Secure transmission method based on relay strategy selection and resource allocation in relay OFDM (Orthogonal Frequency Division Multiplexing) network
A technology of resource allocation and relay strategy, applied in the direction of advanced technology, electrical components, climate sustainability, etc., can solve poor performance, unfavorable users to receive data correctly, relay OFDM network security throughput does not take multi-user into account Issues such as the fairness of scheduling can be achieved to reduce the probability of security interruption and ensure the security of information transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be further described below in conjunction with the accompanying drawings.
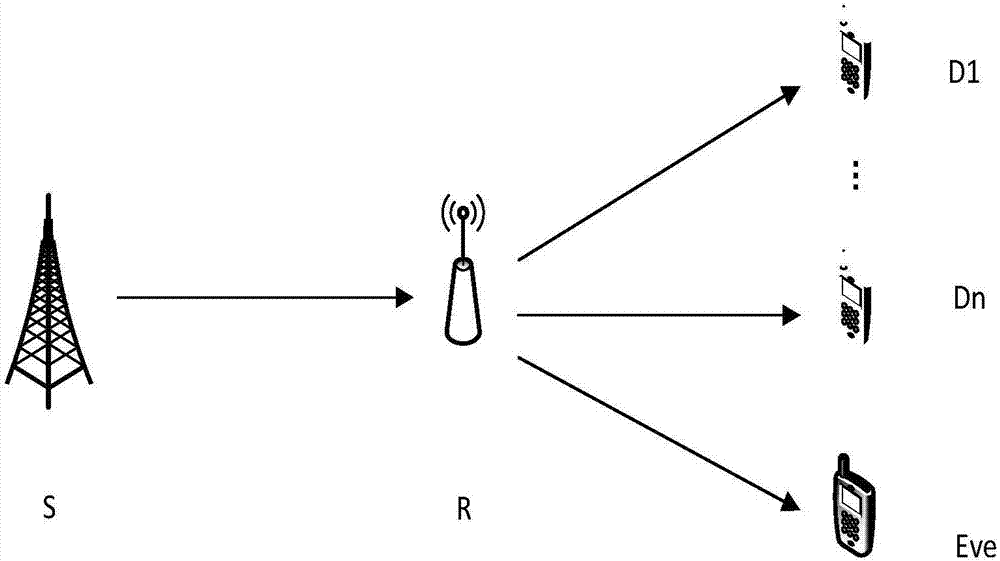
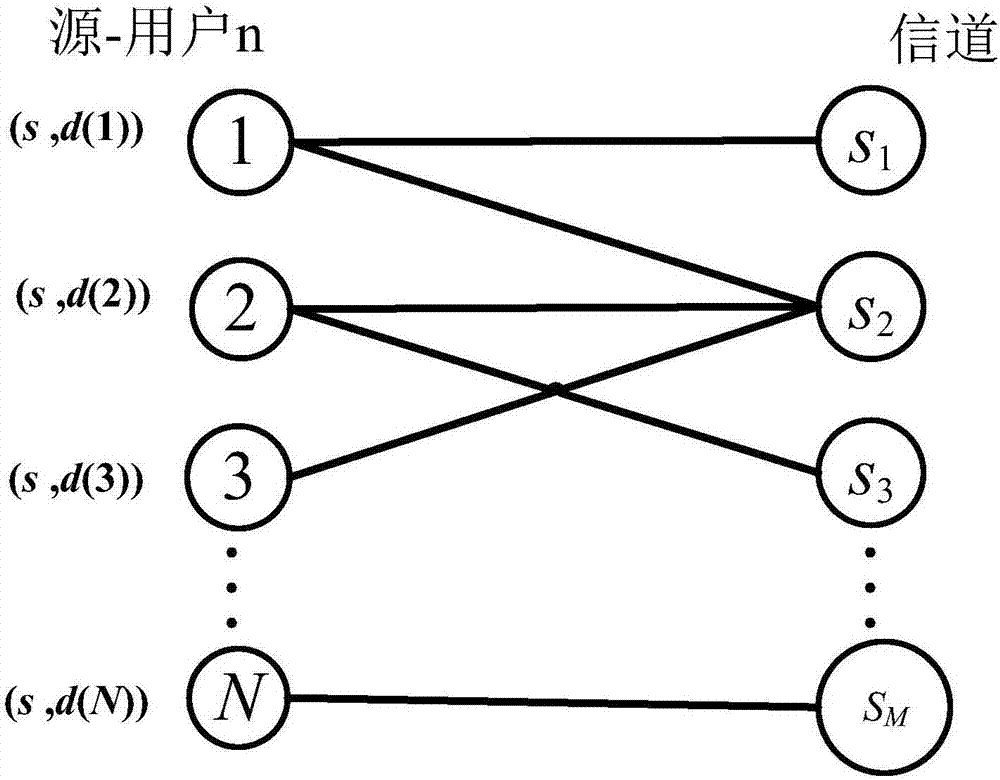
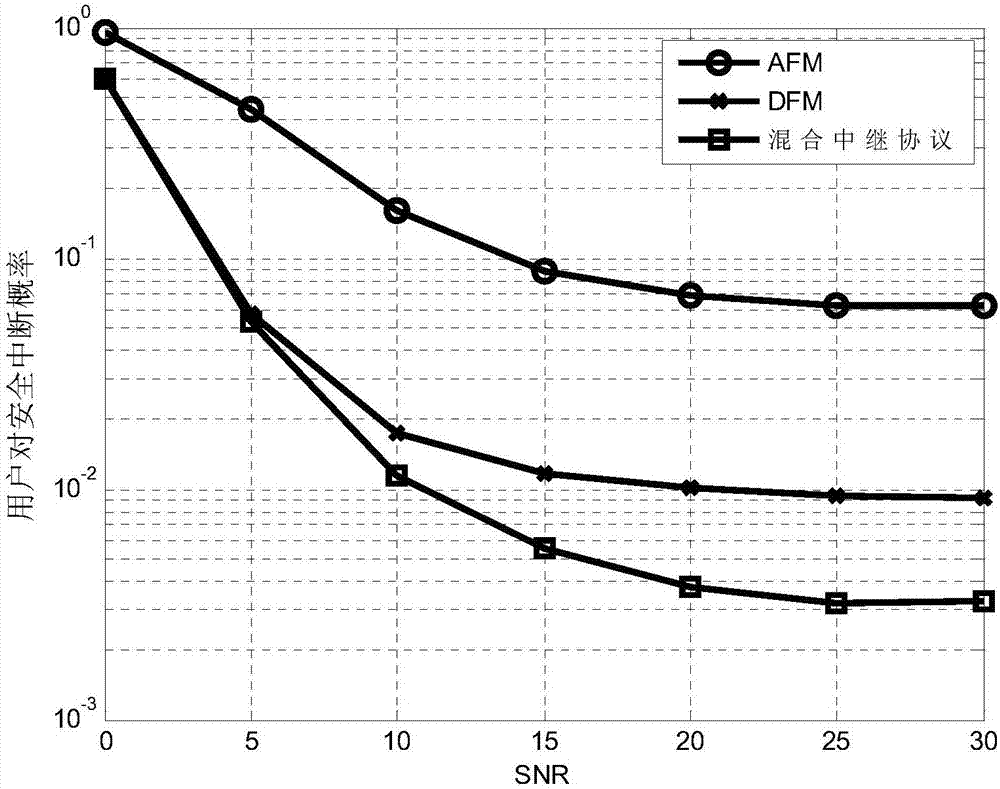
[0041] The present invention considers an eavesdropping channel model of a multi-user relay OFDM network, the relay OFDM system has M mutually independent subcarriers, each subcarrier only bears the data of one authorized user, and the system can provide services for N users (N ≤M), assuming that there is an eavesdropper trying to eavesdrop on the information of N users in the system, assuming that the relay node adopts the hybrid relay protocol, when the relay node is relatively close to the source node, the node pair can choose the way of decoding and forwarding (Decode-and-Forward, DF); if the relay node is relatively close to the destination node, the node pair can choose the Amplify-and-Forward (AF) transmission mode.
[0042] All data transmission in the network is carried out in a time-slotted manner, and each time slot is divided into two sub-slots. The relay ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com