Identity-based secret key negotiation construction method and network platform
A key negotiation and construction method technology, which is applied to key distribution, can solve the problems of increasing the amount of calculation for users, the inability to calculate the session key, and the inability to set the session key, etc., to achieve simplified use and management, and high security Good results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
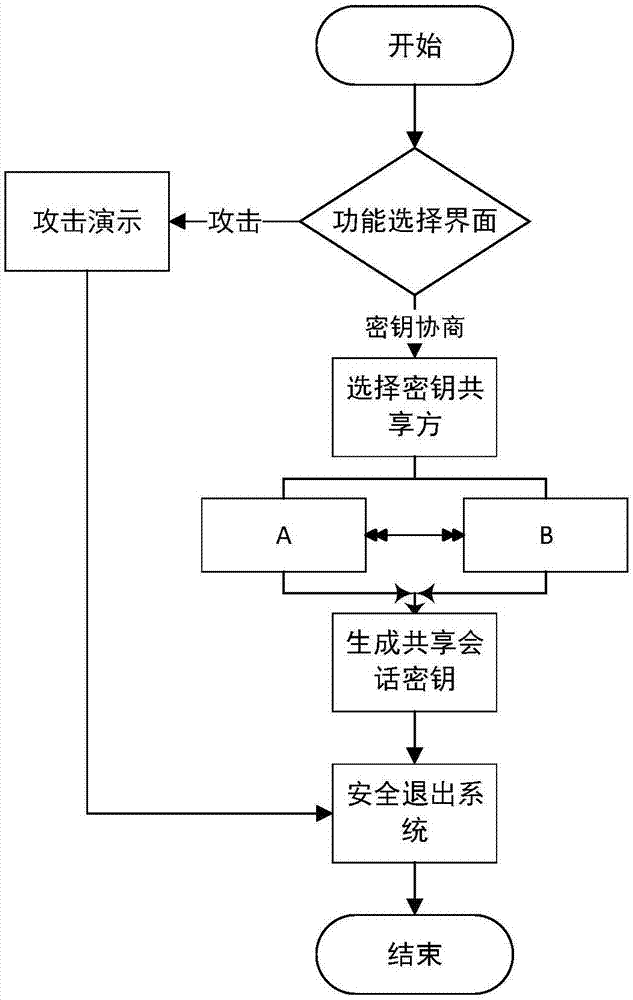
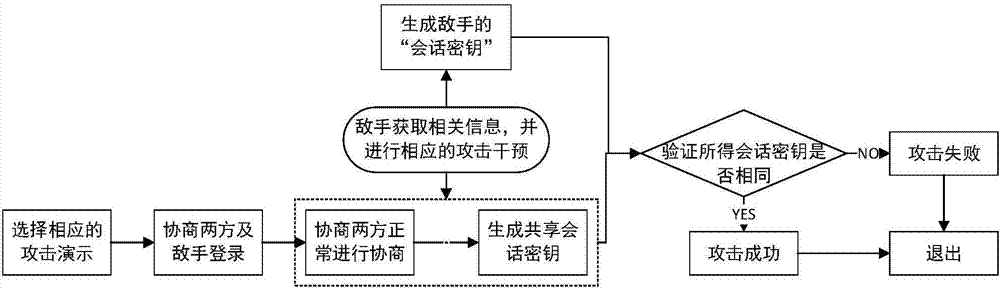
[0105] In this embodiment, the identity-based two-party key agreement protocol is implemented in the form of a website, and the security of the protocol is demonstrated on the website, as follows:
[0106] (1) A new identity-based two-party key agreement protocol.
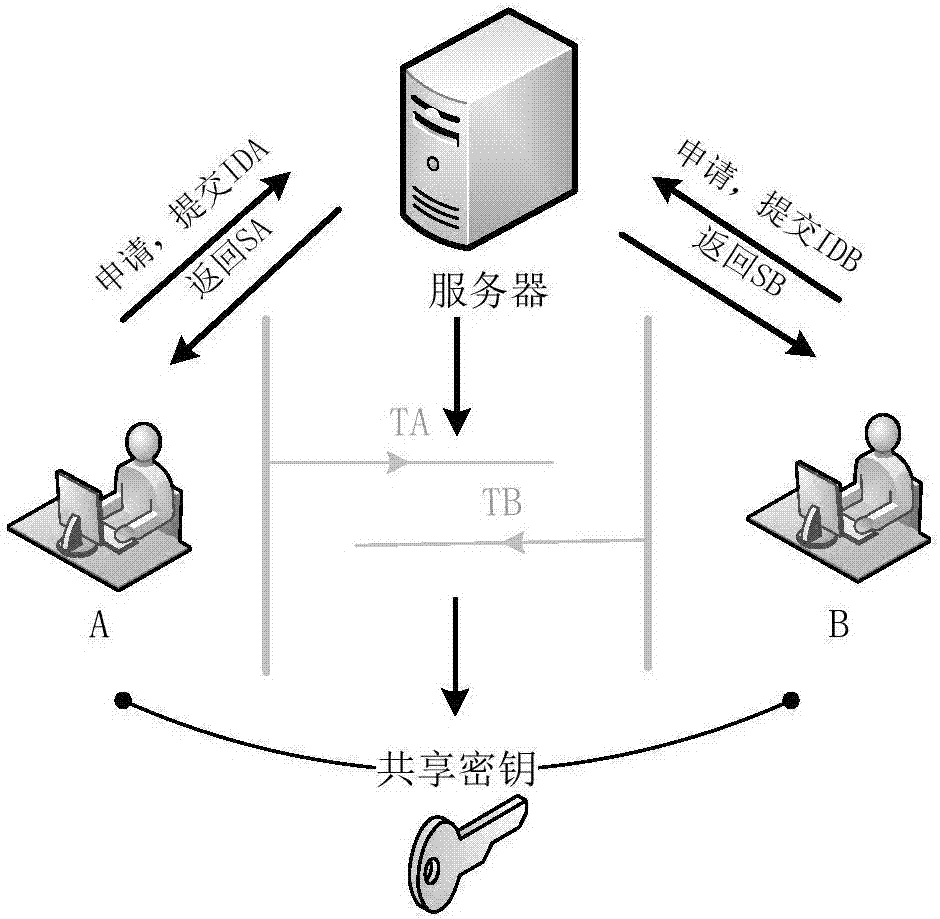
[0107] The algorithm mainly involved in the protocol is an identity-based key agreement scheme. The identity-based key agreement scheme is composed of three stages: system establishment, key extraction (user's public and private keys), and key agreement. Based on Weilpairing.Electronics Letters, 2003,39(8):653-654.) The improvement of the identity-based key agreement scheme proposed, the schematic diagram of the identity-based key agreement system is shown in figure 1 , the specific steps of the whole process are as follows:
[0108] (1) System establishment: public system parameters: {G 1 ,G T ,p,e,P,P pub ,H 1 ,H 2}, keep the master private key s;
[0109] Among them, G 1 : is the additive cyclic group g...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com