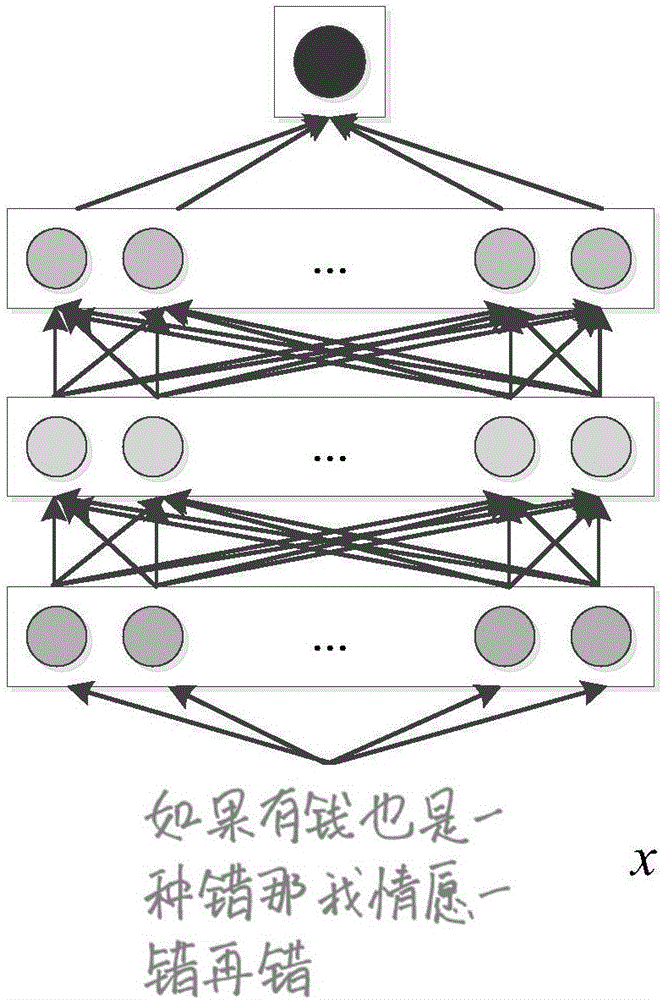
Conditional generative adversarial network-based online handwriting identification method
A recognition method and conditional technology, applied in character and pattern recognition, computer components, instruments, etc., can solve the problems of model freedom and uncontrollability, difficulty in training, etc., achieve a good balance between false acceptance rate and false rejection rate, and easy collection , the effect of improving the recognition efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039]The online handwriting recognition method provided in this embodiment is mainly to provide convenient and personalized door opening, and at the same time, it can avoid emergencies such as forgetting to bring the key, losing the key, and forgetting the access control password. Suppose there is a house with three bedrooms and one living room, and the roles include: parents and children. Usually, the child's bedroom and the parents' bedroom are private spaces, and the child does not want the parents to enter their room. For the living room, toilet and kitchen belong to the public area of the family. Therefore, we need to set different permission levels. By entering different people's handwriting signatures for different doors, that is, entering different characters, we can identify whose handwriting is and whether it is forged signatures for others. That is to say, the signature recognition does not recognize a specific character, but relies on a certain person's writing...
Embodiment 2
[0046] The online handwriting recognition method provided in this embodiment is mainly to solve the problem that the same document needs to be signed by different users in different places, and often encounters the thorny problem that users cannot be present due to delay.
[0047] 201: a user registration module, recording the identity confirmation of the user.
[0048] 202: The receiving module accepts an arbitrary text input by the user in advance, and puts them into the confrontation network as training samples.
[0049] The method includes a) accepting a request from multiple contract users to sign a document; b) receiving the sign and number of contract users; c) generating an identifier associated with the signed document; d) sending an invitation to sign the document together with the document identifier For each contract user; e) provide each user with a signature entry; f) receive each user's signature identification, signature time stamp and face image time stamp; g)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com