A key revocation method for key management tree in cloud database
A key management and database technology, applied to key distribution, can solve the problems of increased storage overhead and management difficulty, large computing overhead, etc., and achieve the effect of saving storage overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0026] The present invention comprises the following steps:
[0027] 1. Key revocation state management tree establishment process:
[0028] 11) First select a root key K with a length of 256 bits r , set it as the root key K of the Hash tree with key r , and keep it secret;
[0029] 12) Define the number of branches and the depth of the tree according to the needs of the user, and establish a hash tree with a key;
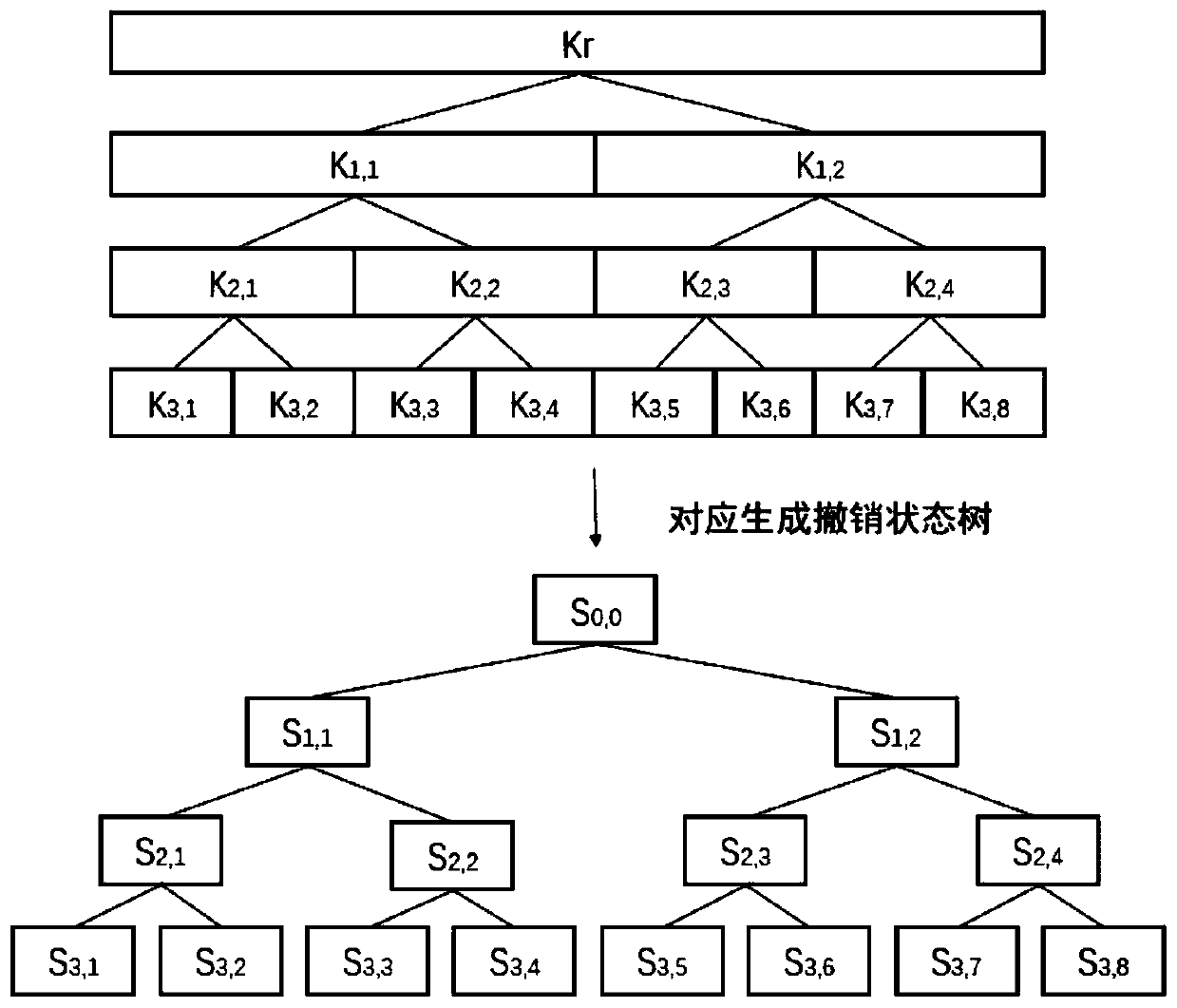
[0030] 13) If figure 1 As shown, when the key management tree structure of the cloud database is established, the key revocation state management tree is correspondingly established to establish a state management tree corresponding to the structure; This kind of key management tree structure is universal, here is just one example;
[0031] 14) Revocation state value S of each node in the key revocation management tree x,y...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com