Data secure transmission system and method for firmware upgrade
A firmware upgrade and transmission system technology, applied in the direction of digital transmission system, transmission system, data exchange network, etc., can solve the problem of unsafe firmware upgrade
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
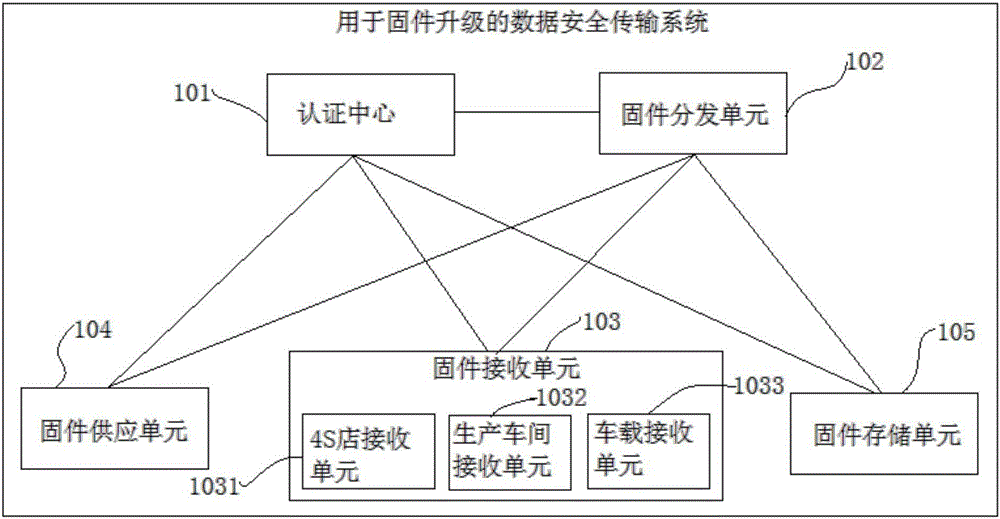
[0115] see figure 1 , figure 1 A schematic structural diagram of a data security transmission system for firmware upgrades in the first embodiment of the present invention is shown, and the specific structure includes:
[0116] The authentication center 101 is configured to generate public key authentication information of the corresponding unit based on the identification code and public key of each unit, and send it to the corresponding unit after being encrypted by the public key of the corresponding unit. After being authenticated by the authentication center 101 , secure data transmission can be performed between units based on public key authentication information. Specifically, in this embodiment, each unit encrypts its own identification code and public key with the public key of the authentication center 101 and sends them to the authentication center 101, and the authentication center 101 generates the following public key authentication information:
[0117] E[PR ...
no. 2 example
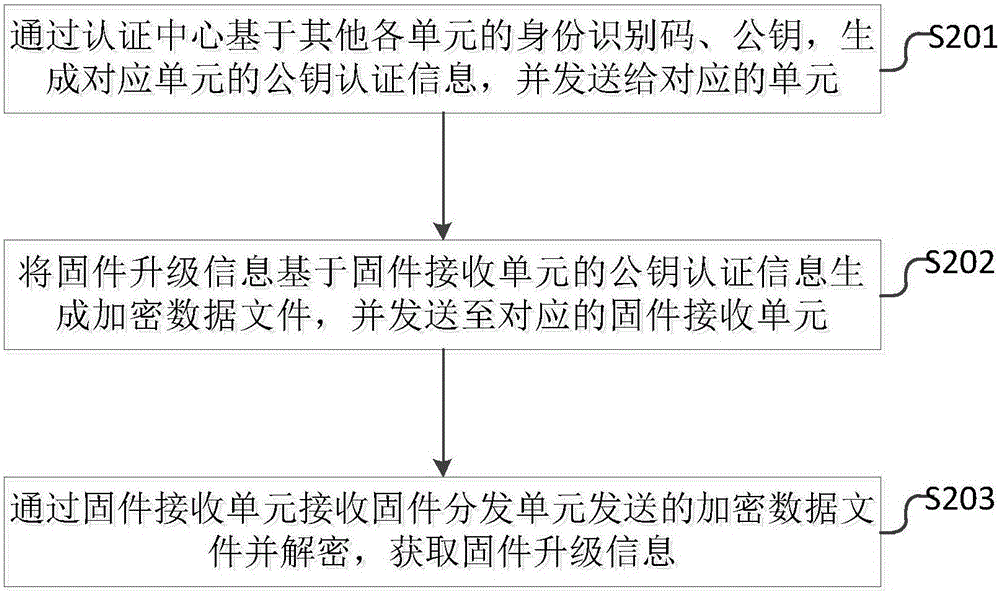
[0126] see figure 2 , figure 2 It shows a schematic flow diagram of the data security transmission system for firmware upgrade in the second embodiment of the present invention, and the specific steps are as follows:
[0127] S201. Generate public key authentication information of the corresponding unit based on the identification codes and public keys of other units through the certification center, and send it to the corresponding unit.
[0128] Specifically, in this embodiment, the process for the authentication center to generate public key authentication information for each unit is as follows:
[0129] The certification center sends its own public key PU CA Sent to each unit, each unit receives the PU CA After the own public key PU X and ID X by PU CA After encryption, it is sent to the certification center, and the certification center passes its own private key PR CA Obtain PU after decrypting the information X and ID X Then generate the following public key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com