Security processing method, device, processing chip and network equipment
The technology of a processing method and a processing device, which is applied in the field of communication, can solve problems such as low processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
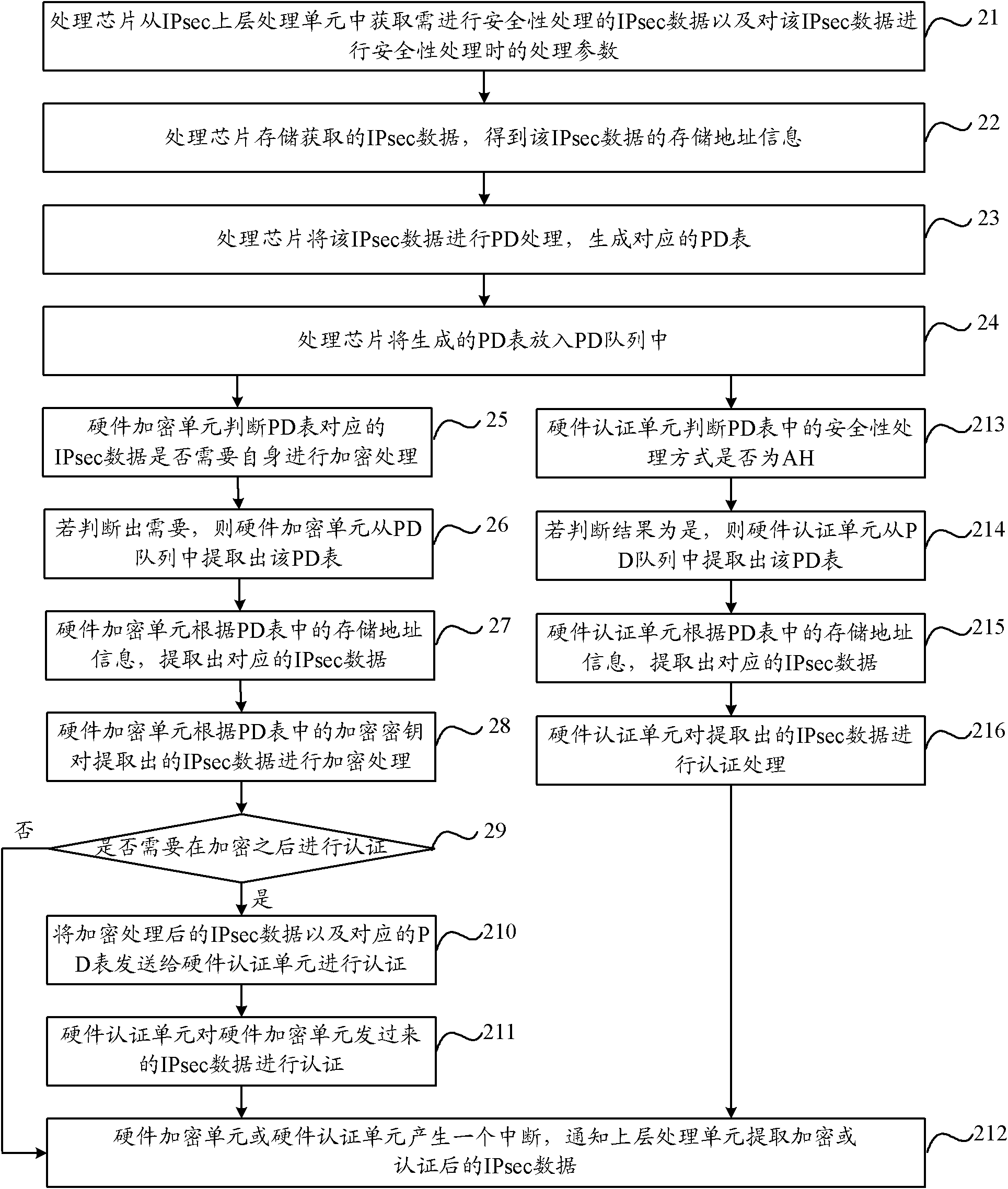
[0039] Such as Figure 4 As shown, it is a schematic flow diagram of the security processing method proposed in Embodiment 1 of the present invention, and its specific processing flow is as follows:
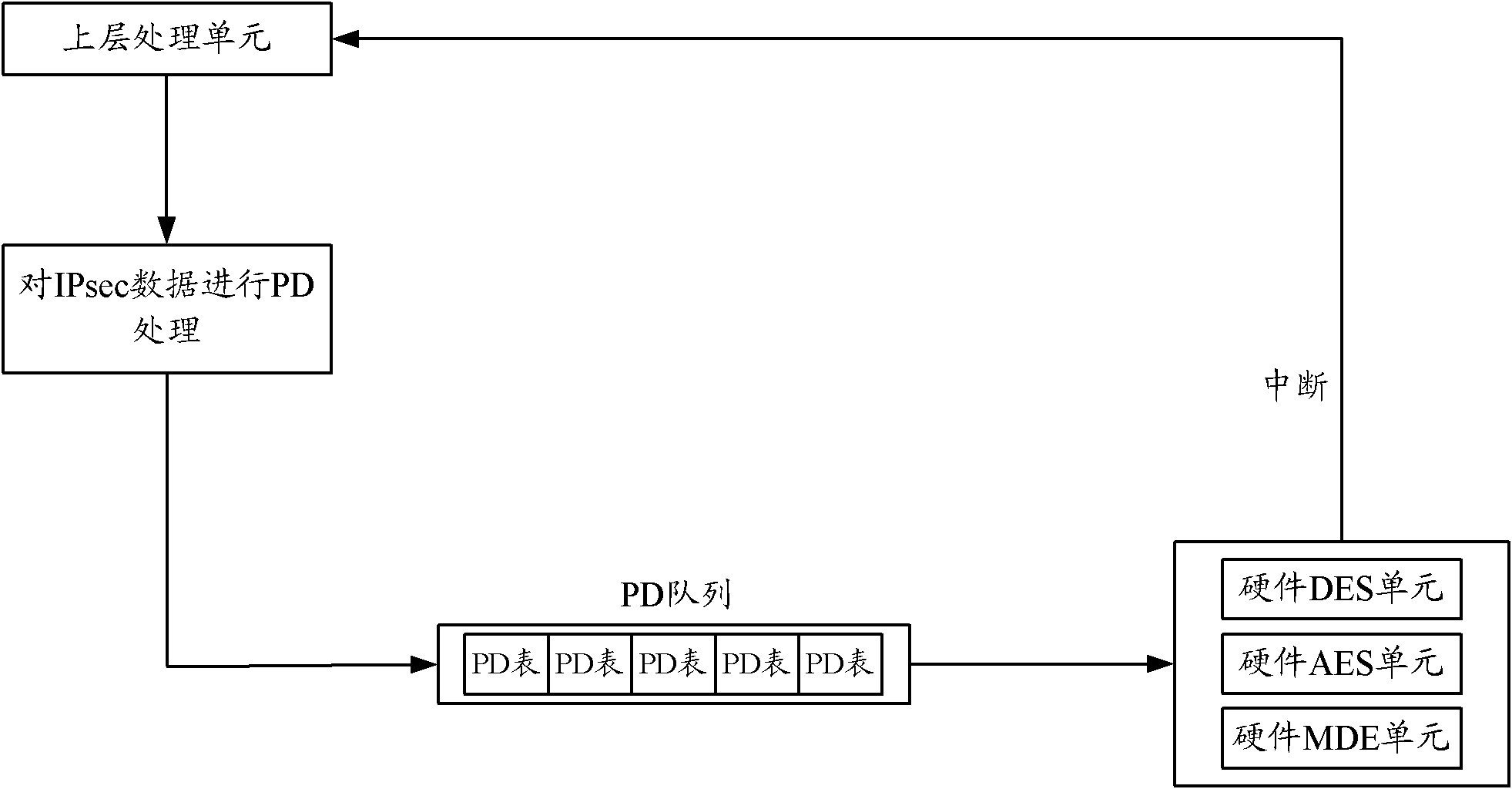
[0040] Step 41, obtaining the security processing method of the IPsec data that needs security processing;
[0041] The processing chip obtains from the IPsec upper layer processing unit the IPsec data that requires security processing and the processing parameters when performing security processing on the IPsec data. The above processing parameters include the security processing method and the security processing key. If encryption is required processing, the security processing key contains the encryption key; if authentication processing is required, the security processing key contains the authentication key; if encryption processing is required first, and then authentication processing is performed, the security processing key The key contains both the encryption key and ...
Embodiment 2
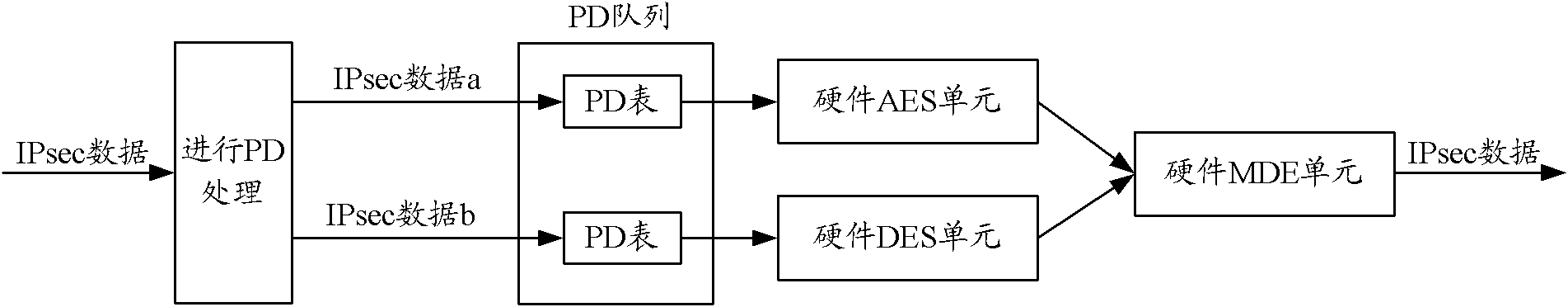
[0073] Such as Figure 6 As shown, the security processing method of IPsec data a is AES+AH, and the security processing method of IPsec data b is DES+AH, wherein, the authentication processing method corresponding to the AES algorithm is the software authentication processing method, and the authentication processing method corresponding to the DES algorithm is The method is the hardware authentication processing method. After the processing chip performs PD processing on the IPsec data a, the corresponding PD table is obtained, and then the PD table of the IPsec data a is put into the hardware encryption processing queue corresponding to the hardware AES unit, and the hardware AES unit is placed in the hardware encryption processing queue according to the The time points are sequentially extracted from the hardware encryption processing queue in order of first arrival, and then the hardware encryption processing is performed on the IPsec data corresponding to the extracted P...
Embodiment 3
[0075] Embodiment 3 of the present invention provides a security processing device, the structure of which is as follows Figure 7 shown, including:
[0076] A security processing mode obtaining module 71, configured to obtain the security processing mode of the IPsec data requiring security processing;
[0077] An authentication processing determination module 72, configured to determine that the IPsec data needs to be encrypted and then authenticated according to the security processing method obtained by the security processing method obtaining module 71;
[0078] An encryption algorithm obtaining module 73, configured to obtain an encryption algorithm for encrypting the IPsec data;
[0079] An authentication processing method determining module 74, configured to determine an authentication processing method for performing authentication processing on the IPsec data according to the encryption algorithm obtained by the encryption algorithm obtaining module 73, the authenti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com