Method and device for verifying identifying code
A verification method and verification code technology, applied in electrical components, transmission systems, etc., can solve problems such as reducing server performance and increasing database operation frequency, and achieve the effect of reducing operation frequency and improving performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
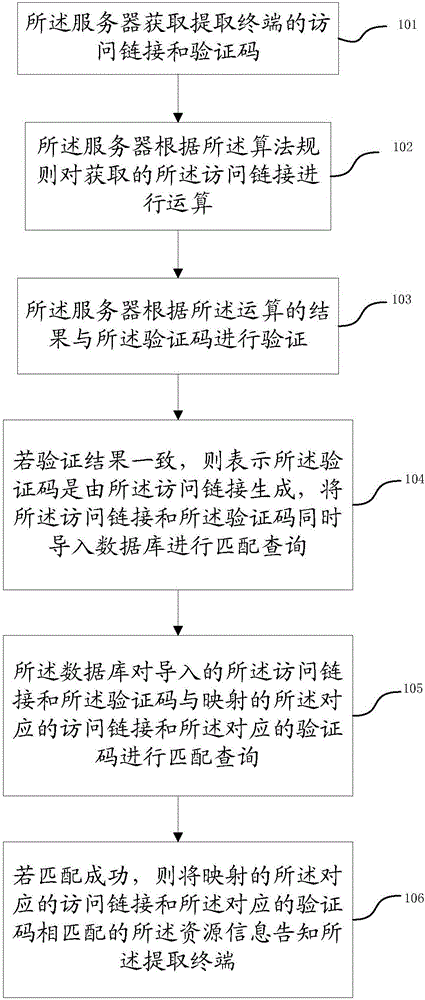
[0044] As stated in the background art of the present invention, in the prior art, when the server receives each verification code, it needs to query the database, which increases the operating frequency of the database, thereby reducing the performance of the server.
[0045] In view of the above technical problems, the present invention proposes to preset algorithm rules in the server. When there are a large number of verification codes accessing the server, the server first performs algorithm preprocessing on them, filters out illegal verification codes, and sends the filtered verification codes Performing operations on the database reduces the frequency of database operations, thereby improving server performance.
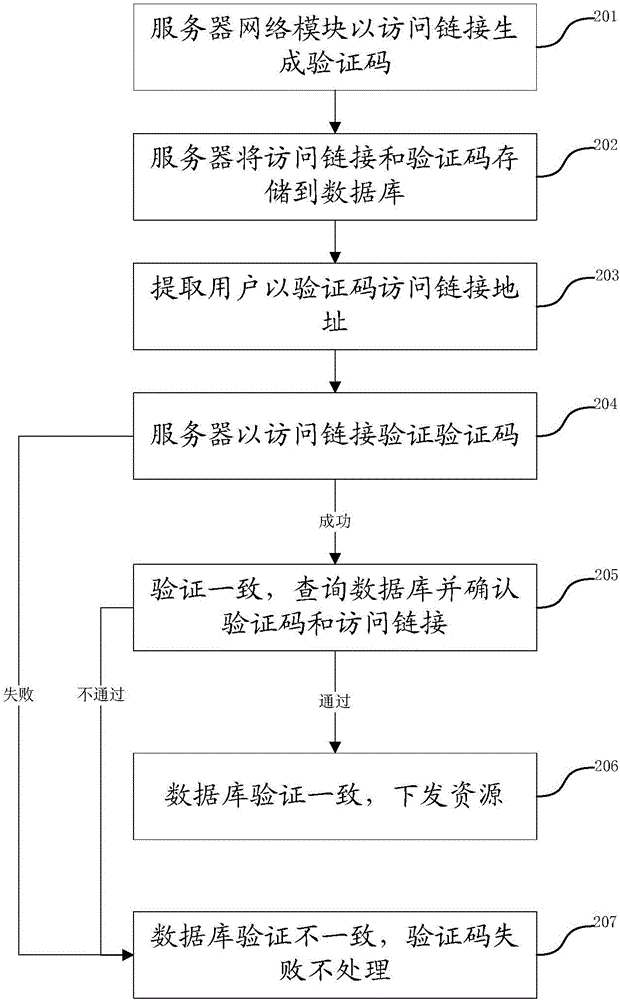
[0046] Such as figure 1 As shown, the flow diagram of a verification code verification method provided by an embodiment of the present invention, it should be noted that before performing the following steps, it is necessary to preset the access link and verification...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com