Method for detecting unauthorized access vulnerability of power mobile application
A mobile application and unauthorized access technology, which is applied to electrical components, electrical digital data processing, instruments, etc., can solve the problem that unauthorized access cannot be found
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0043] (1) Determine the different user types that exist in the mobile application, ensure the comprehensiveness of the user types, and obtain the number of users corresponding to each user type;
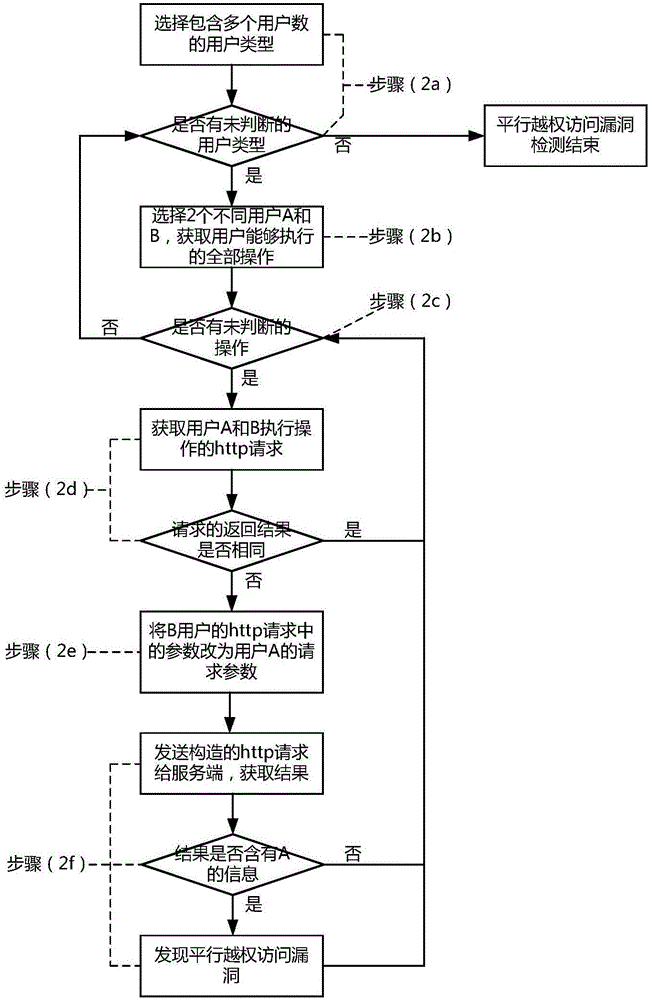
[0044] (2) Construct http requests of different users belonging to the same user type for the same operation, modify the http request of one of the users, and send the modified request to the server, and analyze the execution results to detect parallel unauthorized access vulnerabilities;
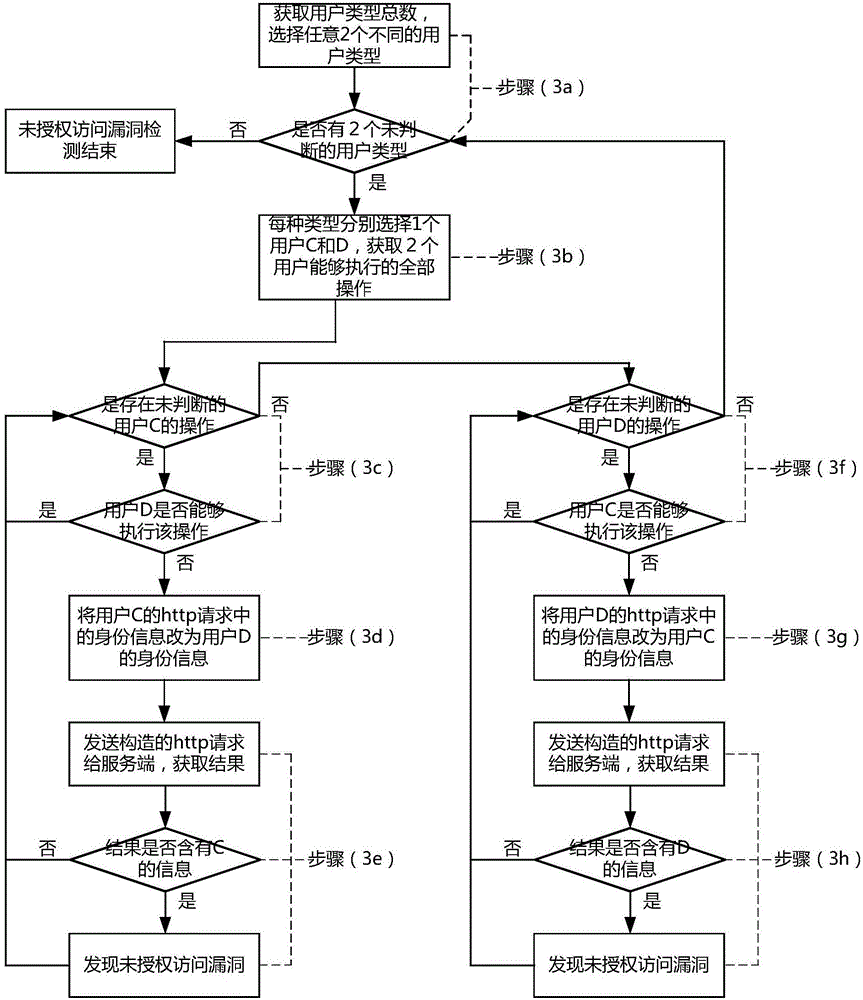
[0045] (3) Construct the http requests of different users belonging to different user types, and modify the http requests that users belonging to some user types can execute but other types of users cannot perform operations, send the modified request to the server, analyze the execution results and Detect unauthorized access vulnerabilities;
[0046] (4) Integrating the vulnerabilities detected in step (2) and step (3), complete the detection of unauthorized access vulnerabilities in power mobil...
Embodiment 2
[0068] The present invention will be further described below in conjunction with the accompanying drawings and the specific mobile application of "handheld vehicle management (abbreviation: handheld vehicle management)". The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
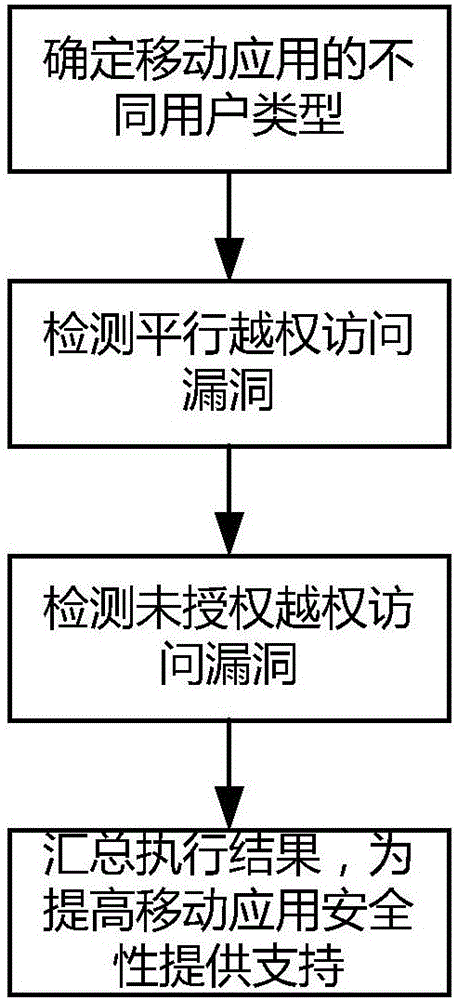
[0069] refer to figure 1 As shown, a method for detecting unauthorized access vulnerabilities of power mobile applications in the present invention includes four steps of determining the user type of the mobile application, parallel unauthorized access vulnerability detection, unauthorized access vulnerability detection, and summarizing test results.
[0070] Determining the different types of users that exist in a mobile application includes the following steps:
[0071] (1a) According to the actual business of the mobile application, determine the user type that exists in the mobil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com