A Ranking Verifiable Semantic Fuzzy Searchable Encryption Method
An encryption method and semantic technology, applied in the field of cloud computing, can solve problems such as the inability to achieve verifiable sorting, and the inability to verify whether the order of search results is correct.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
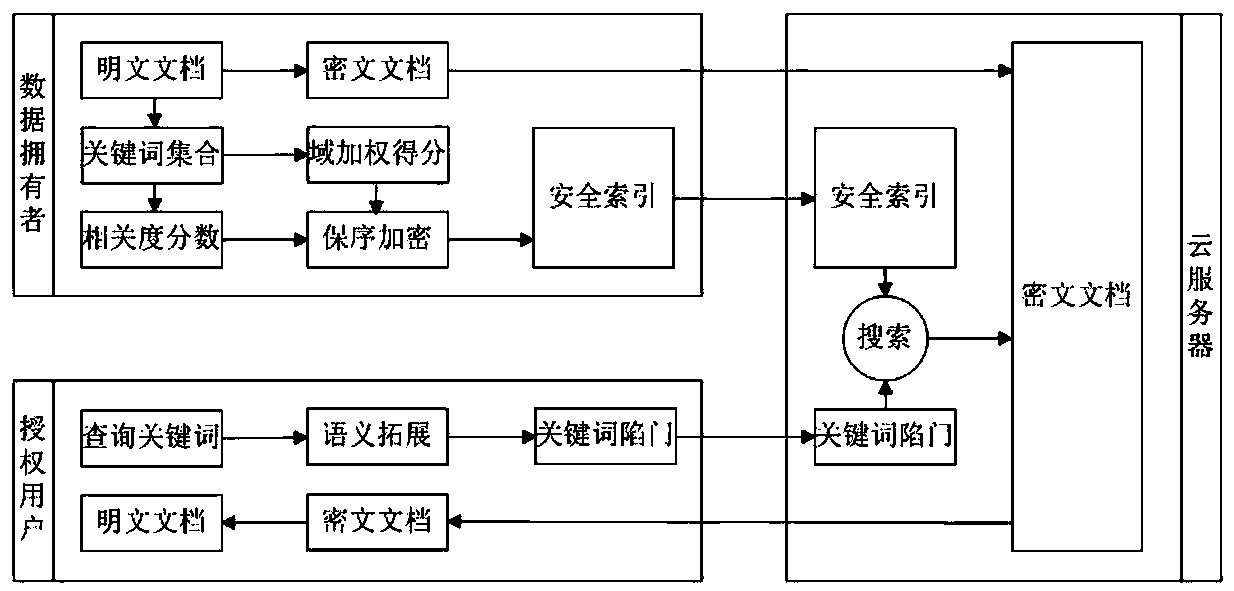
[0053] Such as figure 1 as shown, figure 1 It is the system framework of the embodiment of the present invention, including three entities: data owner, authorized user and cloud server. The basic operation process of this embodiment is as follows:
[0054] (1) KeyGen(λ): The data owner inputs a security parameter λ to generate the document encryption key sk, the key hk of the one-way hash function, and the key ek of the order-preserving encryption function. Send keys sk, hk to authorized users.
[0055] (2) Index (F, hk, ek):
[0056] a. Keyword extraction: data owner for document set F=(f 1 , f 2 ,..., f m ) to extract keywords, and get the keyword set W=(w 1 ,w 2 ,...,w n ).
[0057] b. Calculate correlation score: introduce the tf-idf weight calculation method to calculate keyword correlation score S.
[0058]
[0059] |f| indicates th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com