Application access authentication method, application access authentication system, application access authentication device and terminal
An application port and application client technology, applied in the field of application access authentication, can solve the problems of inapplicability of the authentication scheme, the absence of users and APPs, and the inability to flexibly deploy new applications and upgrade existing applications, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0083] In order to make the purpose, technical solution and advantages of the present invention more clear, the embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined arbitrarily with each other.
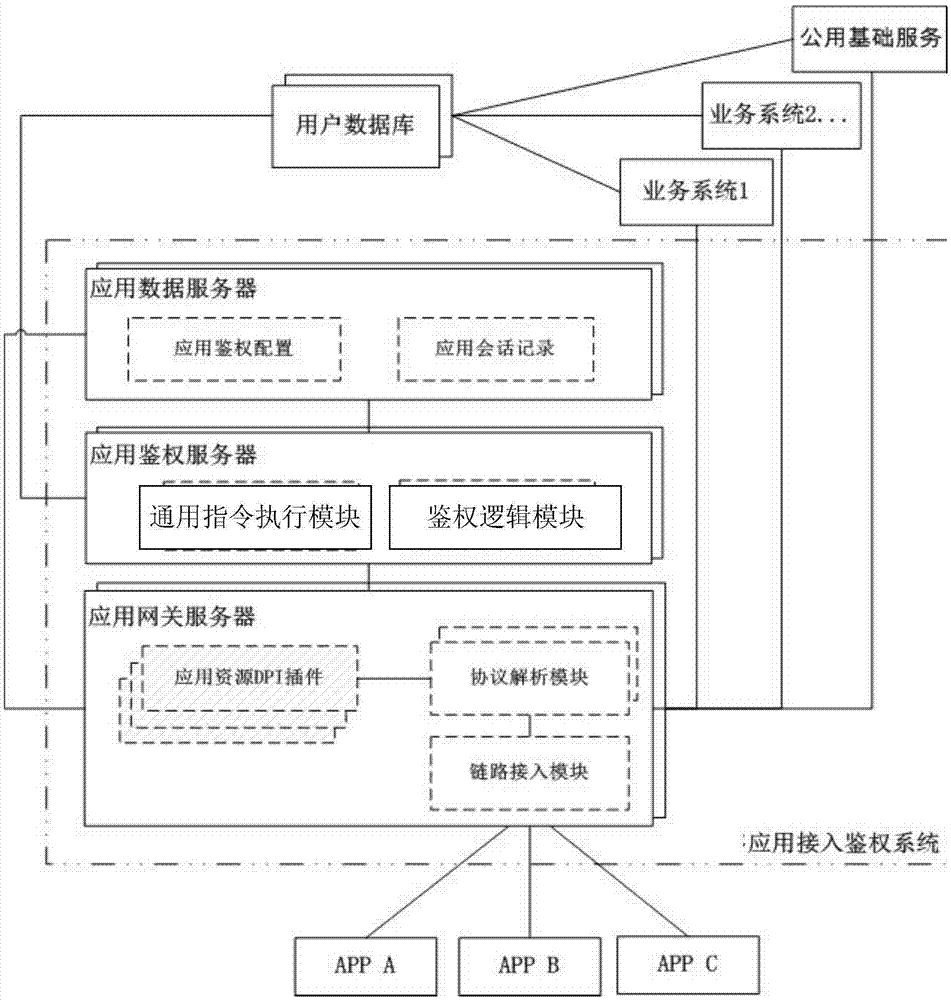
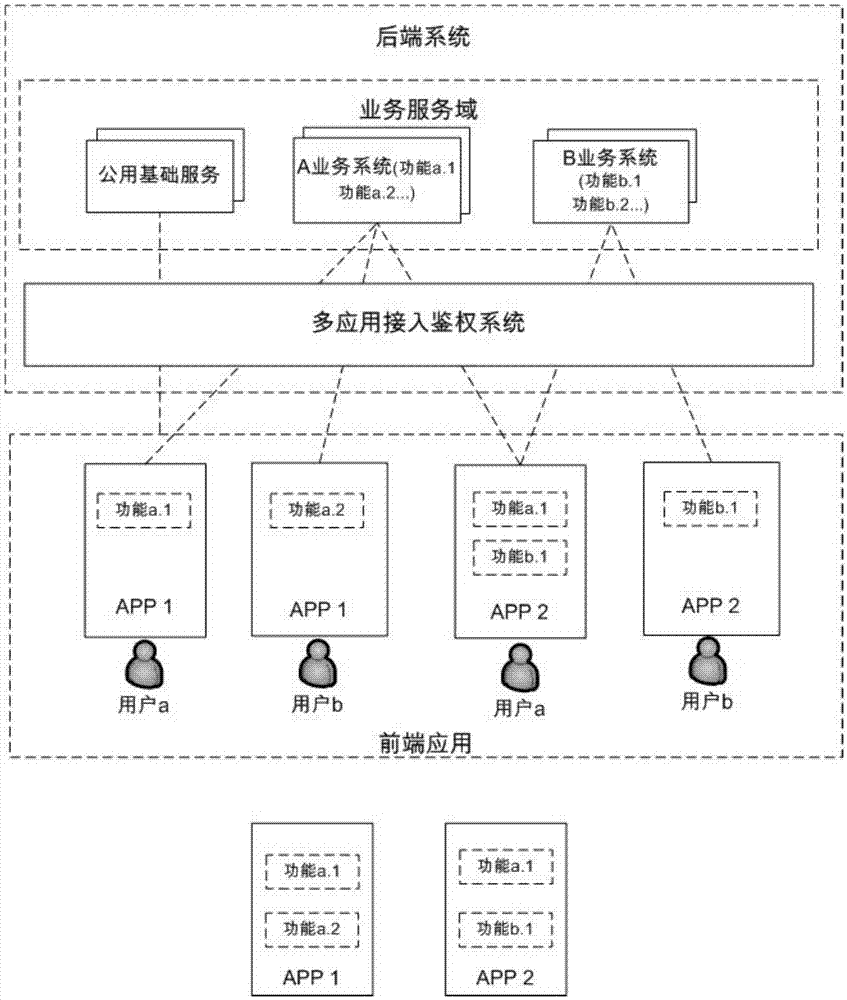
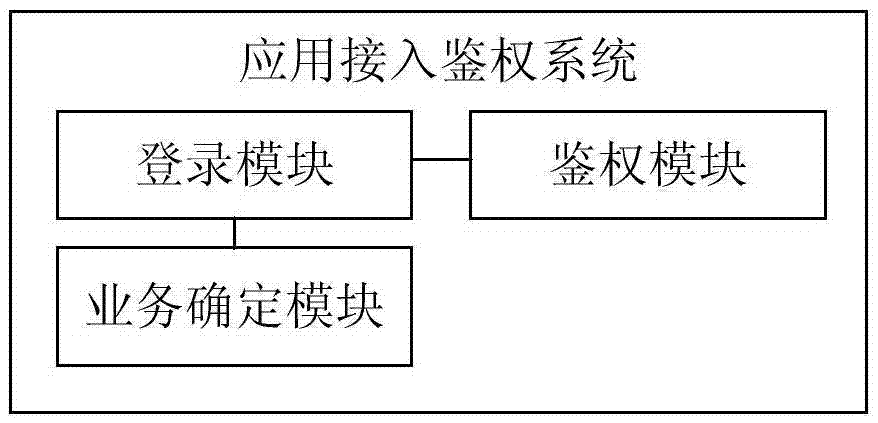
[0084] Through analysis and abstraction, the essence of the APP access system is that the client connects to one or more ports of the server to access one or more resources inside the server. The resources and access here have a broad meaning, as long as they can be accessed through the network API Any object can be considered as a resource, including not only data (for example, a contact list) or media (for example, a phone message, a video), etc., but also application ports, API interfaces or functions (for example, printing a fax), etc. , access not only refers to the usua...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com