A two-stage hash chain storage method for data or files
A two-stage, chain-based certificate storage technology, which is applied to the field of two-stage hash chain storage of data or files, which can solve the problems of no data errors, and the inability to prevent files from being tampered with.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
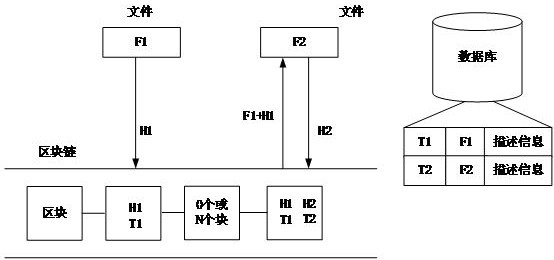
[0072] User A uploads the credential material F1 to the blockchain client C through the mobile APP client, and the blockchain client C calculates the hash value of the credential material F1 through the hash algorithm, that is, H1= HashF1, the hash algorithm can be It is an algorithm such as SHA-512 and SHA-384. The blockchain client C puts the file F1, the hash value H1 calculated by the file F1, and the current timestamp T1 into the block in the form of a transaction, and broadcasts the constructed block to each consensus of the blockchain B node.
[0073] After receiving the block, each consensus node of blockchain B verifies the transaction file F1, file F1 hash value and timestamp in the block. The verification includes signature verification and file hash verification, and sends the verification result to Each blockchain consensus node. Each blockchain consensus node votes after receiving the verification results. For transactions that pass the vote, the blockchain gen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com