Program fault monitoring method and system
A program failure and monitoring system technology, applied in the computer field, can solve problems such as inability to detect program failures in a timely and accurate manner, and achieve the effect of rapid failure processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
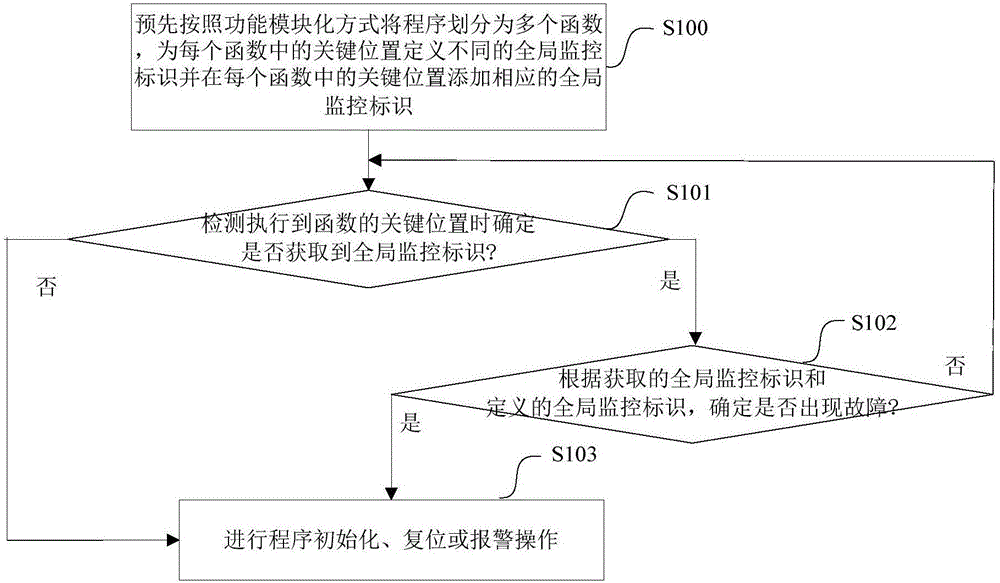
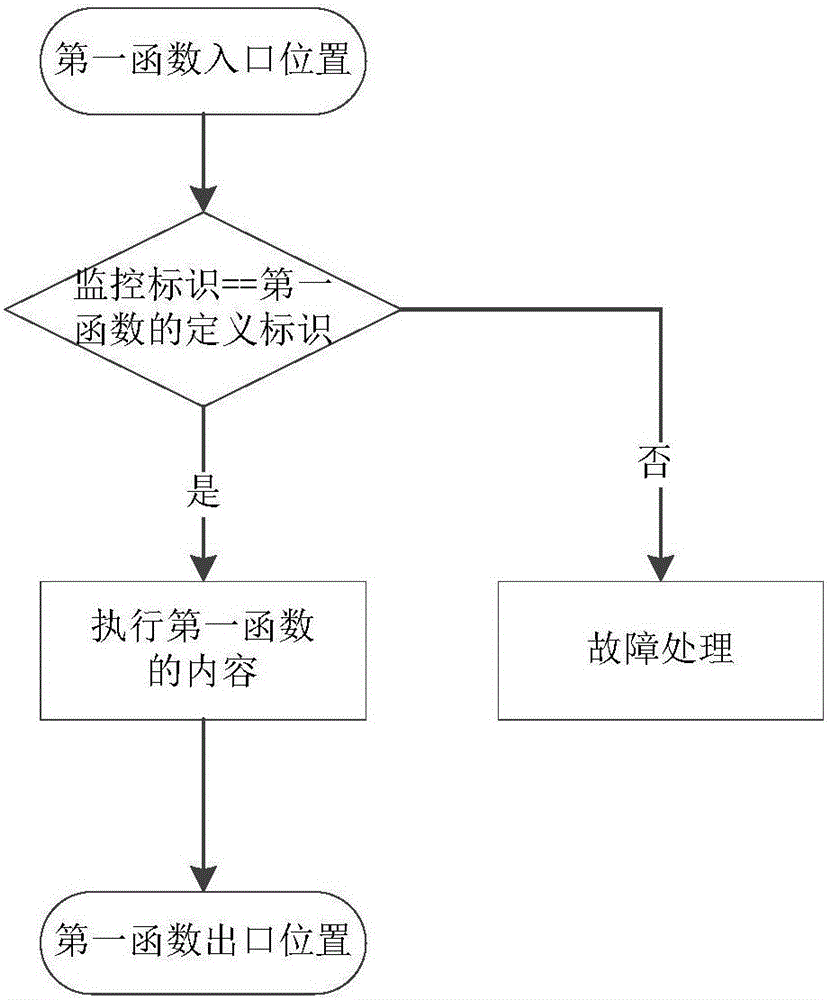
[0071] The monitoring diagram of program failure is as follows image 3 As shown, the monitoring process of program failure is as follows:
[0072] Step S1: Divide the program into three functions in advance according to the functional modularization method: the first function, the second function and the third function; predefine the global monitoring identifiers 1, 2, 3, and add the global monitoring identifier 1 to the first function Add the global monitoring identifier 2 to the entrance position of the second function, and add the global monitoring identifier 3 to the entrance position of the third function;
[0073] Step S2: In the running process of the program, when it is detected that the entry position of the first function is executed, and the program flies to the entry position of the third function at this time, the global monitoring identifier of the entry position in the third function is obtained 3 ;
[0074] Step S3: Compare the acquired global monitoring identifier ...
Embodiment 2
[0077] The monitoring diagram of program failure is as follows Figure 4 As shown, the monitoring process of program failure is as follows:
[0078] Step S1: Divide the program into three functions in advance according to the functional modularization method: the first function, the second function and the third function; predefine the global monitoring identifiers 1, 2, 3, and add the global monitoring identifier 1 to the first function Add the global monitoring identifier 2 to the entrance position of the second function, and add the global monitoring identifier 3 to the entrance position of the third function;
[0079] Step S2: In the running process of the program, when it is detected that the entry position of the second function is executed, and the program does not run away at this time, the global monitoring identifier 2 of the entry position in the second function is acquired;
[0080] Step S3: Compare the acquired global monitoring identifier 2 of the entry position in the ...
Embodiment 3
[0082] The monitoring diagram of program failure is as follows Figure 5 As shown, the monitoring process of program failure is as follows:
[0083] Step S1: Divide the program into three functions in advance according to the functional modularization method: the first function, the second function and the third function; predefine the global monitoring identifiers 1, 2, 3, and add the global monitoring identifier 1 to the first function Add the global monitoring identifier 2 to the entrance position of the second function, and add the global monitoring identifier 3 to the entrance position of the third function;
[0084] Step S2: During the running of the program, when it is detected that the entry position of the third function is executed, and the program flies to the data area at this time, the global monitoring identifier cannot be obtained, thereby determining the entry position of the third function error occured;
[0085] Step S3: Perform fault handling operations such as p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com