Authentication method and system
An authentication and character string technology, applied in the field of communication, can solve problems such as not being able to meet the higher requirements of authentication efficiency, and achieve the effect of preventing malicious imitation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
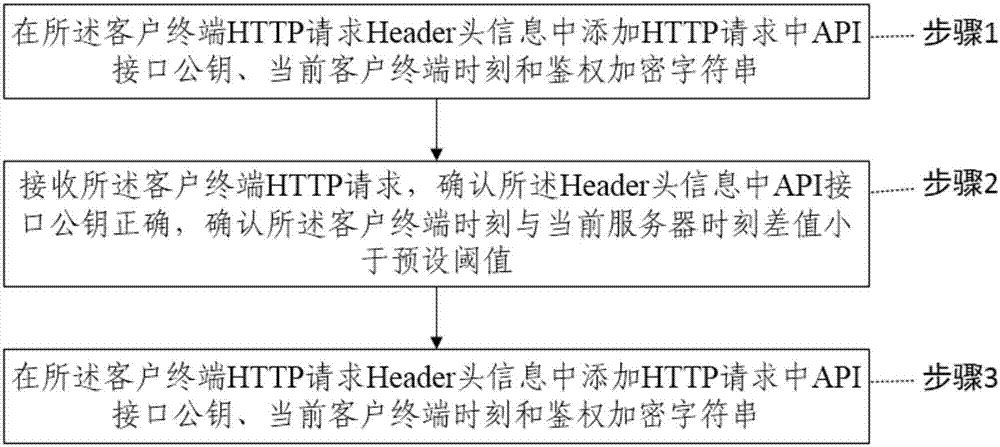
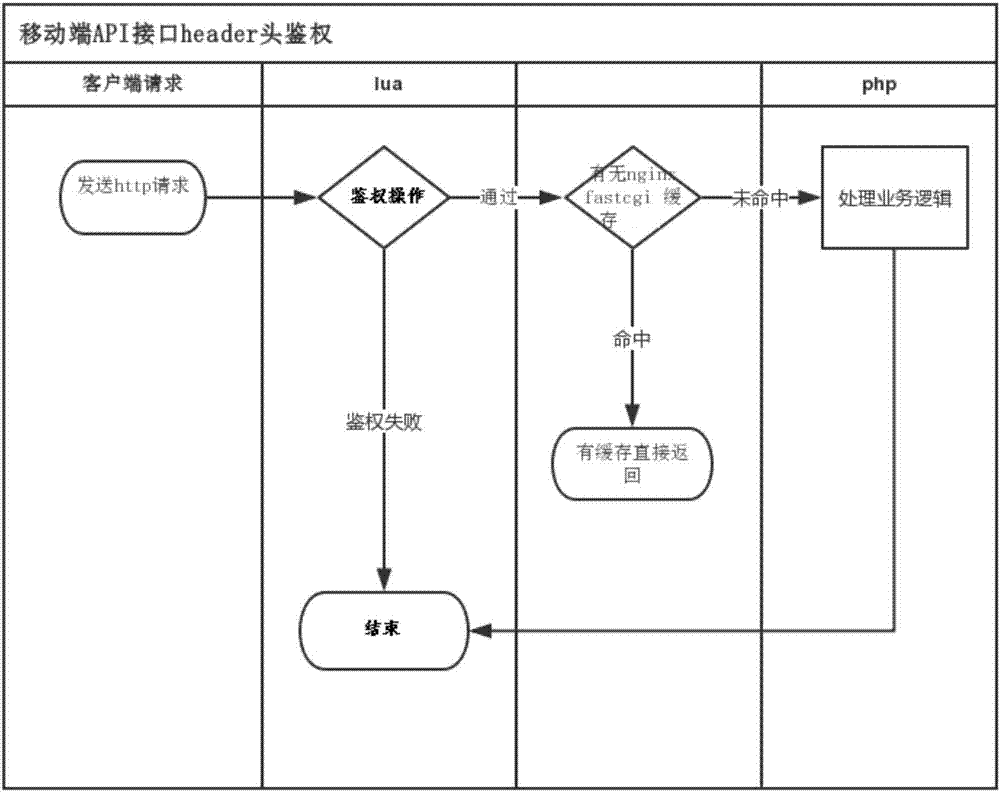
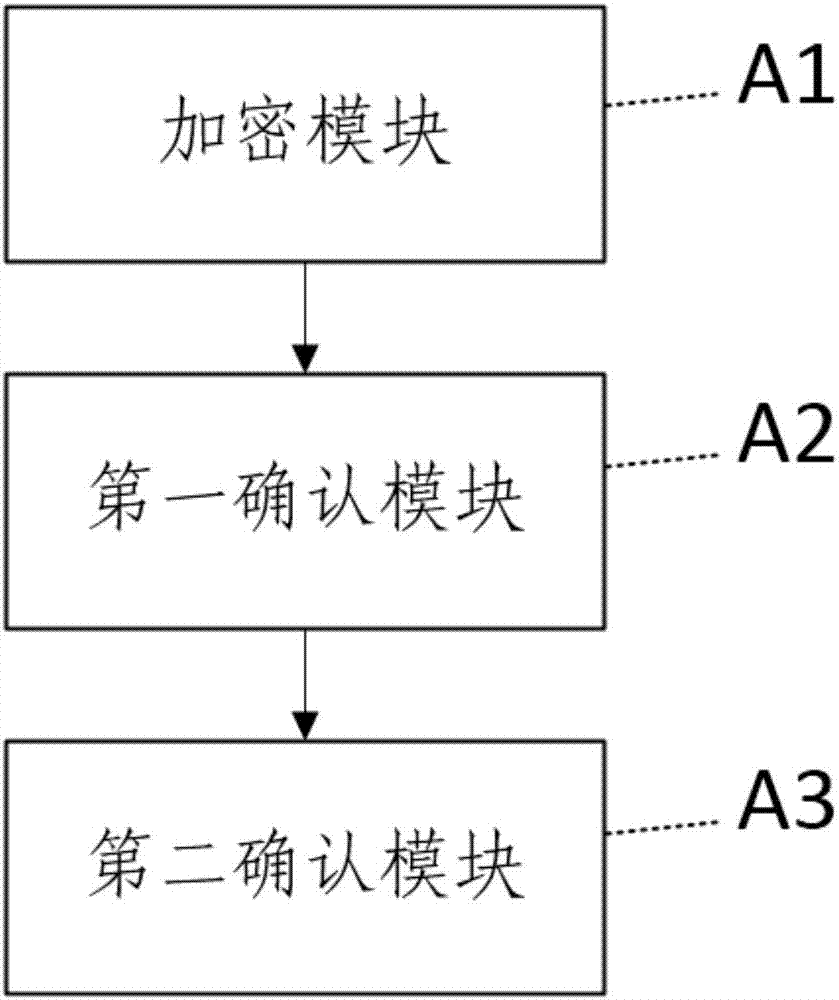
[0019] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
[0020] First, some technical terms involved in the specific embodiments of the present invention will be described.
[0021] HTTP: Request messages from client to server.
[0022] Header: Header header information carried in the HTTP request.
[0023] API (Application Programming Interface, application programming interface): It is some predefined functions, the purpose is to provide applications and developers with the ability to access a set of routines based on certain software or hardware without accessing source code, or understanding internal The details of the working mechanism.
[0024] The public key (Public Key) and the private key (Private Key) are a key pair...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com