Character configuration method and device
A configuration method and role technology, applied in the Internet field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0032] According to an embodiment of the present invention, a method embodiment of a role configuration method is provided.
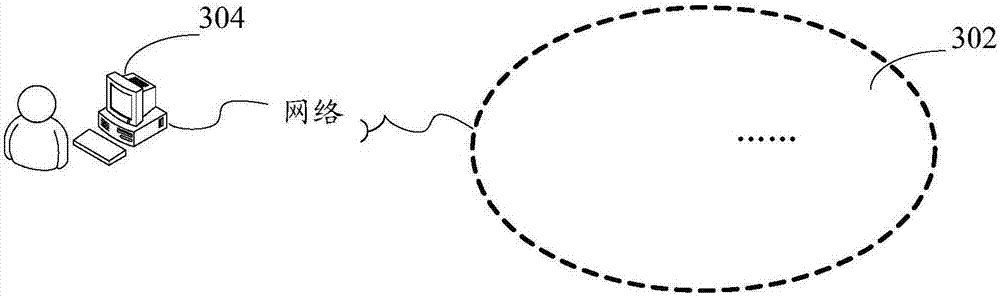
[0033] Optionally, in this embodiment, the above role configuration method can be applied to image 3 In the hardware environment constituted by the server 302 and the terminal 304 as shown. Such as image 3 As shown, the server 302 is connected to the terminal 304 through a network. The above-mentioned network includes but not limited to: a wide area network, a metropolitan area network or a local area network. The terminal 304 is not limited to a PC, a mobile phone, a tablet computer, and the like. The method in this embodiment of the present invention may be executed by the server 302 , may also be executed by the terminal 304 , and may also be executed jointly by the server 302 and the terminal 304 . Wherein, the method for executing the embodiment of the present invention by the terminal 304 may also be executed by a client installed on it.
[0...
Embodiment 2
[0089] According to an embodiment of the present invention, a device for configuring a role for implementing the above method for configuring a role is also provided. Figure 9 is a schematic diagram of an optional role configuration device according to an embodiment of the present invention, such as Figure 9 As shown, the device may include: a detection unit 92 , a first acquisition unit 94 and a configuration unit 96 .
[0090] The detection unit 92 is configured to detect a target event associated with the first character in the game, wherein the first character is a non-player character generated in the game using artificial intelligence to play against the player character, and the target event is used to indicate to modify the first character A character's target attribute value;
[0091]The first acquisition unit 94 is configured to acquire configuration information corresponding to the target event, wherein the configuration information is used to configure the secon...
Embodiment 3
[0119] According to an embodiment of the present invention, a server or terminal for implementing the above role configuration method is also provided.
[0120] Figure 10 is a structural block diagram of a terminal according to an embodiment of the present invention, such as Figure 10 As shown, the terminal may include: one or more (only one is shown in the figure) processors 1001, memory 1003, and transmission means 1005 (such as the sending means in the above-mentioned embodiments), such as Figure 10 As shown, the terminal may also include an input and output device 1007 .
[0121] Among them, the memory 1003 can be used to store software programs and modules, such as program instructions / modules corresponding to the character configuration method and device in the embodiment of the present invention, and the processor 1001 runs the software programs and modules stored in the memory 1003 to execute Various functional applications and data processing, that is, the config...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com