Secure software downloading and starting method
A software download and security technology, applied in the direction of program loading/starting, computer security devices, electrical components, etc., can solve the problem of destroying equipment security and achieve the effect of equipment security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
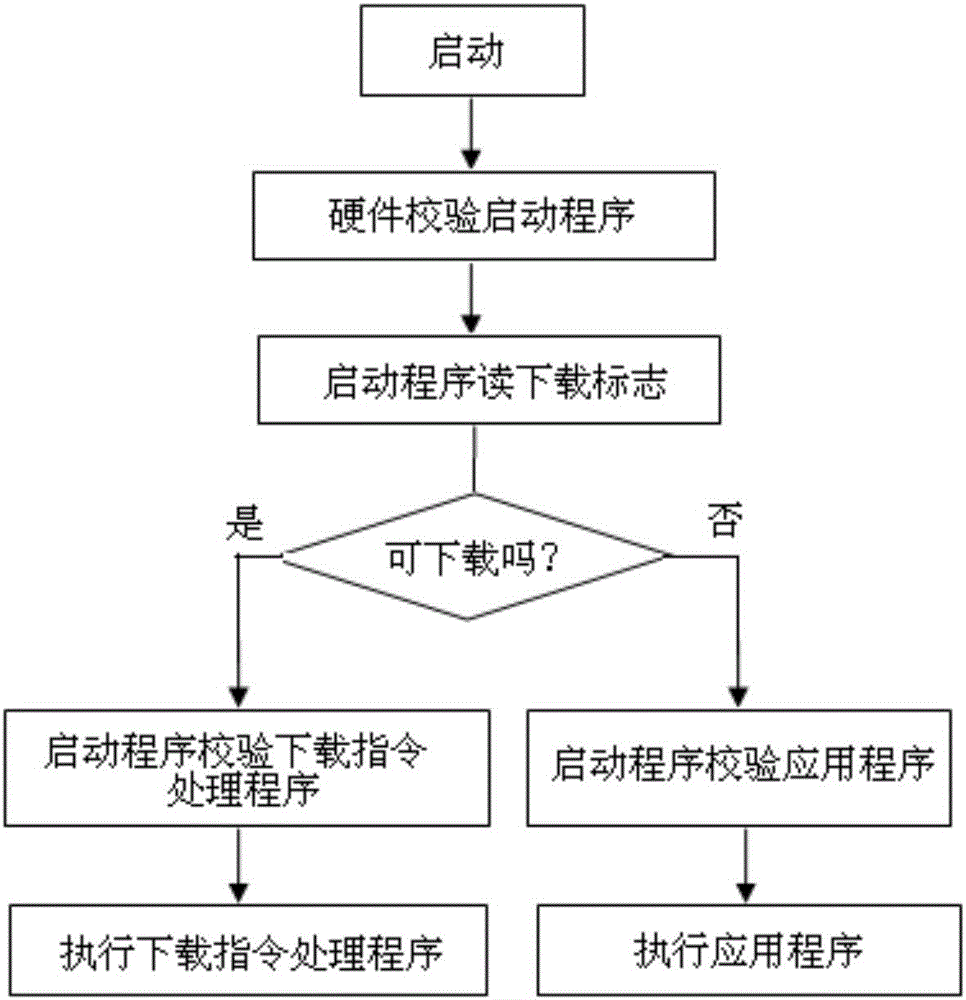
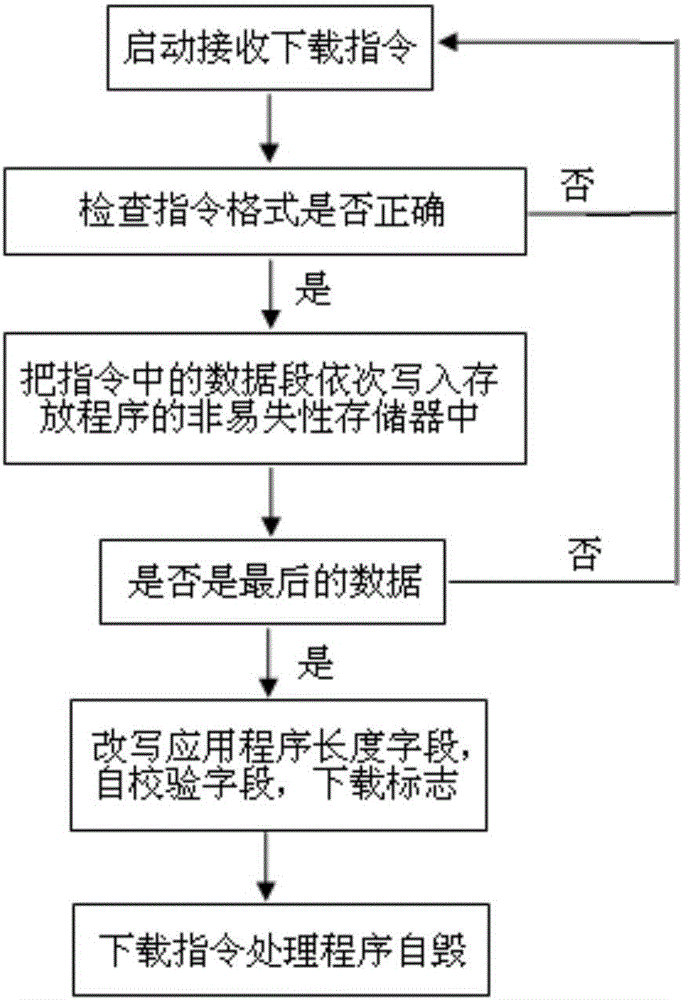
[0022] The safe software downloading and starting method includes a hardware verification program, a software starting program, and a download instruction processing program. The method can realize safe software downloading and self-starting. The device using this method stores the download flag field in the non-volatile memory; also stores the respective length fields and self-checking fields of the startup program, the download program and the application program.
[0023] see figure 1 After the device using the safe software download and startup method is started, the hardware logic circuit first checks the startup program implemented by the software. This is because the hardware logic circuit is not easily attacked by an attacker compared with the software program, so the hardware logic circuit first checks the startup program implemented by the software to ensure that the startup program has not been tampered with by the attacker. Then start the program or hardware logi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com