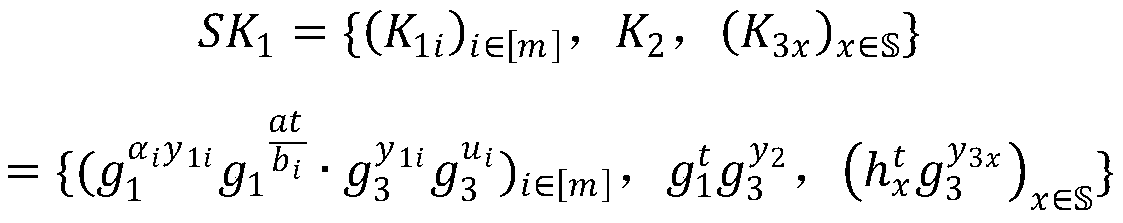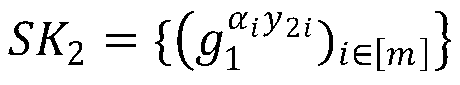Anti-leak cp-abe method under policy hiding and outsourced decryption
A CP-ABE and policy technology, applied in the field of information security, can solve problems such as unavoidable side channel attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention is described in further detail now in conjunction with accompanying drawing.
[0045] The CP-ABE scheme proposed by the present invention has three characteristics of anti-leakage, policy hiding and outsourcing decryption. Its use process includes the following five algorithm steps:
[0046] (1) Initialization algorithm (λ, Σ):
[0047] The initialization algorithm inputs a security parameter λ, an attribute space Σ, Σ is the name of the attribute space, which represents all attribute sets, and each attribute can be mapped to a group An element in , U=|Σ| is the size of the attribute space, and m is the number of shares of the key, which is related to the security of the algorithm. The algorithm runs a bilinear group generator to generate where P 1 , P 2 , P 3 are three different large prime numbers, is a bilinear pairing operation, with is a multiplicative cyclic group with prime order N, yes the order is p i subgroup of . T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com