Access mode leakage prevention data safety isolation and sharing realization method
A data security and access mode technology, applied to electrical components, transmission systems, etc., can solve problems such as being hacked, not hiding user access modes, and difficult data sharing between users, so as to achieve the effect of ensuring safe isolation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] Below with reference to shown in accompanying drawing, the present invention is further described by specific embodiment:
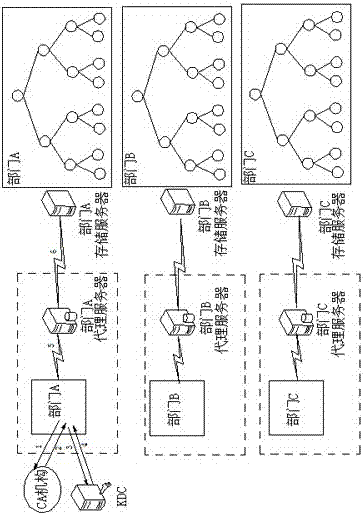
[0016] A method for implementing data security isolation and sharing that is resistant to access mode leakage. The method implements data security isolation and sharing with the help of proxy encryption technology on the basis of physical isolation, and changes the original storage form of data. Ensure that the access mode is not disclosed during the data access process, thereby successfully protecting user privacy. The above three parts work together to build a data security isolation and sharing implementation method that resists access mode leakage.
[0017] In order to avoid the risk of resource isolation being breached by mechanisms such as SELinux-sVirt, each department that requires data isolation is allocated one or more independent physical servers to achieve physical isolation and ensure the security isolation of data between departments ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com