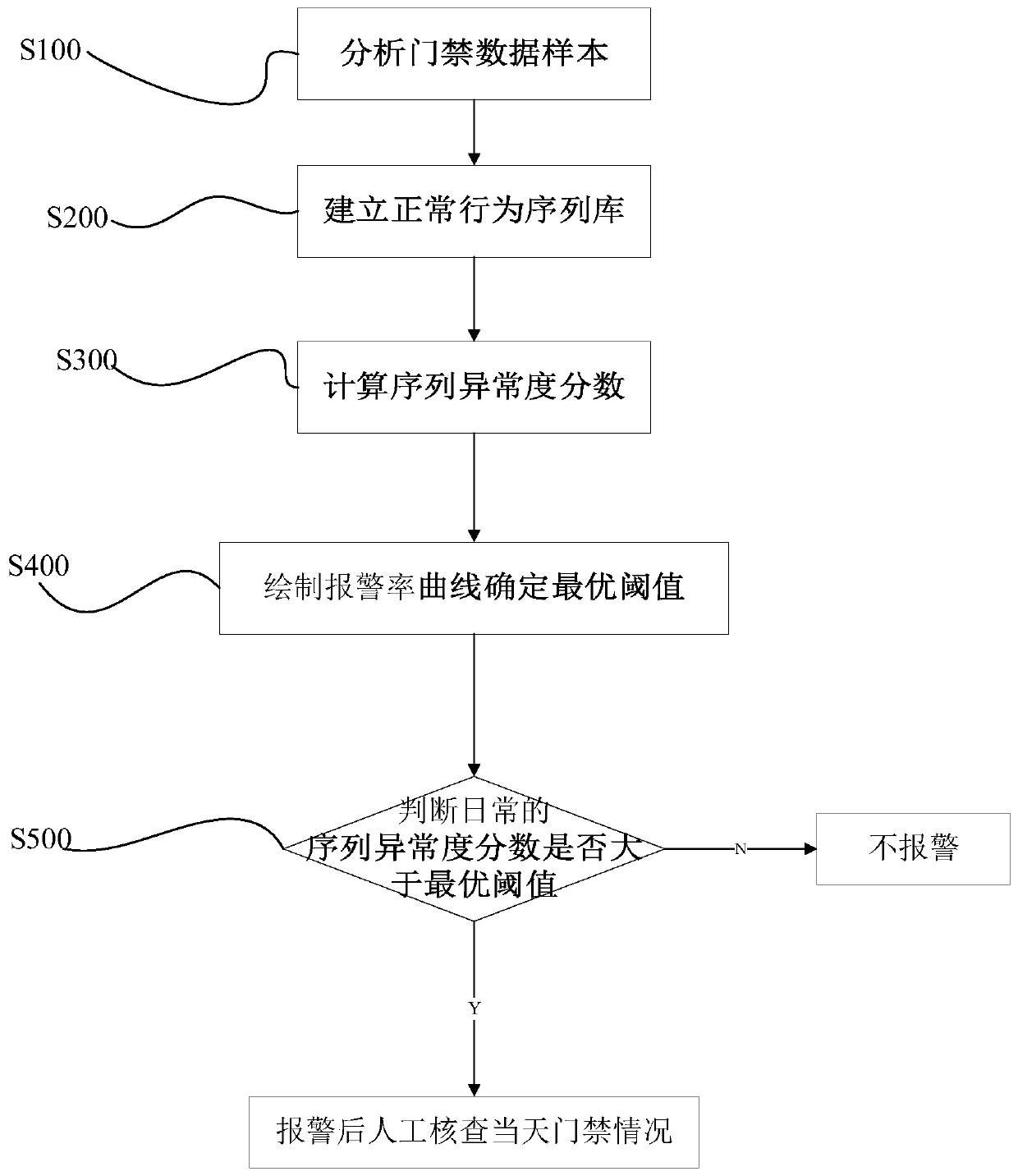
An Analysis Method of Insider Threat Abnormal Behavior Based on Access Control Log Mining
A behavior analysis and access control technology, applied in the field of data analysis, can solve the problems of low accuracy of detection results, achieve simple operation, reduce high false alarm rate, and improve accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
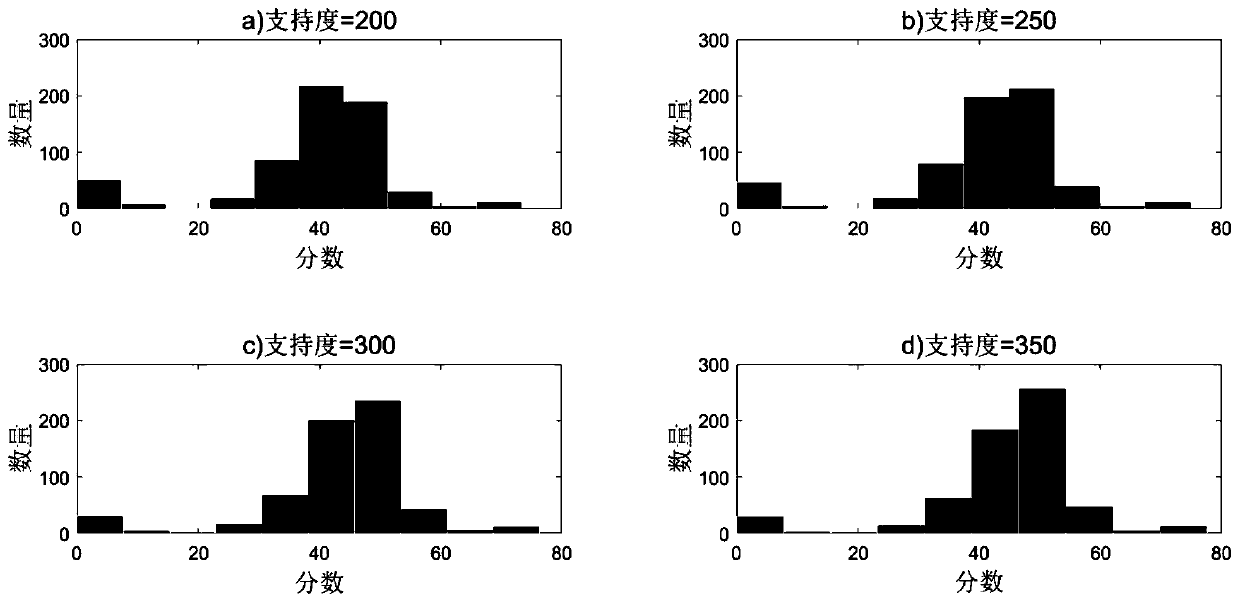
[0111] Analyze and detect the access control data of a certain department of a certain unit according to the above method, calculate the sequence anomaly score for the obtained test path sequence database, and obtain the results under different support degrees. The sequence anomaly score results are as follows image 3 shown. It can be seen from the figure that as the support increases, the calculated sequence anomaly score increases as a whole, the concentrated area of high segmentation advances to the right on the x-axis, and the calculated maximum score gradually increases.
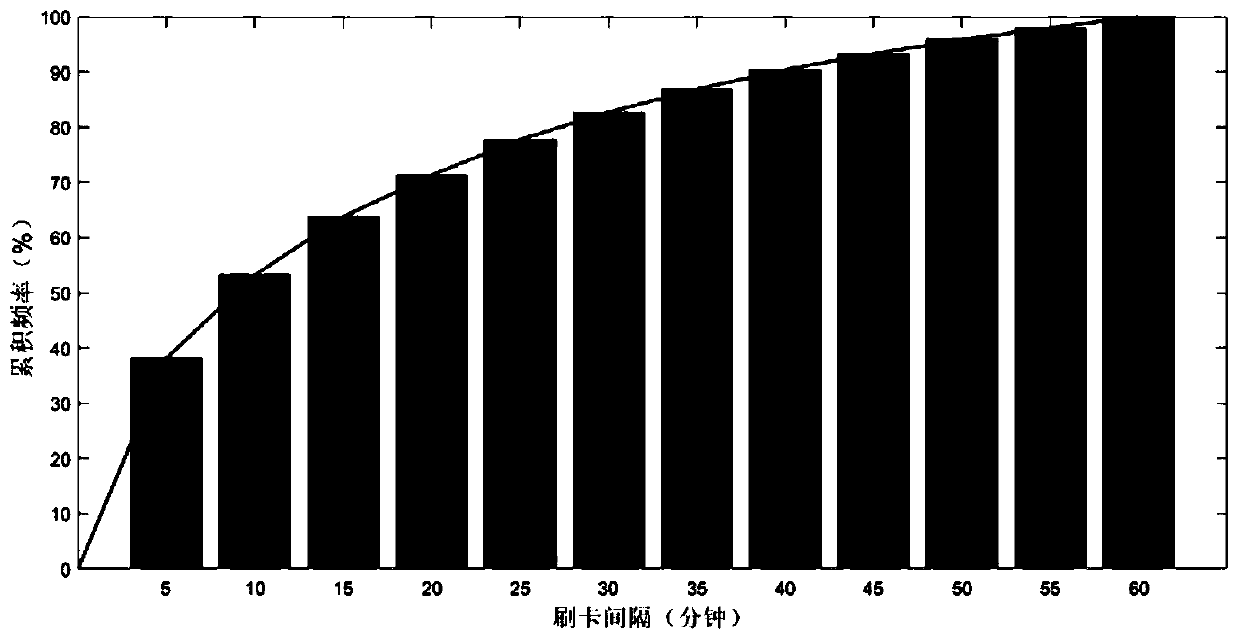
[0112] Figure 4 It is the alarm rate curve drawn according to the behavior scores of department personnel. It can be seen from the figure that with the gradual decrease of the current threshold (that is, the gradual increase of the difference), more and more abnormal behavior sequences are alarmed. Decision makers can according to The results in the figure are used to select the required threshold ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com