A method and system for identifying fake wifi using physical layer information
A physical layer information and physical layer technology, applied in wireless communication, security devices, network topology, etc., can solve the problems of reduced implementability, low security, and limited recognition scenarios, so as to achieve diverse use scenarios and improve security Sexuality, the effect of wide recognition scene
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] Below in conjunction with accompanying drawing, further describe the present invention through embodiment, but do not limit the scope of the present invention in any way.
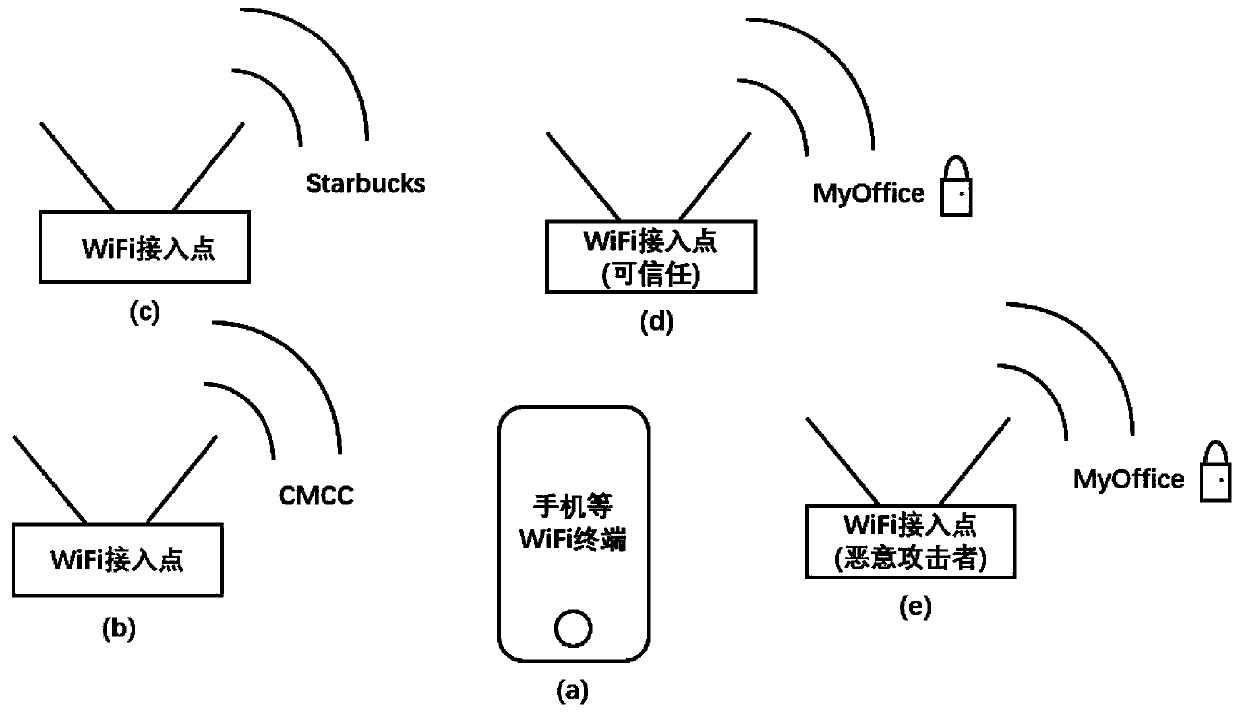
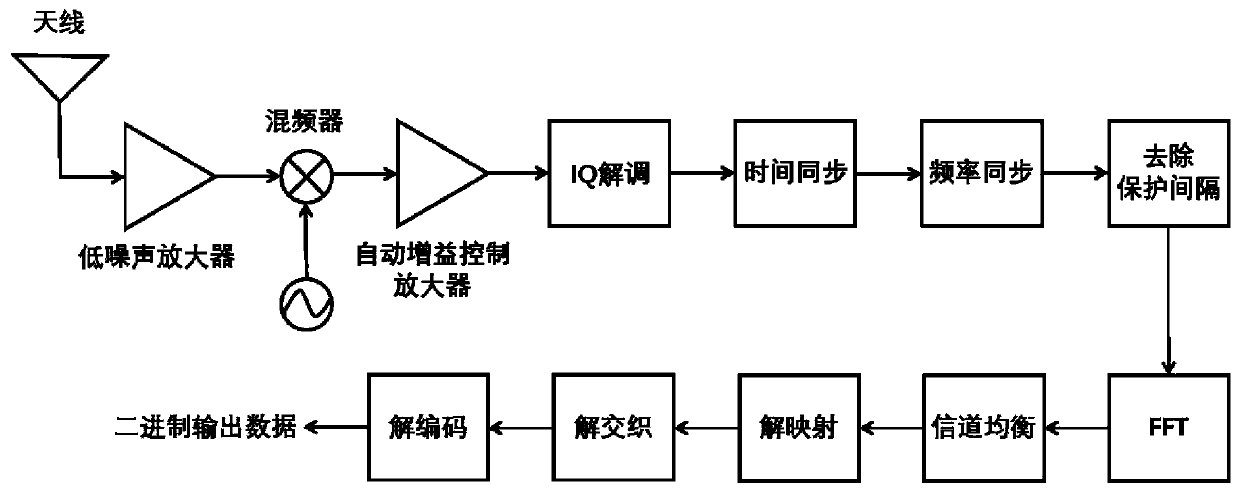
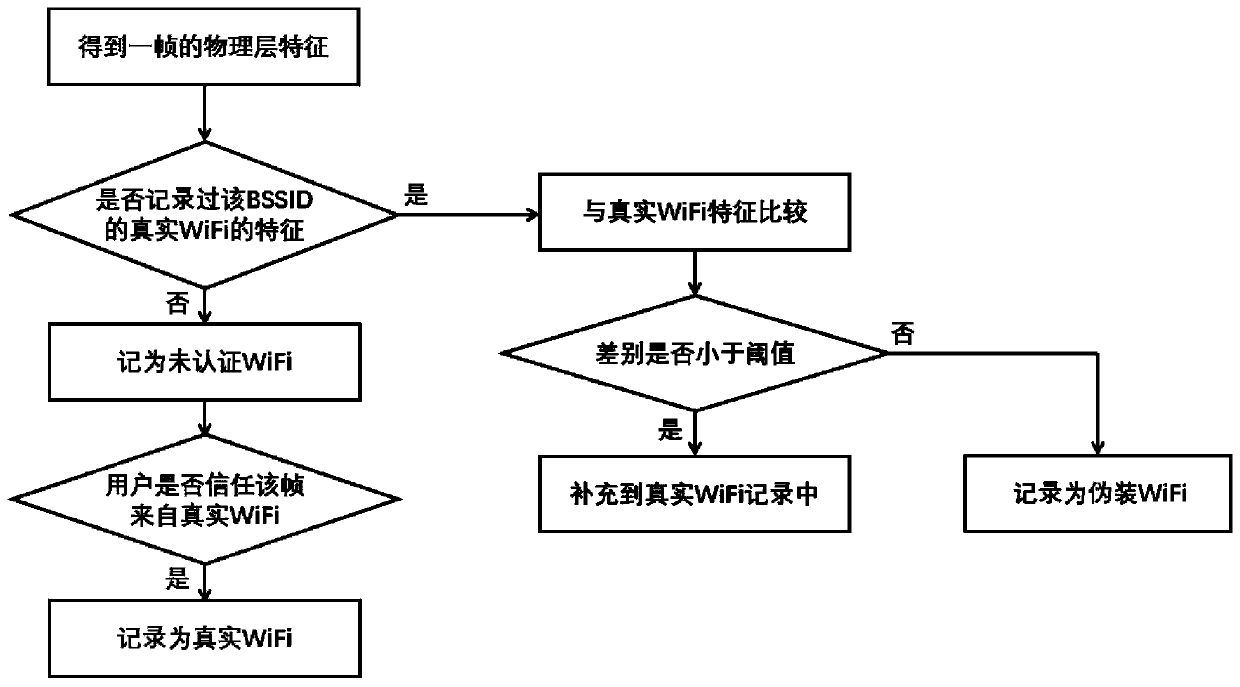
[0044] The present invention provides a method for identifying fake WiFi by using physical layer information, including a method for collecting physical layer information, a method for calculating physical layer characteristics, and a method for identifying fake WiFi; wherein, the method for collecting physical layer information is divided into Two steps, the first step is to select the appropriate physical layer information, the selection strategy is to select the information related to the equipment, and exclude the information related to other factors such as the environment, the selection result is the frequency offset of the received signal, the constellation point offset, and The correlation degree of the sent signal, the second step is to collect these physical layer information, the collection...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com