Method and system for preventing configuration document from being tampered and monitoring upper computer
A configuration file and tampered technology, which is applied in the direction of program control design, program control device, computer security device, etc., can solve the problems of unfavorable protection of important files and important information, prone to failure, wasteful search for faults, etc., to achieve protection from being Effects of tampering and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
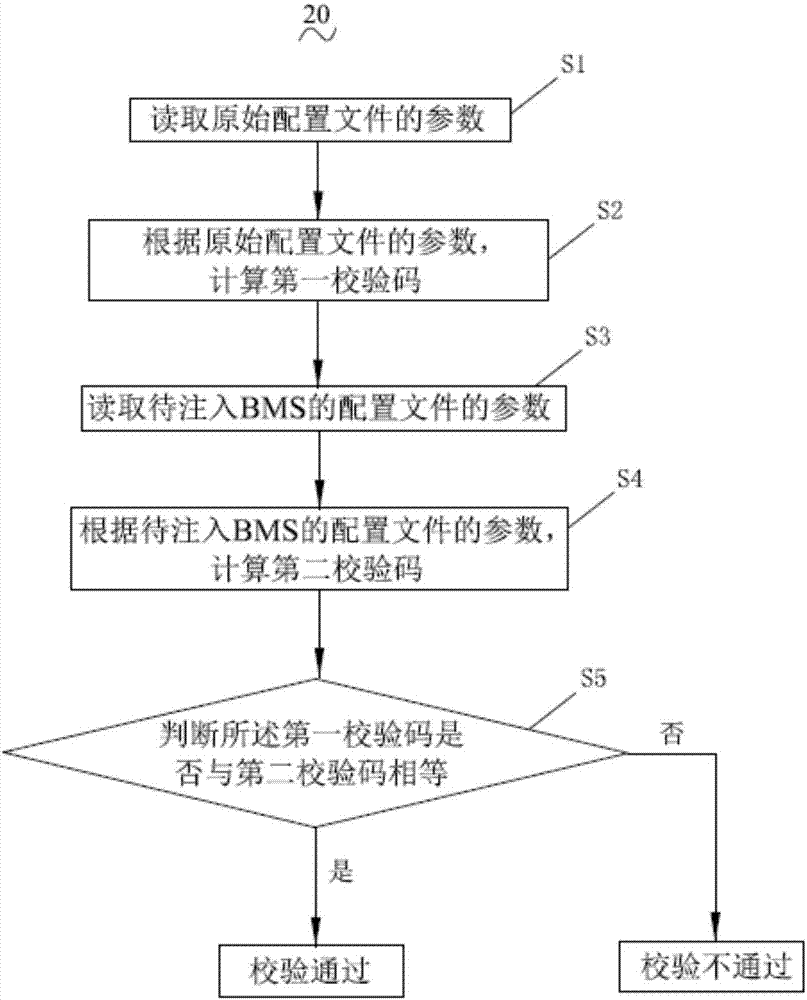
[0053] see figure 1 , figure 1 It is a flowchart of a method 20 for preventing configuration files from being tampered with according to the first embodiment of the present invention, including:
[0054] S1, read the parameters of the original configuration file;
[0055] S2. Calculate the first check code according to the parameters of the original configuration file;
[0056] S3, reading the parameters of the configuration file to be injected into the BMS;
[0057] S4. Calculate a second check code according to the parameters of the configuration file to be injected into the BMS;
[0058] S5, judging whether the first check code is equal to the second check code, if they are equal, the check is passed; otherwise, the check is not passed.
[0059] specifically,
[0060]In the step S5, it is judged whether the first check code is equal to the second check code, and if they are equal, after the check is passed, the method further includes: injecting the configuration file ...
Embodiment 2
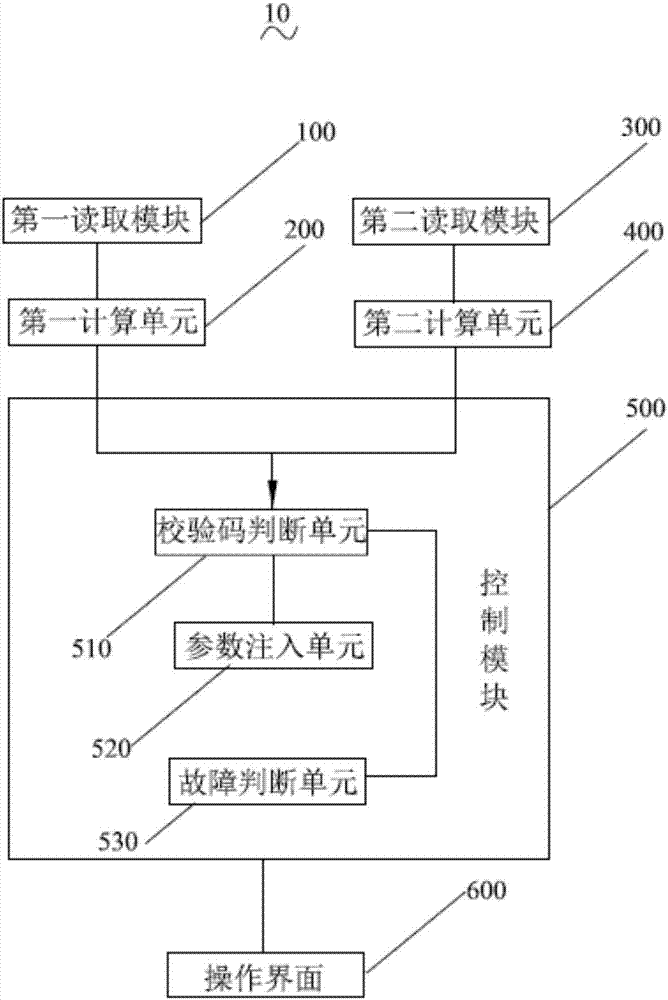
[0064] see figure 2 , figure 2 A functional block diagram of a system 10 for preventing configuration files from being tampered with provided by the second embodiment of the present invention, including:
[0065] The first reading module 100 is used to read the parameters of the original configuration file; the first calculation unit 200 is used to calculate the first check code according to the parameters of the original configuration file. The second reading module 300 is used to read the parameters of the configuration file to be injected into the BMS; the second calculation unit 400 is used to calculate the second check code according to the parameters of the configuration file to be injected into the BMS. The first reading module 100 is connected with the first computing unit 200 . The second reading module 300 is connected with the second computing unit 400 .
[0066] The judging control module 500 is used to judge whether the first check code is equal to the second...
Embodiment 3
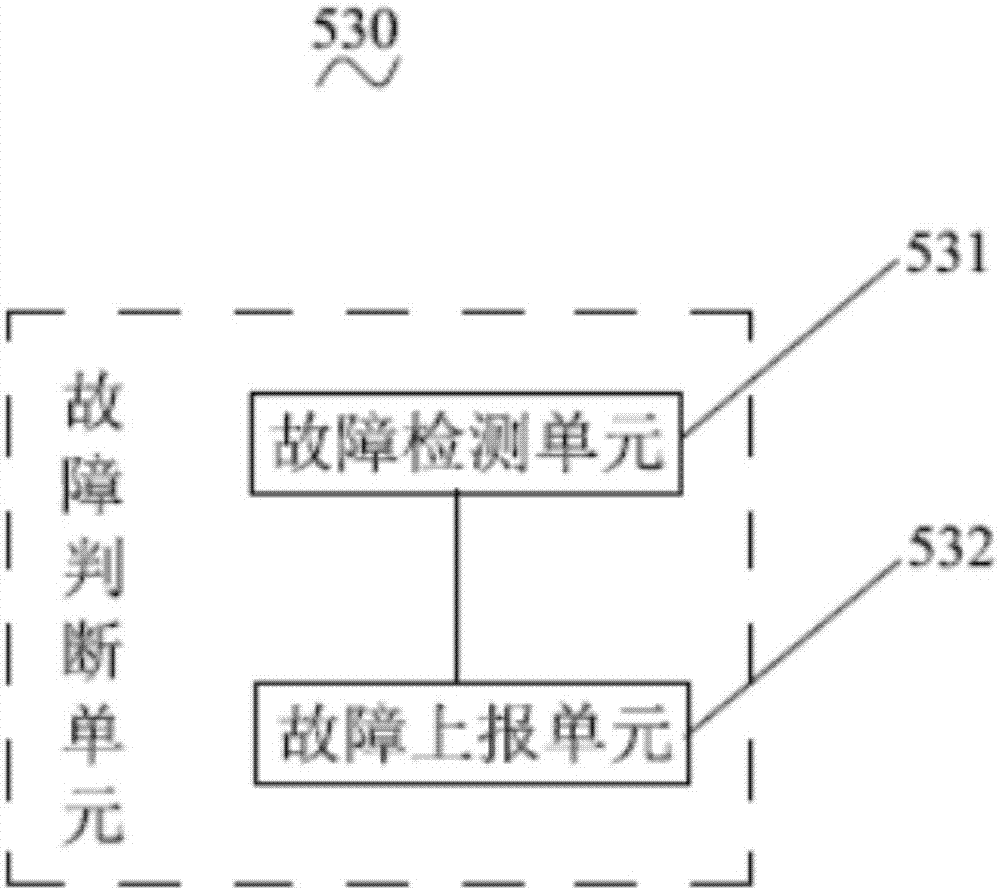
[0076] The present invention also provides a monitoring host computer, which is connected to the battery management system through a CAN line, including the system for preventing configuration files from being tampered with in the second embodiment above, and the specific structure of the system for preventing configuration files from being tampered with And the working principle is basically the same as the description of the above-mentioned embodiment 2. For details, please refer to the above-mentioned embodiment 2, which will not be repeated here.
[0077] In this embodiment, the configuration file is prevented from being tampered with. If the verification in the host computer fails, the configuration file cannot be injected into the BMS, thereby improving the security of system information and protecting the normal operation of the device.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com