Auditing method for screening round entry events
An event and abnormal event technology, applied in computing, special data processing applications, instruments, etc., can solve the problems of increasing audit labor, time cost, low audit effect, poor efficiency, etc., to reduce misjudgment of audit results, improve Audit efficiency, reduce inefficiency effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
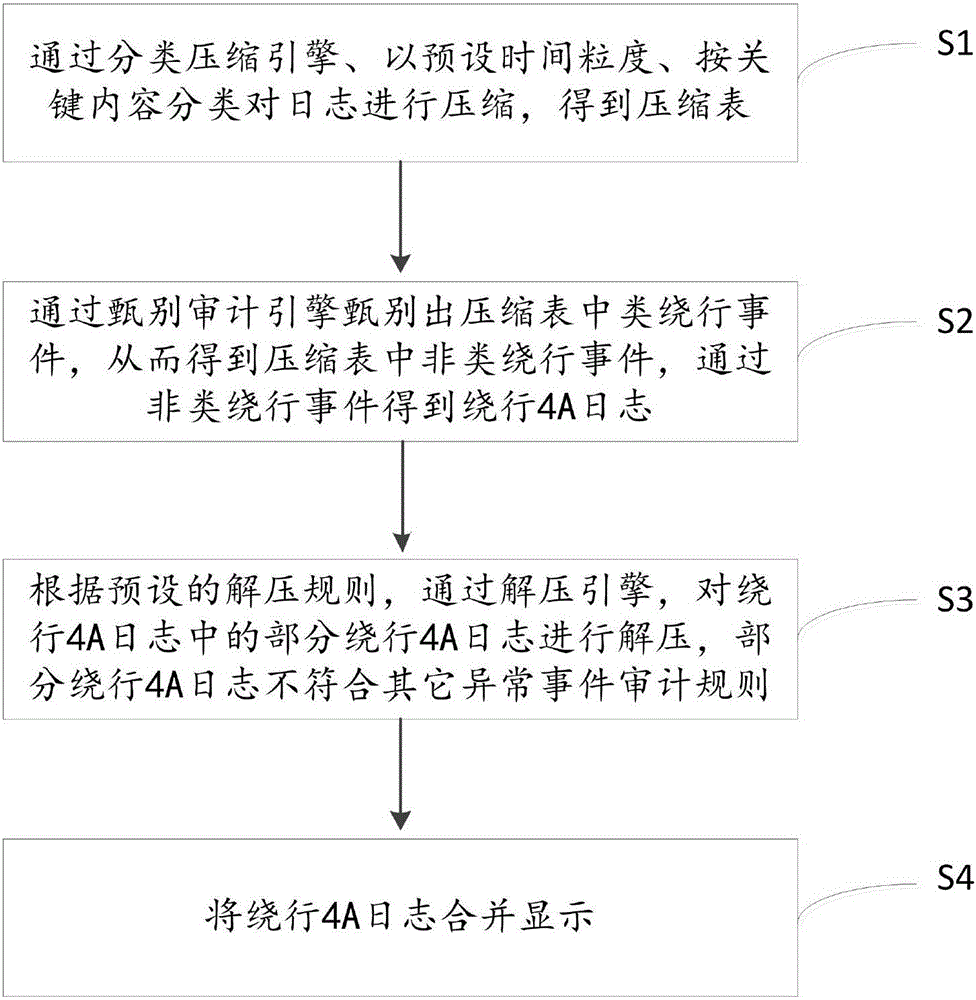
[0047] see figure 1 , is a flow chart of the audit method for screening bypass login events provided in Embodiment 1. The method comprises the steps of:
[0048] S1: Compress the logs with the preset time granularity and key content classification through the classification compression engine to obtain the compression table.
[0049] This step is used to compress large-scale logs. Specifically, the preset time granularity is set according to actual conditions, and is not specifically limited here. In this embodiment, the preset time granularity is 4 hours. The key content includes: platform, device, account, operation content, operation result, IP source, and audit exception type.
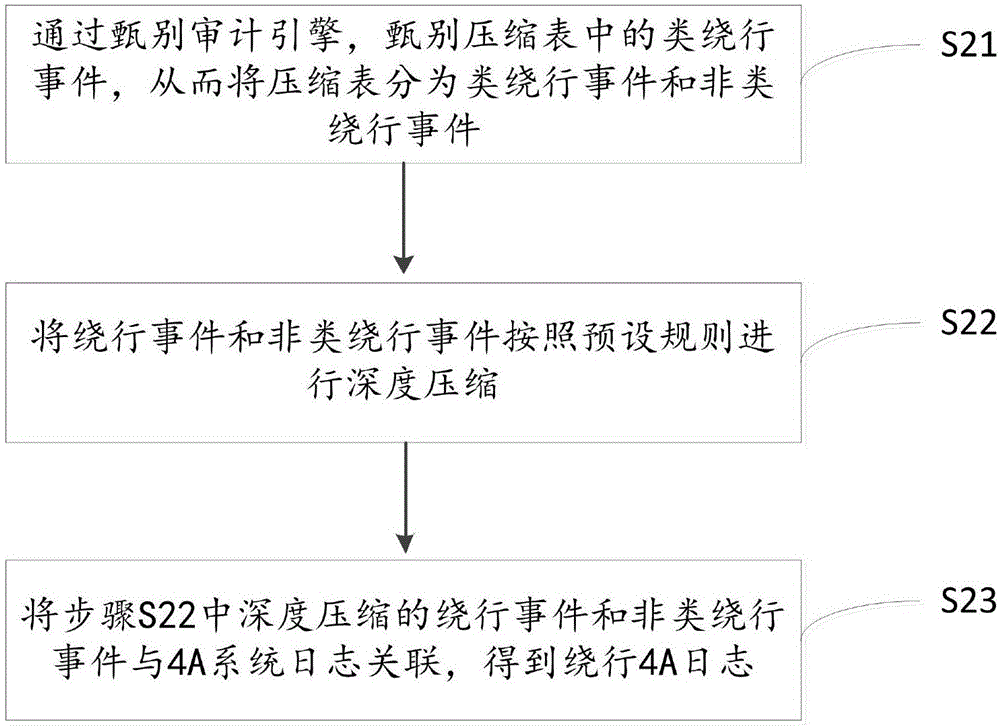
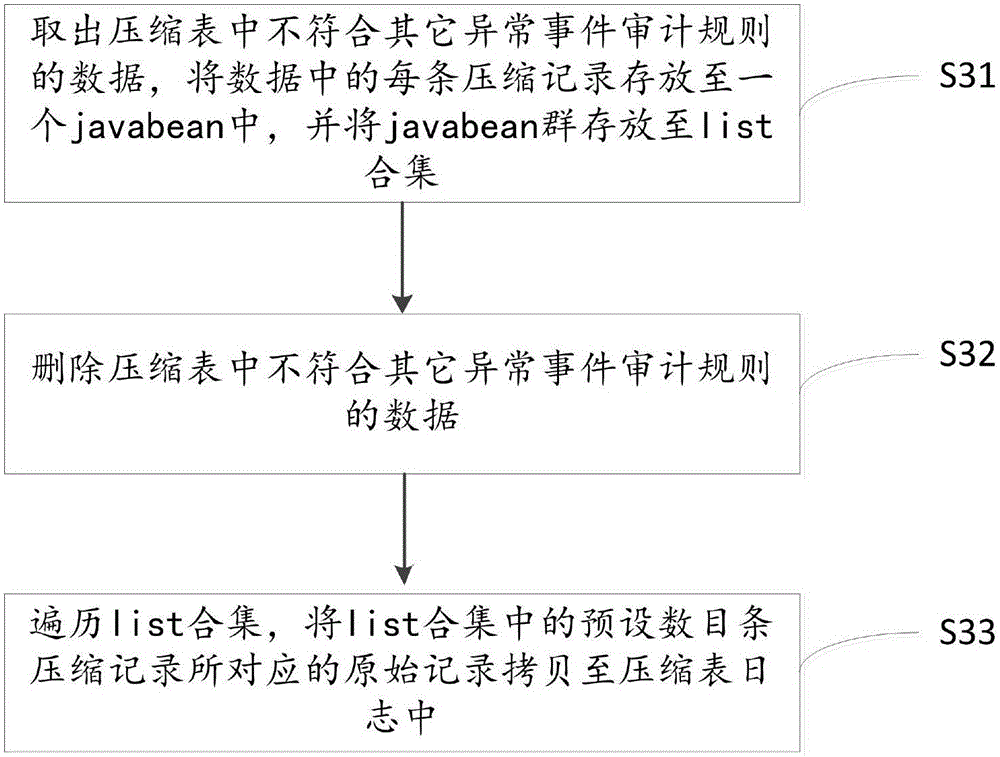
[0050] In this embodiment, during specific implementation, the large-scale log table within every four hours is divided into the same division as the key field according to the platform, device, account, operation content, operation result, IP source, and audit exception type by the classificati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com