Method for realizing application program safety certification based on CPU space-time isolating mechanism
An application and security authentication technology, applied in computer security devices, program/content distribution protection, instruments, etc., can solve problems such as poor timeliness, tampering, etc., to ensure validity, high isolation, and reduce key leakage problems. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
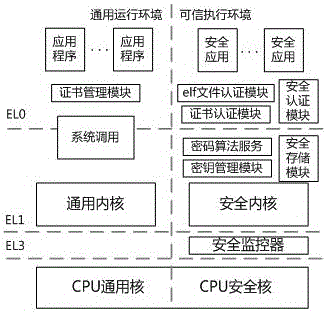
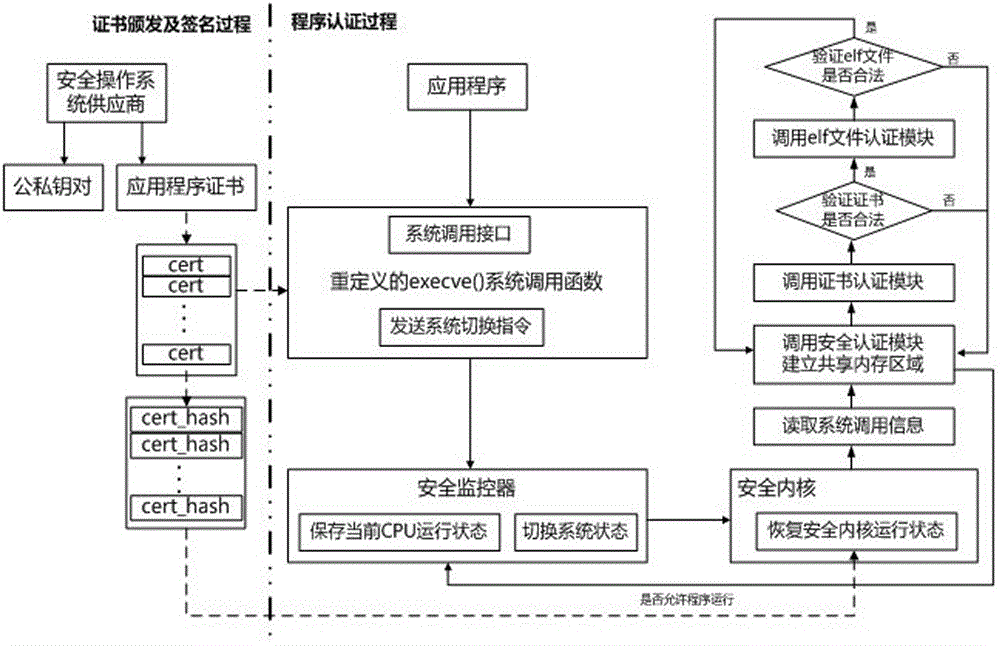
[0034] Such as Figure 1-2 As shown, a method for implementing application security authentication based on the CPU space-time isolation mechanism, including a signature process and an authentication process;
[0035] Among them, the signature process: each application of the secure operating system provider issues a set of public-private key pairs and X.509 certificates (called application certificates), and embeds the certificate number into the elf file header; The private key signs the elf binary file, and embeds the signature value into the extensible area of the application certificate; in addition, the supplier uses its own private key to sign the application certificate and stores the signature value in the "issuer unique identifier" of the certificate Area, and store the hash value of the certificate to the secure operating system; the signing process generates two sets of important data - the application certificate and the certificate hash value, which provide sup...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com