ICS information safety assessment method based on analytic hierarchy method
An AHP, information security technology, applied in the ICS information security assessment based on AHP, in the field of information security assessment, it can solve the problems that the assessment method cannot be completely in accordance with the ordinary information system, lack of comparison, and direct judgment by a single method, etc. The effect of ensuring network and information security, clear thinking, and accurate assessment results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
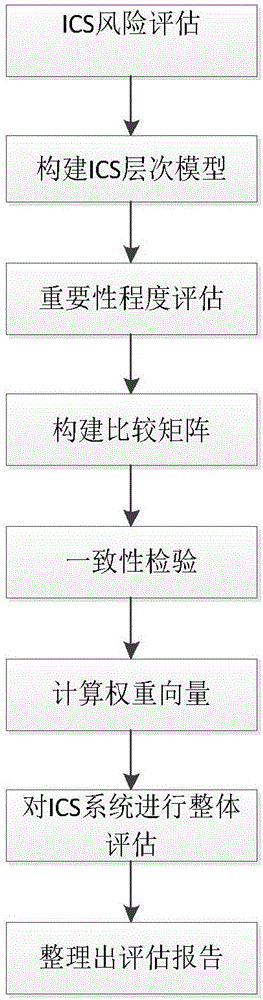
[0036] An ICS information security assessment method based on the analytic hierarchy process, the specific steps of the security assessment method are as follows:
[0037] Step A. Assess the ICS risk, and then construct the ICS hierarchical model of the industrial control system to be evaluated, and name the constructed ICS hierarchical model from top to bottom as layers A, B, C, and D;
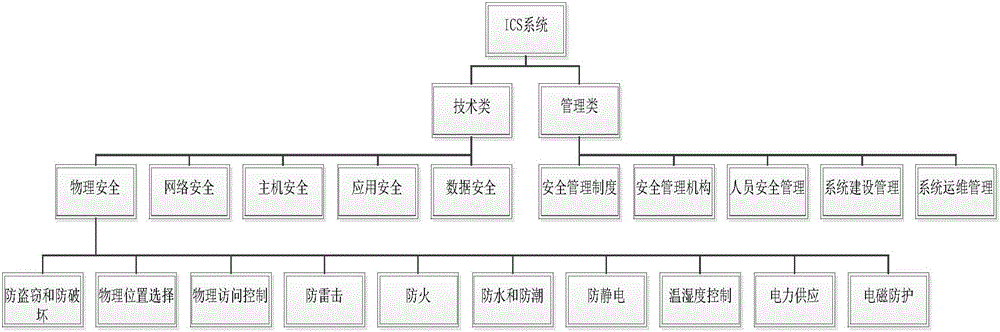
[0038] Among them, the A layer is the ICS system, and the ICS system is connected to the technical and management classes of the B layer. Safety management system, safety management organization, personnel safety management, system construction management and system operation and maintenance management; C-level physical security connection anti-theft and anti-sabotage, physical location selection, physical access control, lightning protection, fire prevention, waterproof and moisture-proof , anti-static, temperature and humidity control, power supply and electromagnetic protection;
[0039] ...
Embodiment 2
[0056] An ICS information security assessment method based on the analytic hierarchy process, the specific steps of the security assessment method are as follows:
[0057] Step A. Assess the ICS risk, and then construct the ICS hierarchical model of the industrial control system to be evaluated, and name the constructed ICS hierarchical model from top to bottom as layers A, B, C, and D;
[0058] Among them, the A layer is the ICS system, and the ICS system is connected to the technical and management classes of the B layer. Safety management system, safety management organization, personnel safety management, system construction management and system operation and maintenance management; C-level physical security connection anti-theft and anti-sabotage, physical location selection, physical access control, lightning protection, fire prevention, waterproof and moisture-proof , anti-static, temperature and humidity control, power supply and electromagnetic protection;
[0059] ...
Embodiment 3
[0076] An ICS information security assessment method based on the analytic hierarchy process, the specific steps of the security assessment method are as follows:
[0077] Step A. Assess the ICS risk, and then construct the ICS hierarchical model of the industrial control system to be evaluated, and name the constructed ICS hierarchical model from top to bottom as layers A, B, C, and D;
[0078] Among them, the A layer is the ICS system, and the ICS system is connected to the technical and management classes of the B layer. Safety management system, safety management organization, personnel safety management, system construction management and system operation and maintenance management; C-level physical security connection anti-theft and anti-sabotage, physical location selection, physical access control, lightning protection, fire prevention, waterproof and moisture-proof , anti-static, temperature and humidity control, power supply and electromagnetic protection;
[0079] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com