A method for operating platform data
An operation method and platform technology, applied in the fields of electrical digital data processing, platform integrity maintenance, instruments, etc., can solve the problems of not necessarily protecting the platform, large strategies, and unpredictable eavesdropping methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In the following description, reference is made to the accompanying drawings, which illustrate several specific embodiments by way of illustration. It will be understood that other embodiments can be conceived and can be made without departing from the scope or spirit of the present disclosure. Therefore, the following detailed description should not be considered in a limiting sense.
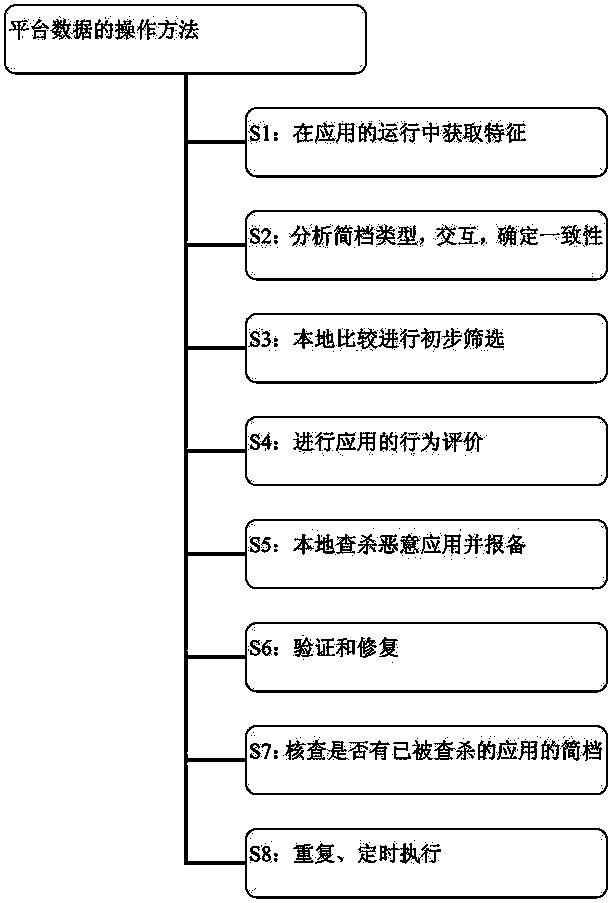
[0021] According to an exemplary embodiment of the present invention, figure 1 A flowchart illustrating a method for operating platform data.
[0022] In step S1, the feature is acquired during the running of the application on the platform;
[0023]In step S2, the platform analyzes the profile type and interacts with the remote device to determine consistency;
[0024] In step S3, for target applications that do not conform to consistency, the platform conducts preliminary screening of suspicious target applications through local comparison;
[0025] In step S4, for the target appli...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com