A biometric-based security verification method and client and server
A biometric, security verification technology, applied in secure communication devices, usage of multiple keys/algorithms, public keys for secure communication, etc. To achieve the effect of preventing replay attacks and enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
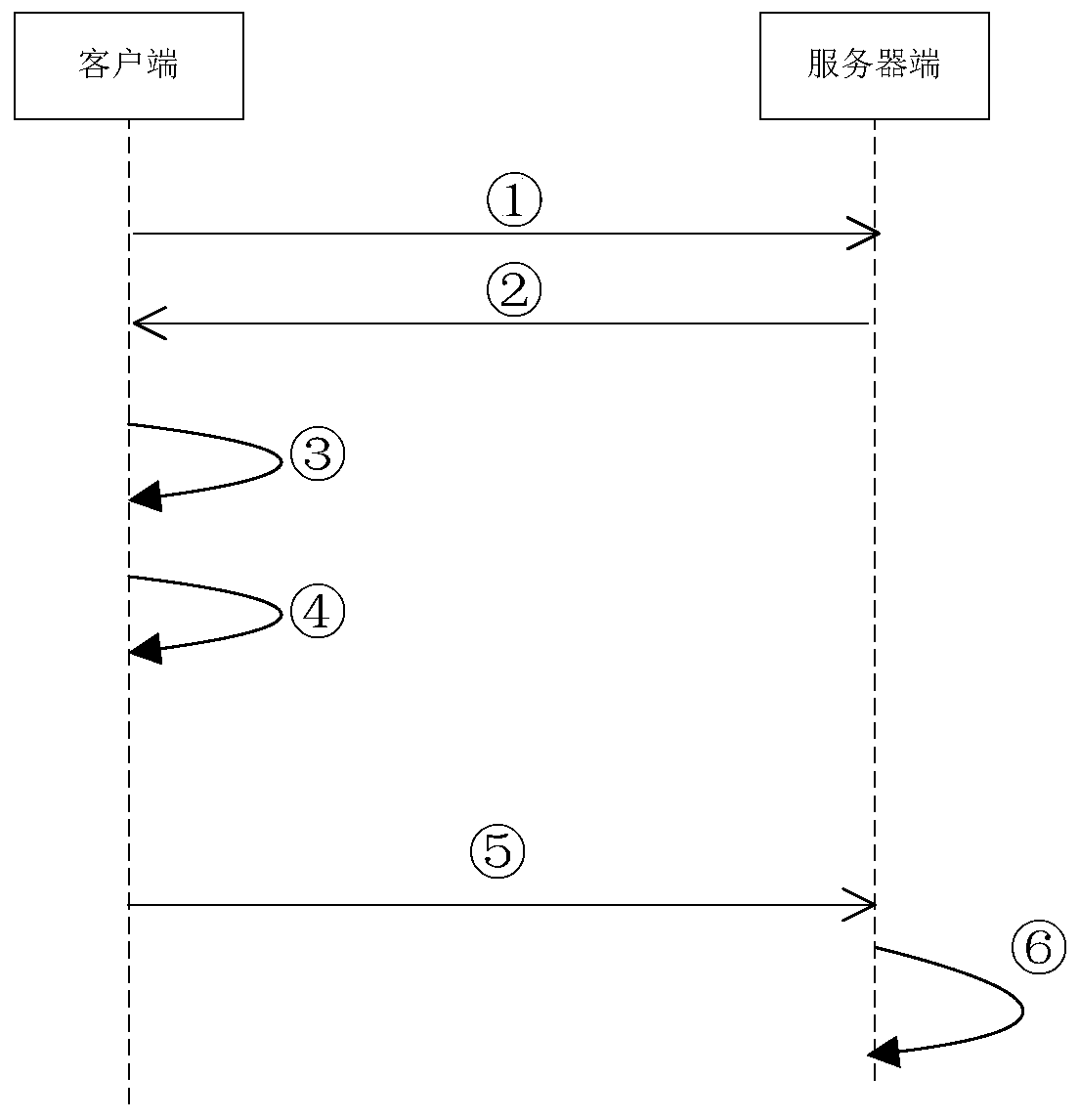
[0077] Embodiment 1. The opening process of fingerprint verification.
[0078] The fingerprint verification of Internet payment first needs to enable the fingerprint verification function, such as figure 1 shown, including the following steps:
[0079] ①. The client sends an activation request for fingerprint verification to the server.
[0080] When the user activates the fingerprint verification function, he first initiates an activation request to the server.
[0081] ②. After receiving the activation request for activation of fingerprint verification, the server sends an activation request response message to the client.
[0082] ③. After receiving the activation request response message, the client receives the fingerprint image for verification input by the user, and obtains the fingerprint template ID corresponding to the fingerprint image for verification.
[0083] Before fingerprint verification is enabled, multiple fingerprint templates entered by the user are sto...
Embodiment 2
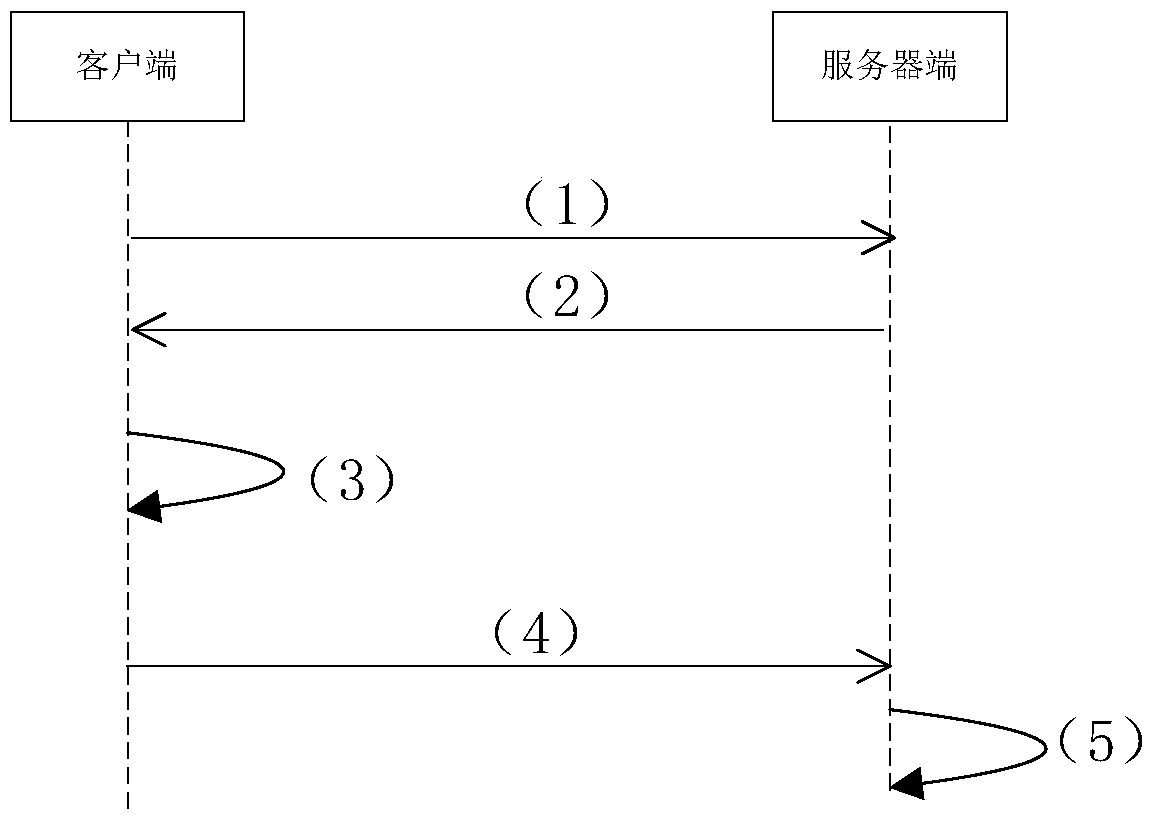
[0117] Embodiment 2, the fingerprint authentication process of the user during use.
[0118] When the user uses the Internet to pay, it is necessary to verify the user's fingerprint, such as figure 2 As shown, perform the following steps:
[0119] (1) The client sends an authentication request to the server, and the server obtains the authentication request from the client.
[0120] (2) After receiving the authentication request, the server sends an authentication request response message to the client.
[0121] (3) After receiving the authentication request response message, the client receives the fingerprint image for verification input by the user, obtains the fingerprint template ID corresponding to the fingerprint image for verification, and stores it in the activation record saved by the client. Compare the ID of the fingerprint template, if they match, go to the next step, otherwise an error will be reported.
[0122] For fingerprint verification during the payment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com