Data management method, device and system
A technology of data management and privacy data, applied in the field of information processing, can solve the problem that privacy users cannot effectively manage privacy data, and achieve the effect of authentic and reliable records
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
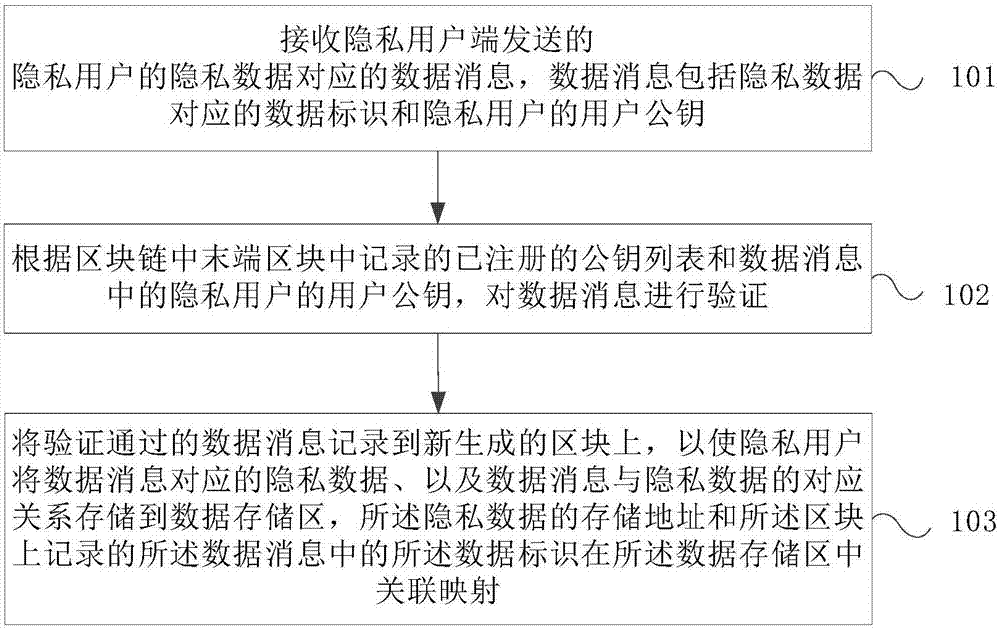
[0068] This embodiment provides a data management method for managing private data of private users. The execution subject of the data management method is a data management device, which can be set on a service terminal device, and the service terminal device can be any implementable terminal device such as a notebook computer, a mobile phone, a tablet, a server, and the like. Blockchain technology is used on this terminal device. The blockchain is a decentralized distributed database system that is jointly maintained by all nodes in the blockchain network. The nodes in the blockchain network can be called blockchain nodes. The blockchain network is based on P2P (Peer to Peer, peer to peer network) network, the service terminal device can be used as a blockchain node in the blockchain network. The specific blockchain data writing is an existing technology and is not limited here.
[0069] Such as figure 1 As shown, it is a schematic flow chart of the data management method...
Embodiment 2
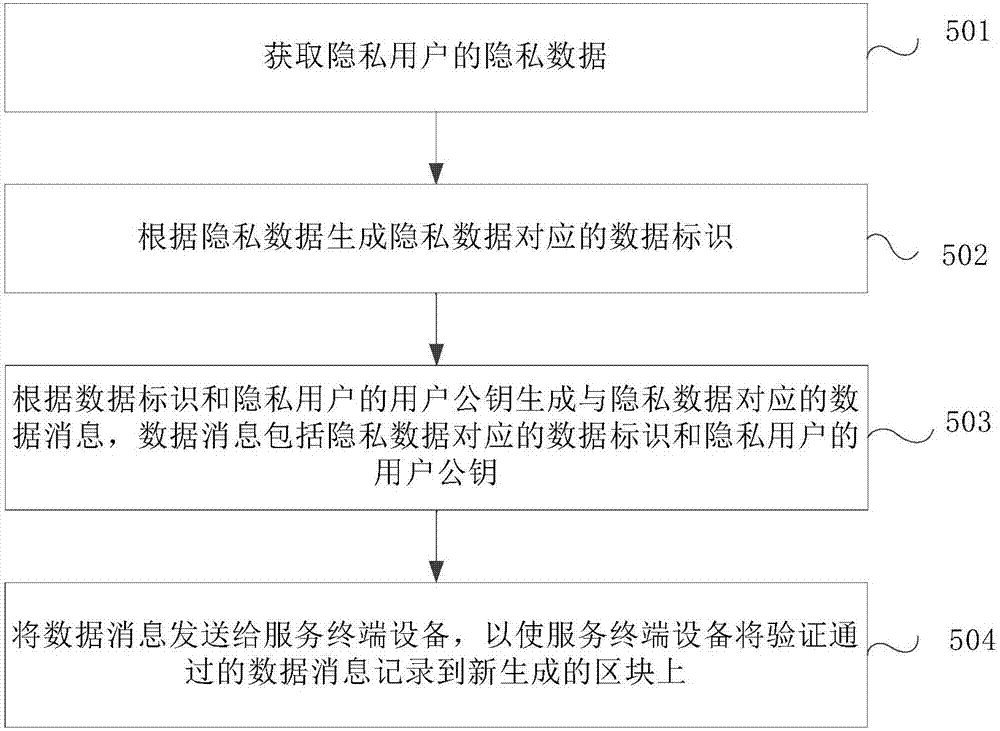
[0081] This embodiment provides a further supplementary description of the data management method provided in the above embodiments.
[0082] On the basis of the foregoing embodiments, after step 103, the method further includes:
[0083] Step 201, receiving a data access request of the accessing user sent by the accessing client, the data access request includes the data identifier corresponding to the private data to be accessed and the user public key of the accessing user.
[0084] Specifically, the data management device in the service terminal device may receive the access user's data access request sent by the access client, and the data access request includes the data identifier corresponding to the private data to be accessed and the user public key of the access user. The visiting user terminal may be the user terminal equipment of the visiting user, or an application program in the user terminal equipment used by the visiting user. The user terminal device of the ...
Embodiment 3
[0092] This embodiment provides a further supplementary description of the data management method provided in the above embodiments.
[0093] On the basis of the foregoing embodiments, before step 201, the method further includes:
[0094] Step 301, receiving the authorization message of the privacy user sent by the privacy client, the authorization message includes the message type with the authorization identifier, the user public key of the privacy user, the data identifier corresponding to the private data of the privacy user, and the user public key of the access user .
[0095] Step 302: Verify the authorization message according to the user public key of the privacy user, the user public key of the visiting user, and the registered public key list recorded in the end block of the blockchain.
[0096] Step 303, recording the verified authorization message in the access right list, so as to register the private data access right.
[0097] Specifically, when the access u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com