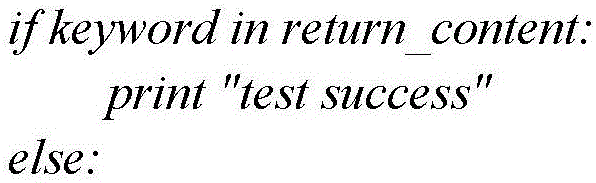Filling type remote bug PoC (proof of concept) writing method and bug detection method
A filling and loophole technology, applied in the network field, can solve the problem of not necessarily mastering programming ability, and achieve the effect of convenient batch vulnerability detection, convenient calling, and simplifying the writing process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The preferred embodiments will be described in detail below in conjunction with the accompanying drawings. It should be emphasized that the following description is only exemplary and not intended to limit the scope of the invention and its application.
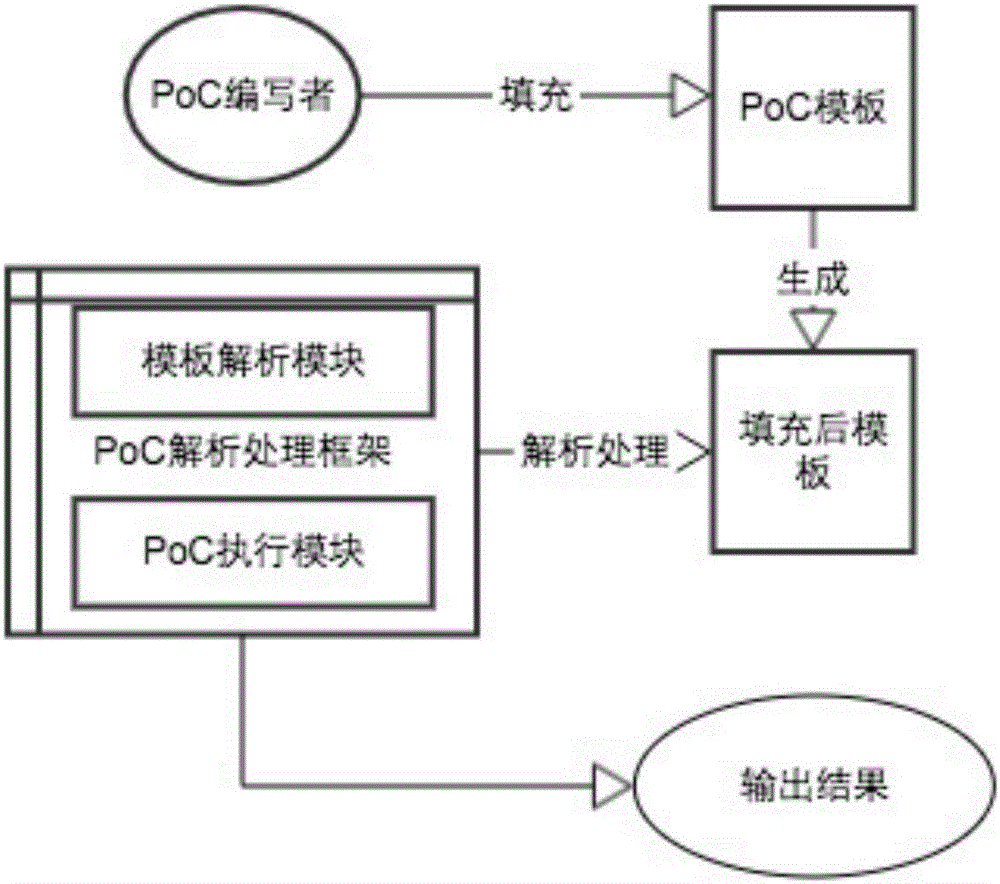
[0043] Process flow of the present invention is:
[0044] 1) The framework provides a standard remote PoC writing template
[0045] 2) On the premise that the vulnerability analysis and testing have been completed, the PoC writer then extracts the content corresponding to the items that need to be filled in the template from the vulnerability analysis results according to the filling items of the template, and fills in the requested parameters, addresses, and methods And the result judgment condition (the template on the right of this step is already standard and fixed, and can be filled in through the online page, without sticking to JSON or XML format).
[0046] 3) Output the filled PoC writing template to the PoC ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com