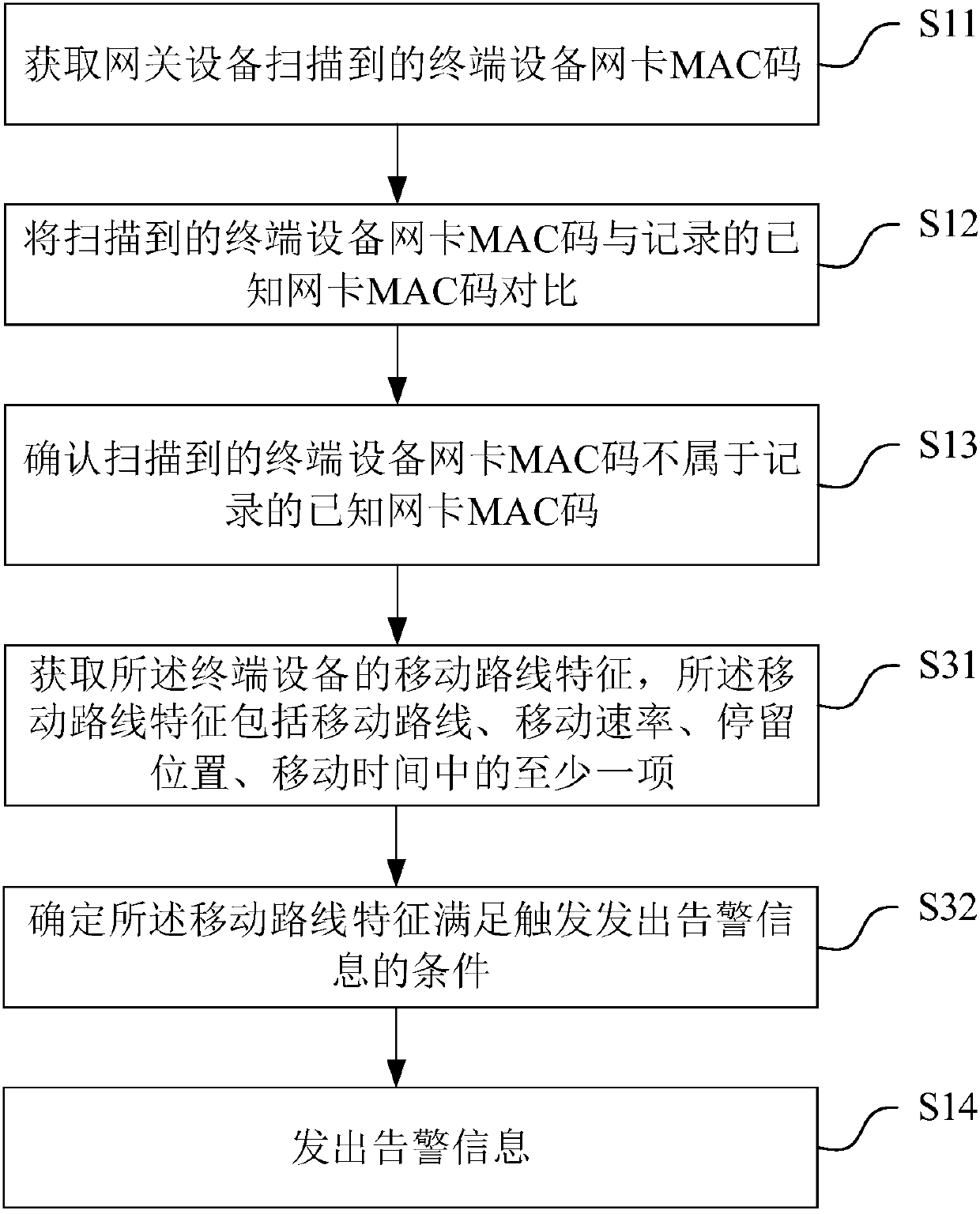
[0081] Different from the intrusion monitoring method described in Embodiment 1, combining image 3 , in this embodiment, before sending out the warning information, the following steps are also included:
[0082] S31 Acquiring the moving route characteristics of the terminal device, the moving route characteristics including at least one of moving route, moving speed, staying position, and moving time;
[0083] Specifically, those skilled in the art know that the feature of the moving route can be obtained through prior art detection, for example, according to the data obtained by the gateway device from the terminal device to connect to the gateway device, the data is processed to obtain the location of the terminal device; In addition, other detection techniques can also be used to obtain the characteristics of the moving route. The moving route is the path that the terminal device moves after entering the coverage area of the gateway device. It is mainly used to confirm...
Embodiment 3
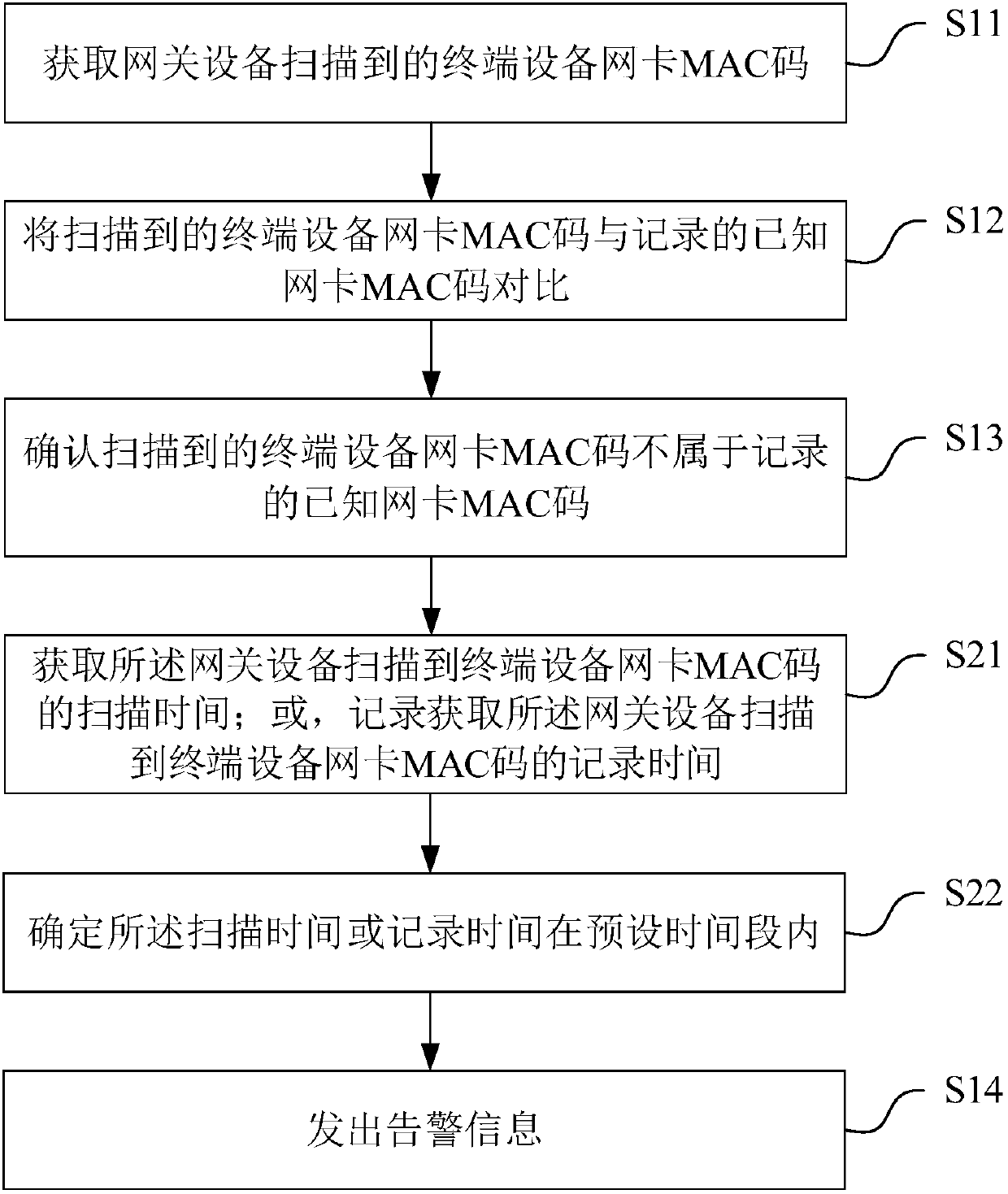
[0100] Different from the above-mentioned embodiments, in combination with Figure 4 , in this embodiment, the MAC code of the known network card is the MAC code of the authorized network card of the gateway device;
[0101] Specifically, the MAC code of the authorized network card is a MAC code of a network card that does not have a connection record with the gateway device but is allowed to access normally. For example, the gateway device is a newly installed device without any connection record at present, but the MAC code of the network card that allows normal access can be preset through the main controller.
[0102] After the step S11 obtains the MAC code of the network card of the terminal device scanned by the gateway device, it also includes:
[0103] S41 acquires the characteristics of the moving route of the terminal device;
[0104] The characteristics of the movement route are consistent with those described in Embodiment 2, and will not be described in detail h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com